NetTools has a number of common features which are used throughout the program. This post provides details on some of these features.
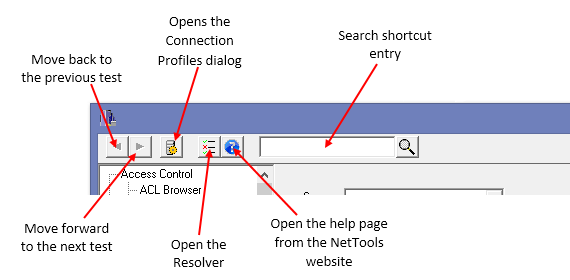
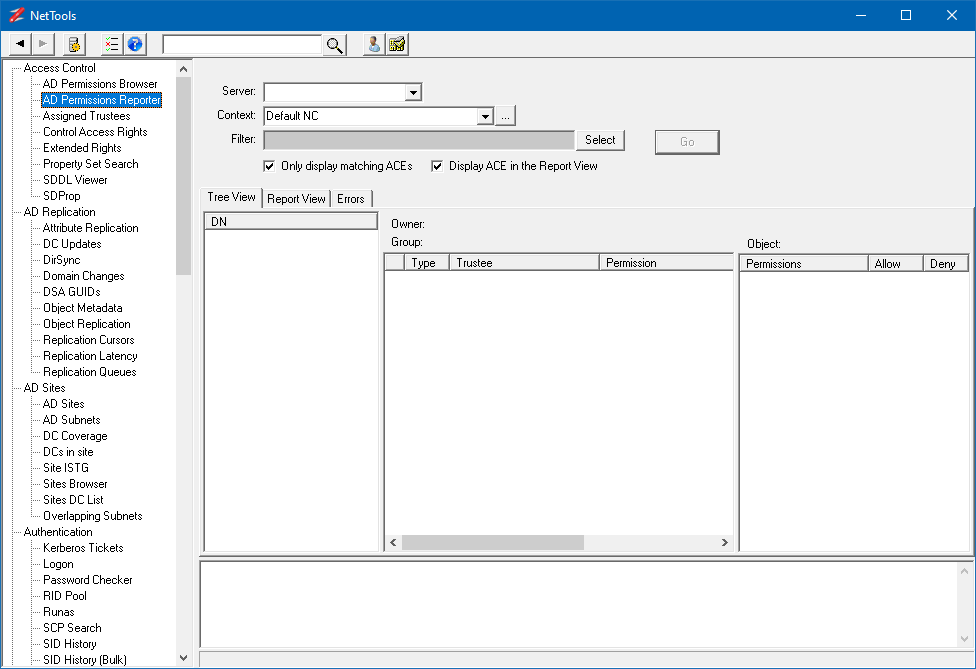
The screenshot below shows the common features of the NetTools interface.
These buttons are used to navigate the tests that have been previously run.
Connection ProfilesThis button opens the Connection Profile dialog used to manage Connection Profiles to connect to specific domain controllers or domains.
ResolverThis button opens the Resolver dialog, which can be used to resolve multiple names and track which objects have been visited.
HelpThis button will open the help page on the NetTools website for the selected test option.
Quick SearchThis option is used as a quick search of the AD, and is a shortcut for the Search option.
Pinned OptionOptions that the user has pinned will be displayed here.
Available TestsThe list of available tests are displayed here. The tests are grouped in categories to help find the appropriate test.
Test OptionsFor each test, the test options are displayed here, use these to configure the test, the associated button is used to start the test.
Result OptionThe results of the tests are displayed in this area. Use the right click context menu to access additional features.
InfoThis area is used to display additional information about the test or error messages that are generated during the test execution.
AD or Server Connections
If NetTools is run on a machine that is joined to an AD domain, by default NetTools will connect to the domain controllers of that domain without needing to specify the server. It will also use the credentials of the user running NetTools to make the connection. If you want to connect to a specific domain controller, different domain, or use a different set of credentials, you use Connection Profiles. See Connection Profiles for more details.
Server Lists
In most of the options there is a field to specify the server or domain, this field is used to enter a server name or select a Connection Profiles that the test will be run against. The server and domain fields are optional, if no entry is provided NetTools will either connect to the domain the machine running NetTools to joined to, or use the default Connection Profile, if one has been defined.
Navigation
The toolbar is used to navigate the tests and access a number of features in NetTools. The toolbar has both fixed buttons and user selected buttons.
The Back and Forward buttons allow you to move backwards and forwards between tests you have used. This is useful if you select a linked option and want to go back to the previous test. The Connection Profiles button opens the Connection Profiles dialog, which allows you to configure profiles that defines the LDAP server, GC server, SSL, authentication, credentials and paging properties. For more details see Connection Profiles. The Resolver button will open the Resolve dialog, which lets you resolve different input types and provides a temporary scratch pad when investigating an issue. For more details see Resolver. The Help button opens the help page on the NetTools.net website for the selected test. The Quick search entry field provides a quick entry method to perform a search of the AD using the User - Search option.
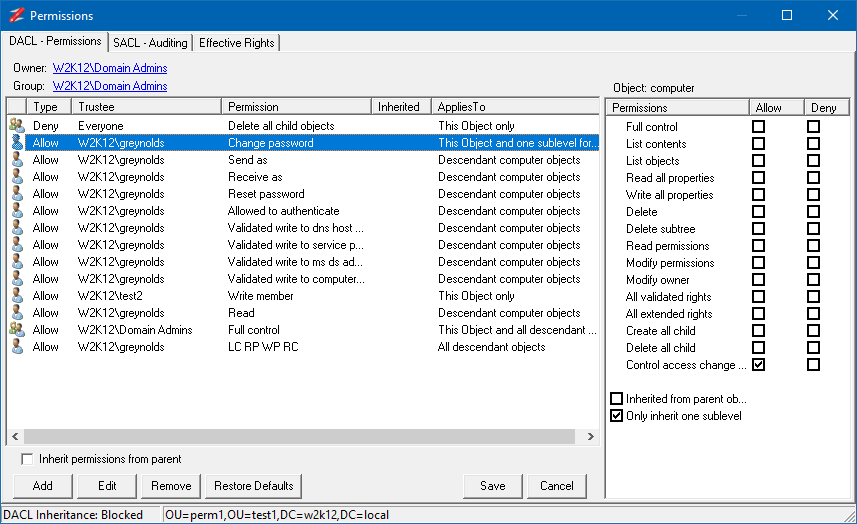
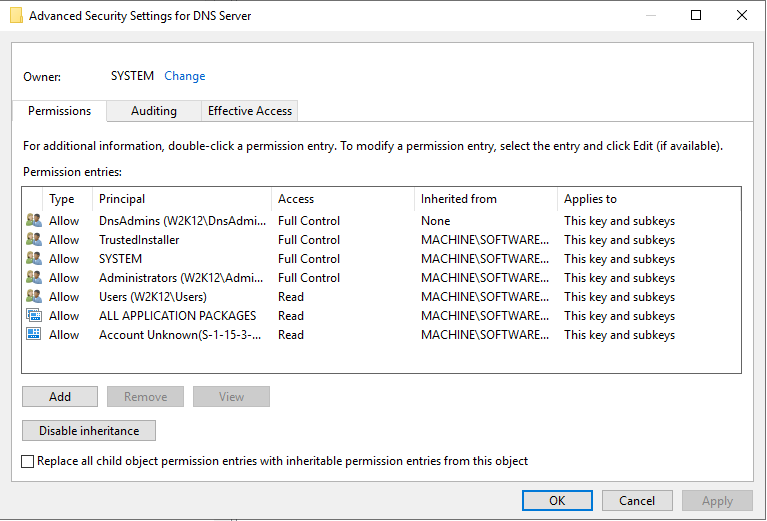
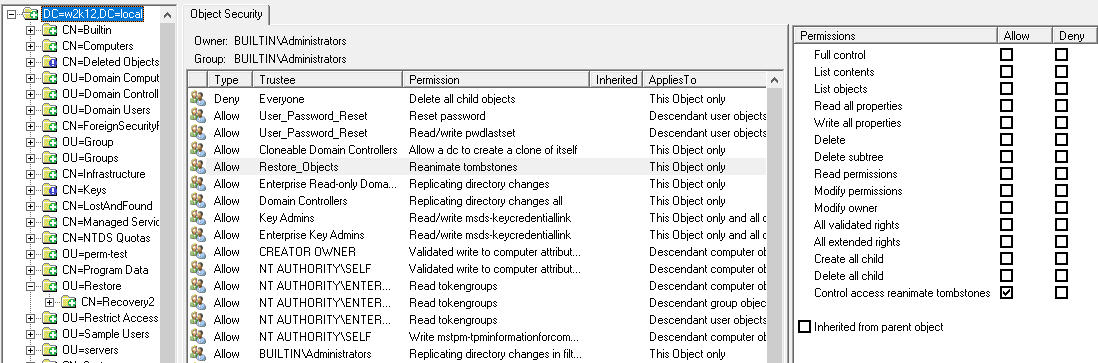
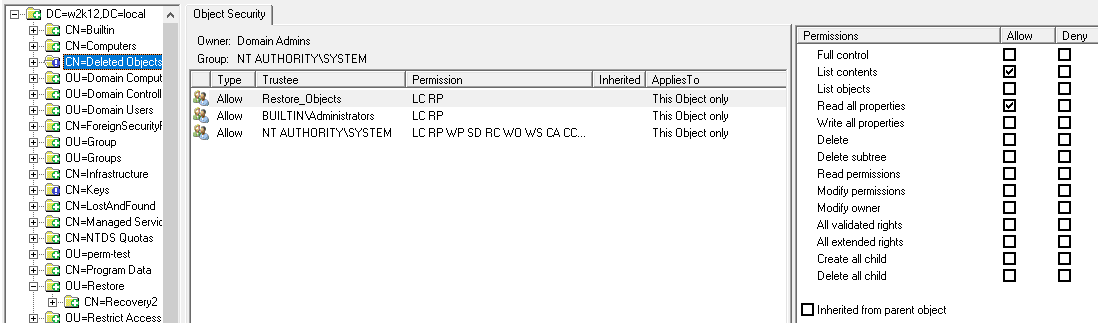
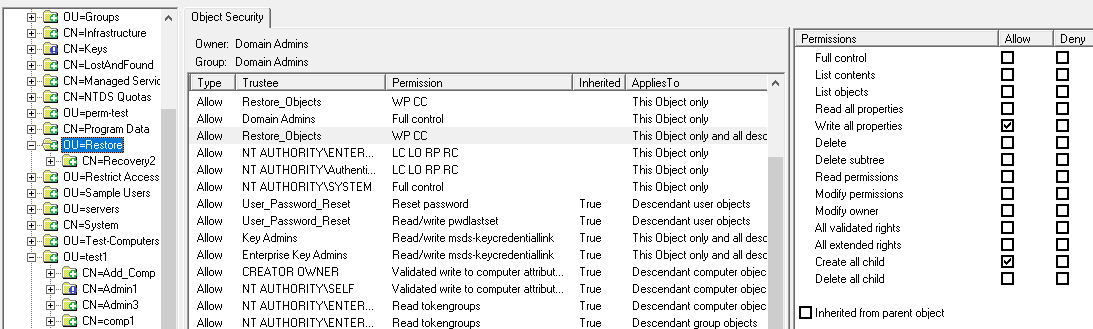
Permissions
You don't need any specific permissions to run NetTools, only execute right on the file system. With a typical AD implementation, a normal user can read a lot of the details in the AD, there are few features that might need elevated rights, i.e. viewing deleted objects or low level replication data shown in the Replication Queues option, where elevated permissions are required this is included in the corresponding Option's web page. Only other scenario where permissions can be an issue is when NetTools is run on a Domain Controller that has User Access Control (UAC) enabled, the results returned by the local Domain Controller will be reduced unless NetTools is executed with Run as Administrator option. In some tests, this might seen be seen as an error 1300 - Not all privileges or groups referenced are assigned to the caller.
Where to start
The number of options in NetTools can make it confusing where to start. The best approach is to start with the Search option under Users or use the quick search option, this allows you to search the AD, be it at the Forest or Domain level for any object in the Active Directory, from there the context menu options allows you to then interrogate the returned objects. See User Search.
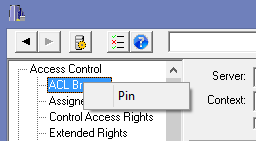
To allow you to find your favorite option quickly, NetTools includes a Pin option, which will add user defined button to the toolbar to allow you to select your commonly used options quickly. To Pin an item, select the option, then right click on the option name and select the Pin from the context menu, you will be prompted to select an icon for the button. To remove a Pinned item, simply right click on the button on the toolbar and select Remove.
Option or test Linking
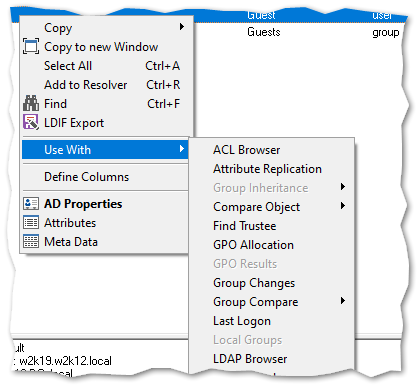
For a number of the tests the output from one can be used as the input for other tests and options, by selecting the corresponding output entry and right clicking the context menu will display these options. The User Search option has a number of linked options that are displayed under the use with sub menu.
Copy and Paste
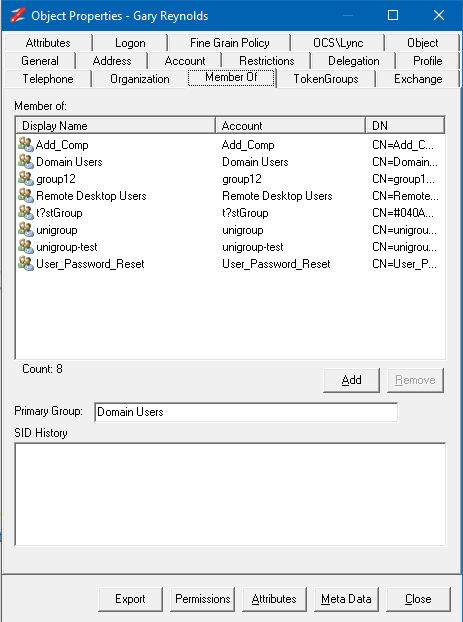
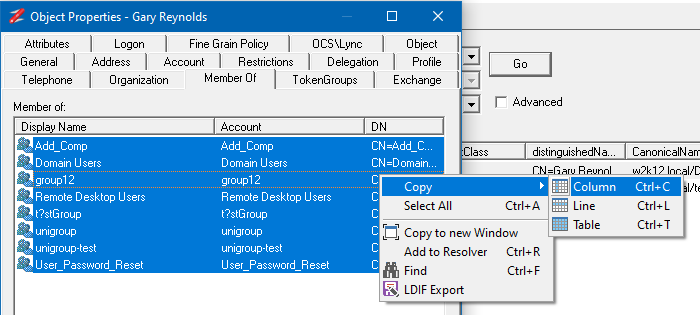
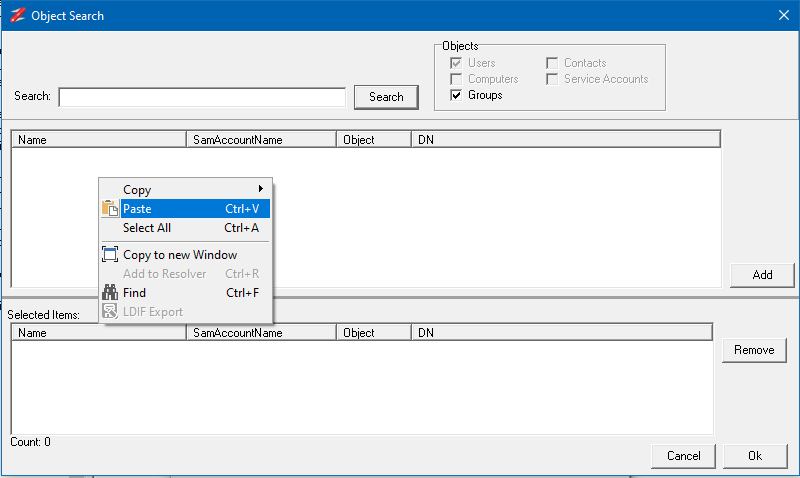
The outputs from the tests can be copied into other functions in NetTools or to external programs. The Copy and Paste options are displayed in the right click context menus. For table views it's possible to copy the data in a single column, the line, or the entire table. When using the copy column option, mouse position when the right click is pressed, is used to define which column will be selected. For text based output fields it's possible to copy the text as with standard copy and paste. The Copy works with a single or multiple selected items, and when copying the details from all selected items is copied. A number of keyboard shortcuts are defined, Ctrl+C will copy the the details of from the column of the select items, Ctrl+L will copy all the details of the selected items, Ctrl+T will copy the entire contents of the table, include headers. The Copy to new window context menu option will copy the contains of the view to a new detached window, which provide additional sort and filtering options. See Copy to new window
Messages/Results pane
On most options, there is a lower pane, this pane is used to display any errors or status report from the execution. Any error messages or codes returned by the APIs are displayed here.
Exporting Objects
There is the ability to export objects in LDIF file format, this is available from the context menus. See LDIF Export for more details.
Common Dialogs
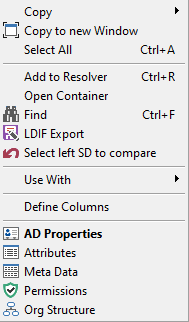
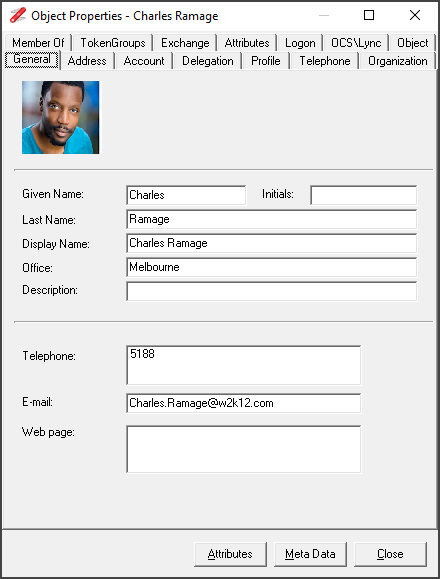
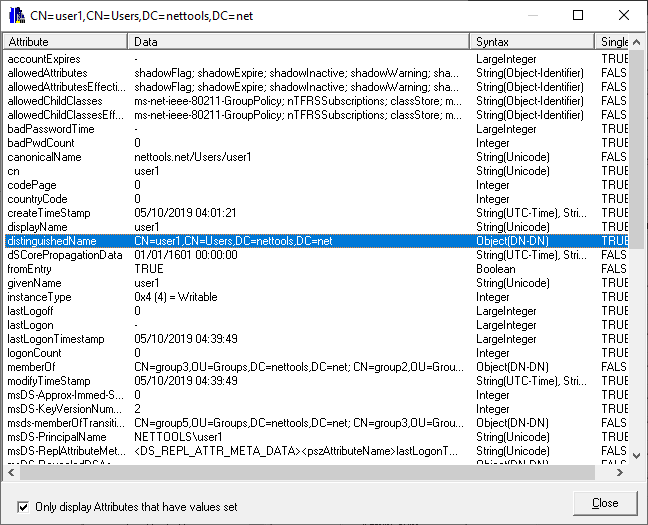
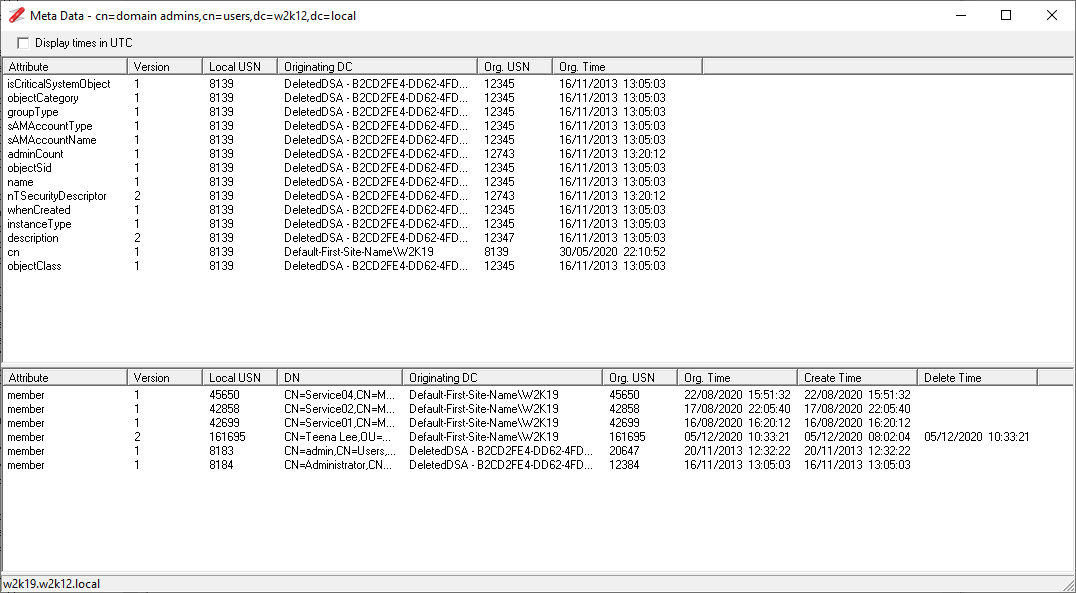
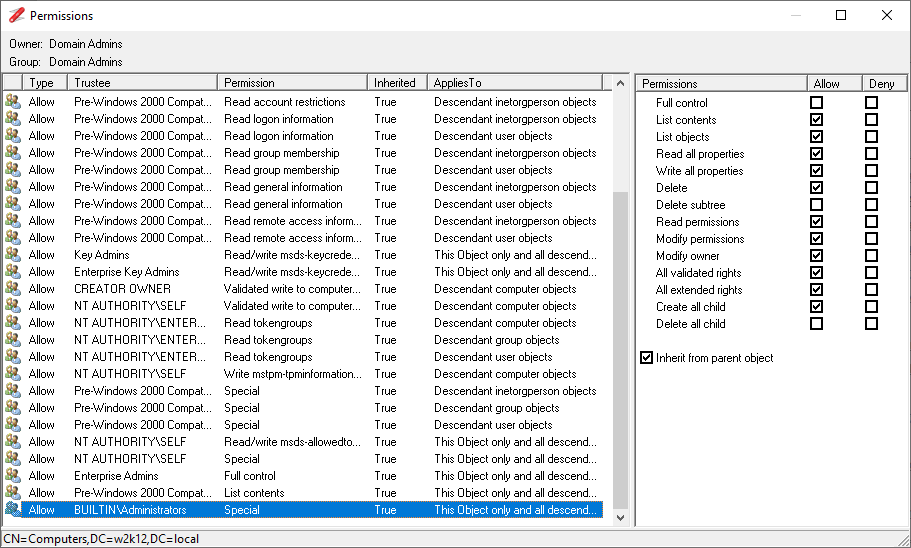
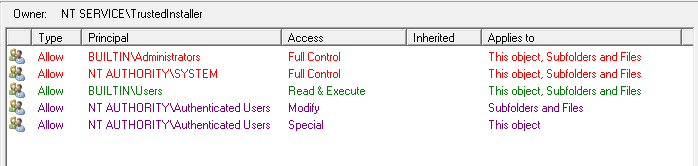
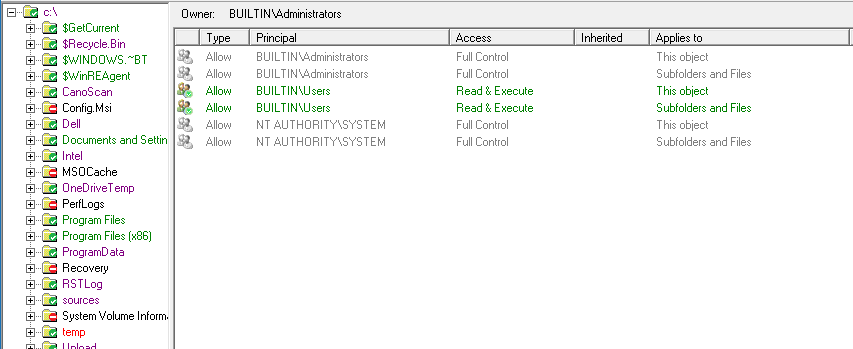
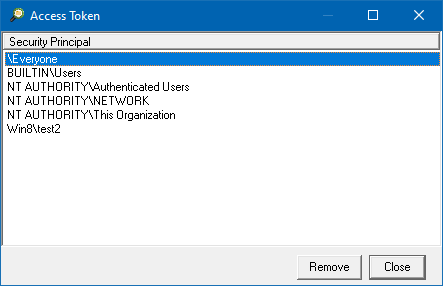
NetTools has four common dialogs which are available from most context menus on in the results and options. These are the AD Properties, Attributes, Meta Data, and Permissions dialogs which is used to display and edit an object's permissions, these dialogs are accessed via the context menu and are listed at the bottom of menu, as shown below.
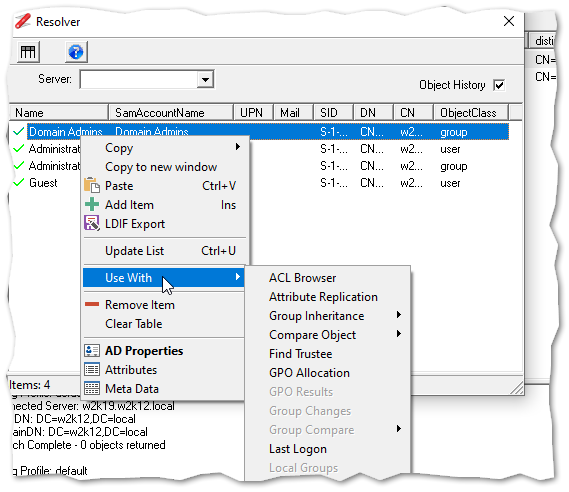
Resolver
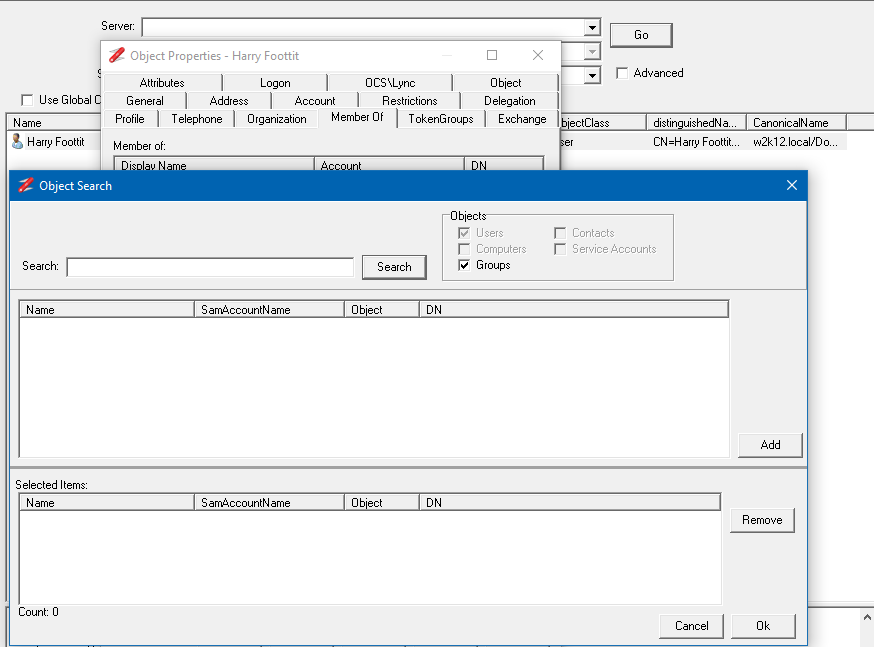
The Resolver dialog provides a scratch pad to temporary store items that you are troubleshooting or investigating. The Resolver dialog is accessed via the toolbar and items can be added to the dialog either from the context menu, pressing Ctrl+R, manual entry, or pasting a list of DN, samaccountname, email, upn or displaynames. From the Resolver dialog the NetTools options and test can be selected from the context menu in the Resolver dialog.
NetTools saved configuration
NetTools uses a single configuration file called NetTools.ini, this is used to save any user defined configuration or lists. NetTools will try to read the configuration from the same location as the exe from executed from.