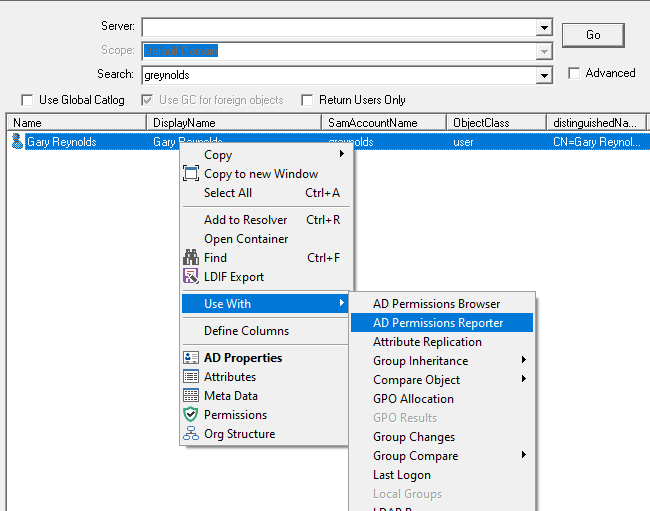
AD Permissions Reporter ![]()
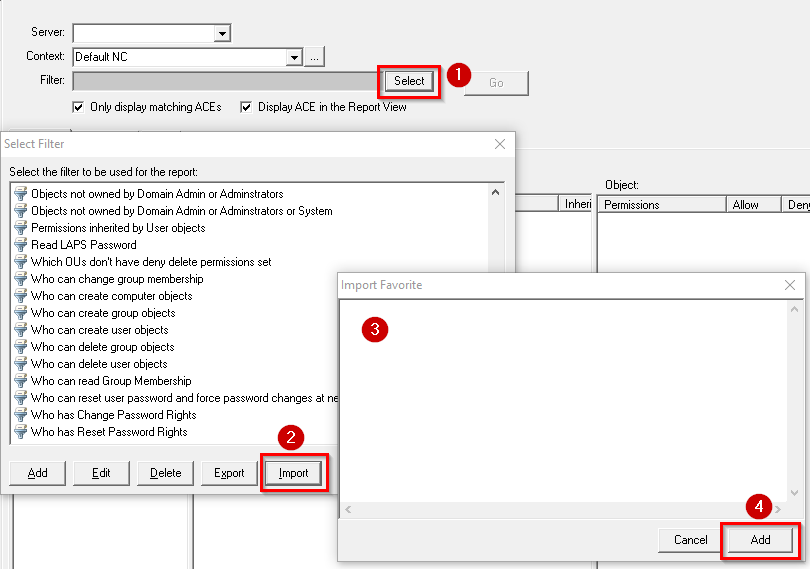
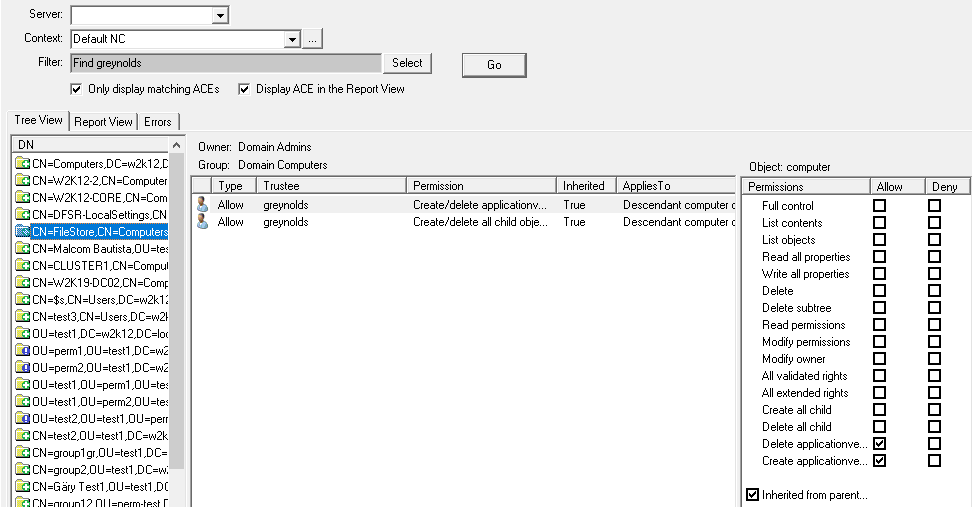
A reporting option to report and search for permissions that have been assigned in the AD, supports both basic and advanced filters. See AD Permissions Reporter.
Certificate Checker ![]()
A new feature to verify the certificate that are assigned to website, including the revocation status, More details available here.
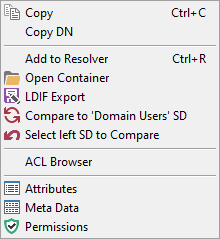
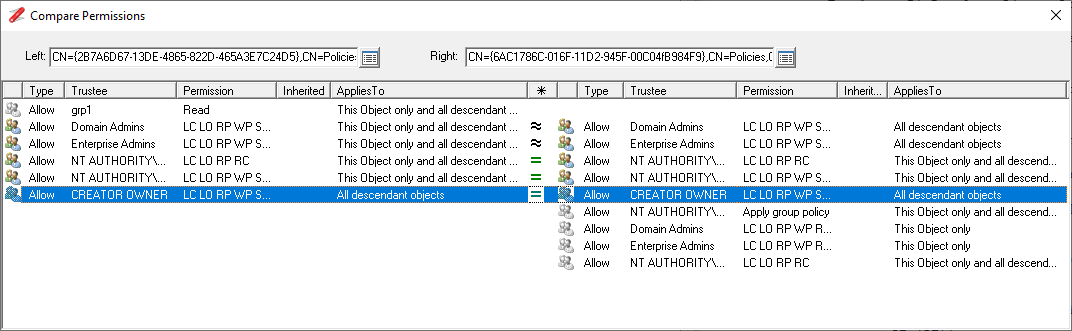
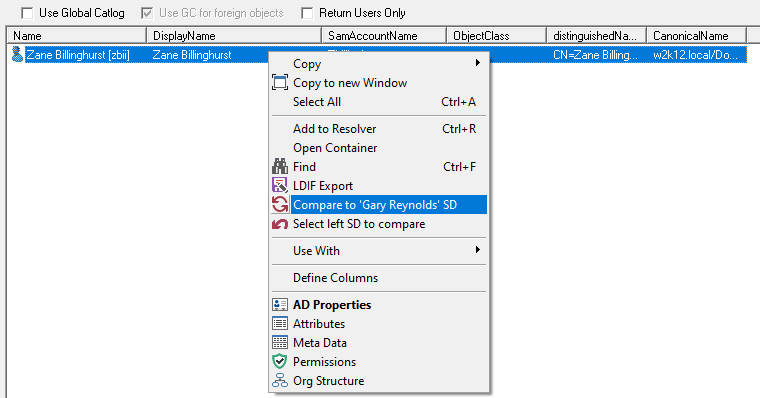
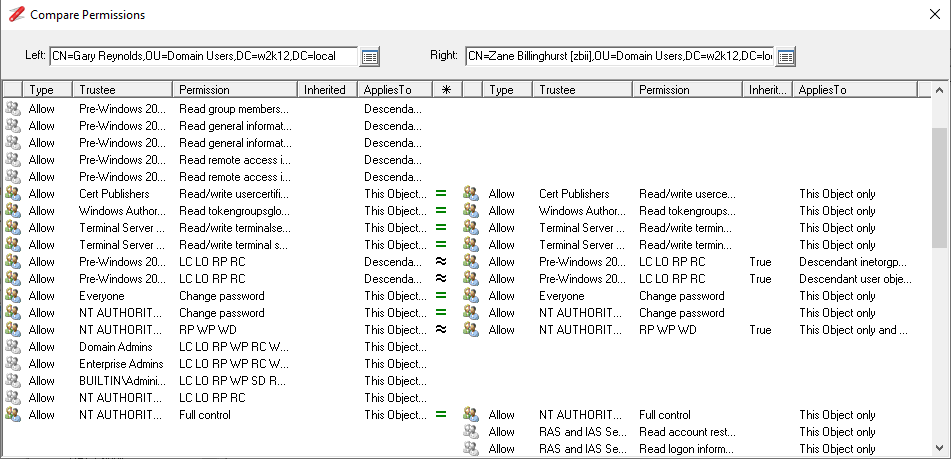
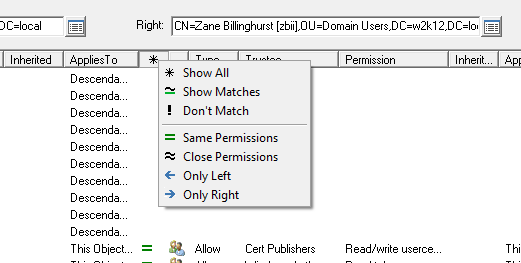
Compare AD Permissions ![]()
Context menu option to compare the permissions of different objects. See How to compare AD permissions.
Object Replication ![]()
A new feature to test if AD objects and their attributes are replicated across the domain controllers in the domain. See Object Replication for more information.
SDDL Viewer ![]()
A new feature to display SDDL strings in the Permissions dialog. More details available here.
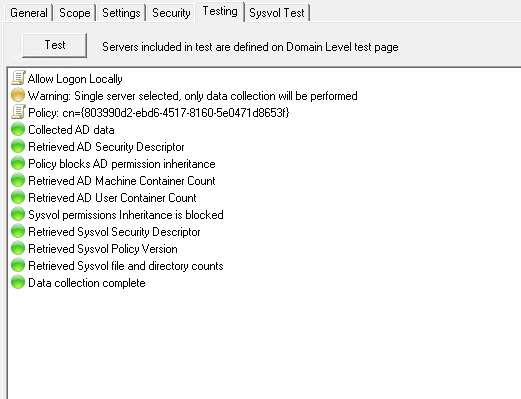
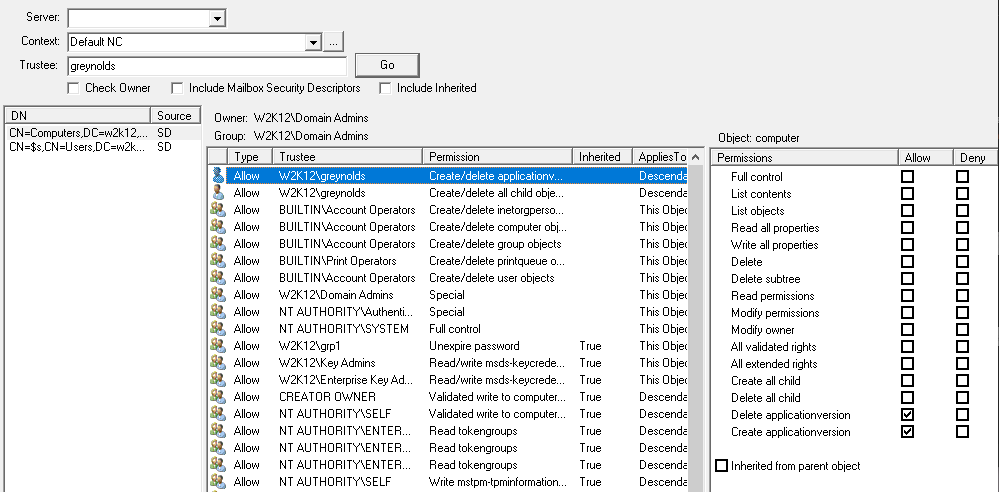
Find Trustee Assignments
Depreciated
AD Permissions Browser
ACL Browser renamed to AD Permissions Browser
Updated context menu to support option to export a permission as a dsacls command.
Updated inheritance text to include no propagation rights details and displayed separately in the rights view.
Changed the icons used in trustee mode to the same as used in AD Permissions Reporter, to make it easier to see which permissions are applies to the trustee.
Fixed index error when assigning the NT Authority\Self to a trustee.
AD Properties
Fixed context menu on delegation tab to allow linked SPN tests.
Fixed memberof bug, some groups are not displayed if the displayname is not set.
Added option to display the time and date when changes to the group membership happened.
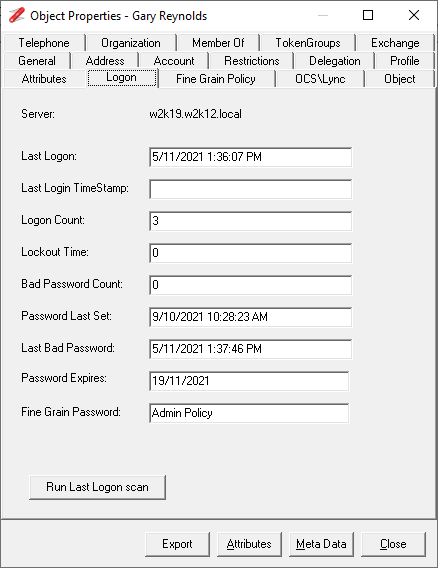
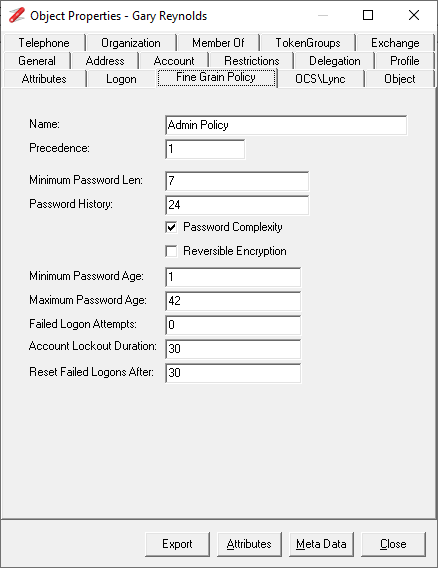
Updated to display the Fine Grain Password details for both users and groups.
Updated Logon tab to include Password Expires based on the msDS-UserPasswordExpiryTimeComputed attribute.
AD Sites
Updated to include a dsBind test to test RPC connection, also updated to support profiles.
AD Subnet
Updated to support IP Addresses with CIDR.
Subnet that are not linked to a site are shown as <not assigned>.
Attributes Dialog
Hex dump - now able to provide hex dump of security descriptor for non-admin users.
Attribute Replication
Updated to display all the attributes of the selected object across the selected domain controllers.
Base64
Updated to support encoding a SID string to binary in Base64 and back to SID String.
DC Resolution
Removed port 3389 from default list of ports, added for testing and shouldn't be there.
Error Messages
Updated to also return error details for WinInet error codes.
GPO Explorer
Added GPO testing functionality similar to that of GPOTool.exe. See How To Test GPOs as GPOTool is no longer available.
Update security tab to include the rights view of the permissions assignment.
Fixed display updates when switching from OU to WMI and back again.
GUID Search
Updated to now search for the entered GUID against common object GUID, and option to search against all GUID attributes found as part of the dynamic attribute discovery.
LDAP Browser
Added button to allow a DN to be opened in a separate window.
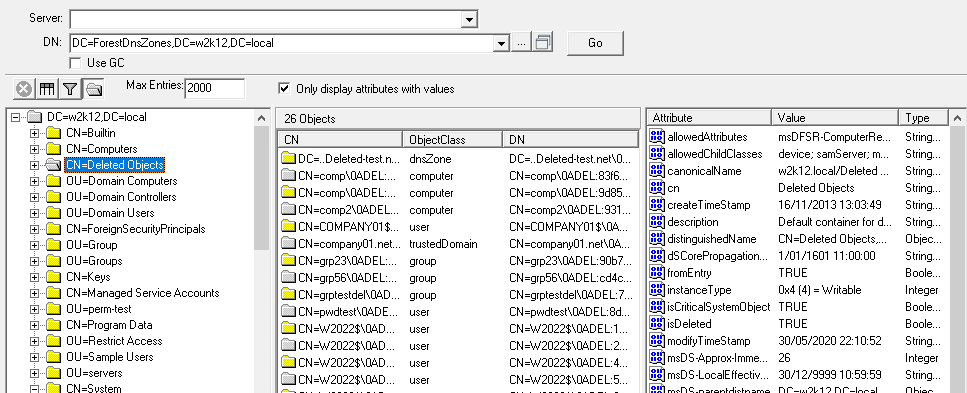
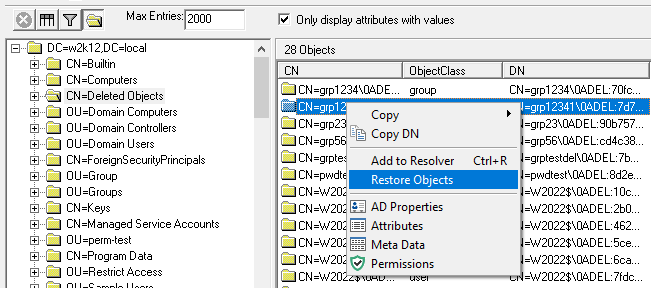
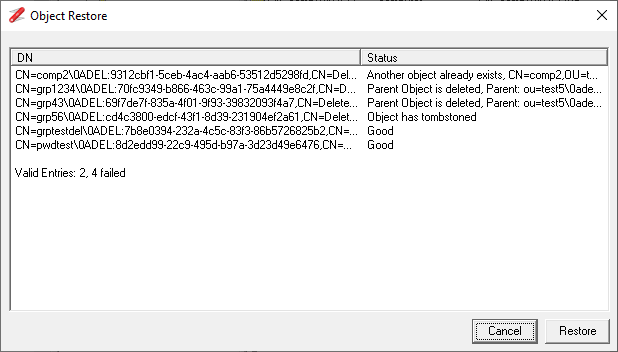
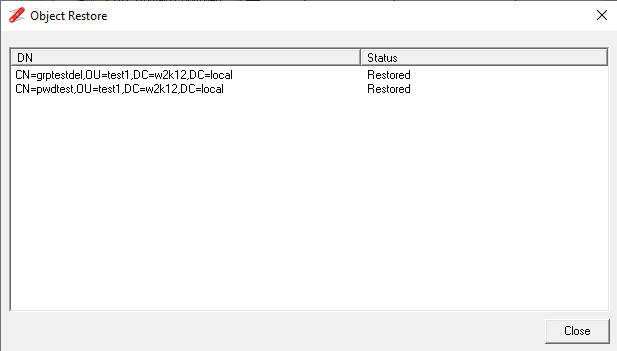
Updated to include a Restore Objects for deleted objects, see How To Restore deleted AD objects.
LDAP Search
Added option to limit the number of records returned. Update Favorite Import to support import of multiple favorite in one go.
Updated the DNSProperty decode to support all data types.
Updated favorites variables to include ##root to specific the root DN of the forest.
Updated to support different Ordering OIDs on the sort field, see Sort for more details.
Certificate verification date format now based on regional settings. When connecting using SSL it will now displays the SSL connection information.
Fixed intermittent exception error that could happen when using meta data attribute types.
Fixed bug in the getdn subst variable that could cause an exception.
LDAP Search Enum dialog - Updated context menu to allow selection of bit operator.
Define the enum DecodesType for GPOptions, ServerState, ForceLogoff.
Set DecodeType for AuditPolicy to DecodeType BIN.
Added DecodeType GMSAPWD.PWD_B and GMSAPWD.PPWD_B to display GMSA password in byte based binary output.
Object Count
Updated to save the count details, with subsequent counts shows the delta between the counts.
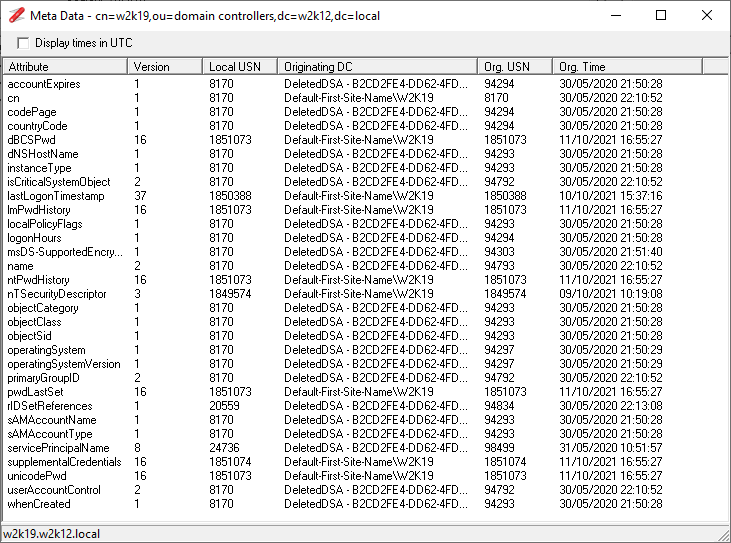
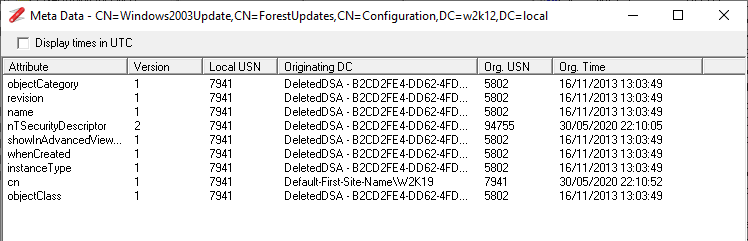
Object MetaData
Updated to also display the value of the value of the attribute and changed time to display local time.
Organization Structure
Fixed exception that can occur when multiple Left SD menu item selected.
Added additional logic to detect circular references.
Added an extra context menu item to display a separate window with the org structure.
Ping
Added option to specify the ICMP packet size used for the ping.
Permissions dialog
Added additional caching at the profile level to improve performance and reduce data requests. Also improves the performance of AD Permissions Browser, and GPO explorer.
Added Inheritance details to the status bar.
Resolver
Updated test options so any entry is added to the resolver history.
Fixed columns update so blank attributes are shown correctly.
Schema Version
Updated to support Exchange 2019 CU11, CU12 & 2016 CU22, CU23.
SDProp
Updated to include support Service Managed Accounts and improved performance.
SID Converter
Updated to include icons for resolved names and now if a SID is not found, it will now check if the domain SID exists to confirm if the SID has been deleted or the domain is invalid.
Site Browser
Updated to displays bridgehead servers in the site settings view.
Added addition error reporting for Validate function and added DsBind test.
Subnets that are not linked to a site are shown as <not assigned>.
Token Size
Updated the connection to use the GC to correctly resolve cross forest groups and fixed bug were multiple entries in SIDHistory caused the token size to be calculated incorrect.
User Search
Fixed bug where from a child domain, the Use GC option didn't use the root of the forest for the search.
User Search dialog
Updated so if only one user account found and it matches the search, it automatically returns the single entry.
Predefined Queues
The follow queues have been updated:
AD: Invalid Pwd Change (All users)
AD: Invalid Pwd Change (Nominated user)
AD: List gMSA Accounts
AD: List MSA Accounts
AD: Restore Deleted User
AD: RootDSE Modify - Dump Database
Users: Invalid characters for O365
Users: Mail and UserPrincipalName different