AD Permissions Editor ![]()
Updated AD Permissions dialog to provide the ability to edit the permissions of an object. The edit option can be used in conjunction with the Effective Rights tab to model permission changes. See Permissions Dialog or How to edit an AD object's permissions.
Reports ![]()
This option is used to display the direct and indirect reports under the nominated User. See Reports
General
Added UAC detection at startup and warn if a restricted token is detected when running on a DC, as sthe DC may not return some data due to the restricted token. Replaced all instances of strcpy with strncpy to help prevent memory overflows. Better support has been added for Unicode characters not included in the current code page. For DNs that contain a Unicode character, the DN will be encoded as # hexstring, i.e. CN=#04044761C48D,DC=w2k12,DC=local.
AD Effective Permissions
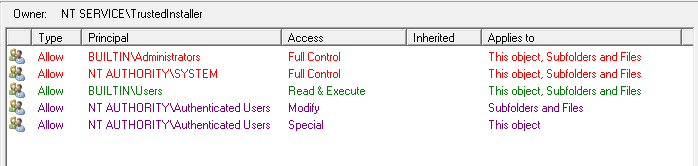
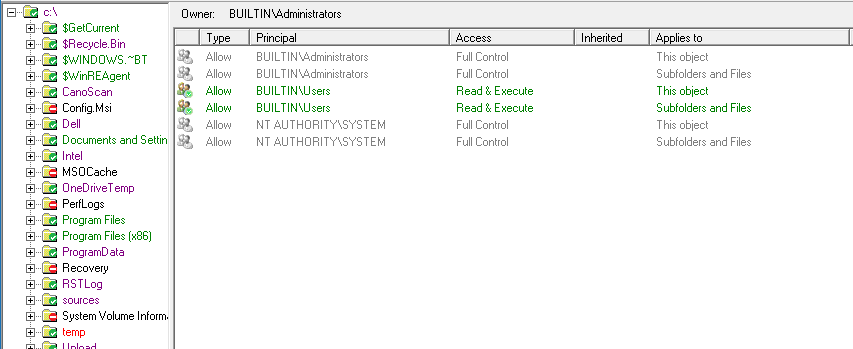
A new capability has been added to the AD Permissions Browser and the Permissions dialog to show the Effective Permissions. In AD Permissions Browser, the Effective Permissions are shown while browsing the AD. See AD Effective Permissions for more details.
AD Permissions Browser
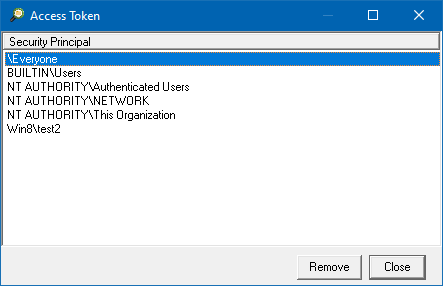
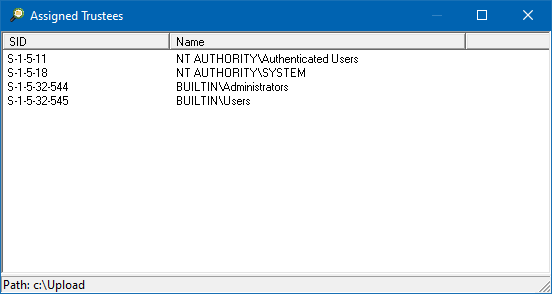
The trustee option was updated to automatically add Pre-Windows 2000 Compatible Access group based on the group membership.
Added option to export permissions.
Permissions are now colour-coded to reflect the permissions that have been granted.
Updated the Trustee option to include a pre-Windows 2000-compatible access group to the access token.
Updated Trustee select to display the object search dialog if the User is not found.
Updated the ACE flags to provide more details of the ACE.
Fixed bug where list contents are not cleared when switching between permissions tabs.
Fixed intermittent error when switching between DACL and Default Security permissions for Schema objects.
Additional caching has been added to improve performance when switching between permission types on the same object.
AD Permissions Reporter
Added option to include Authentication group.
Fixed new rule defaulting the scope selection.
Permissions Dialog
Updated trustee selection to include the option to use the current User's access token.
Added the Effective Rights tab to display the Effective Permissions of the selected trustee. See Permissions dialog
Updated to include SACL permissions
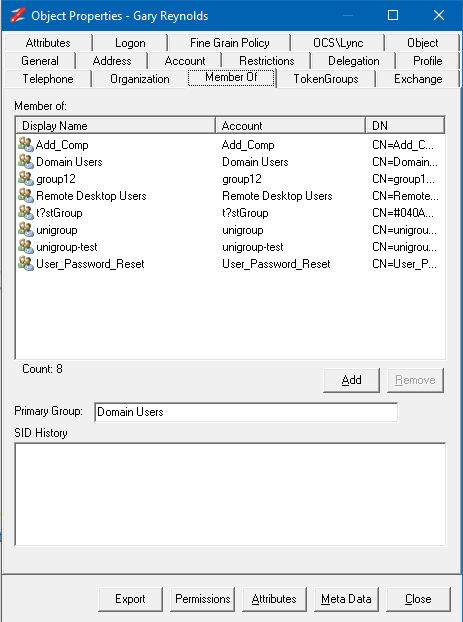
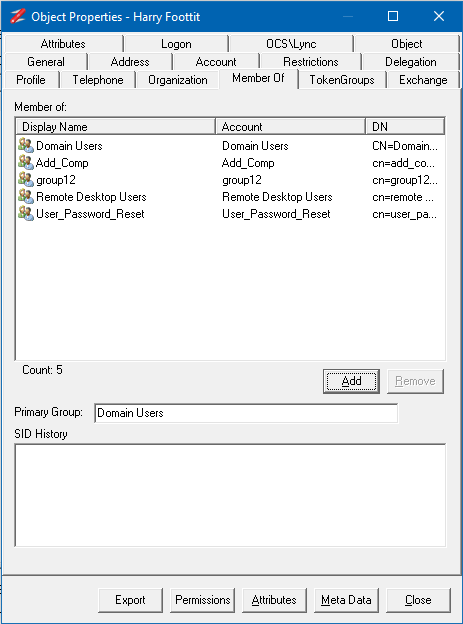
AD Properties Dialog
Updated LAPS tab to support both LAPS v1 and v2.
Update the function of Absolute checkbox to refresh the TokenGroup list when changed.
The account option is updated to show the status of the User who cannot change their password based on the object permissions.
Added a Permissions button to the dialog.
Updated the TokenGroup tab so it doesn't refresh each time it's selected.
TokenGroups now uses the Profile cache to improve name resolution performance over slow links.
Updated to handle attributes that can't be resolved or displayed correctly, due to Unicode characters.
Updated to support Unicode DN in DN-DN attributes - member, memberof, manager, direct reports
Added extra field on Objects tab to display UTF-8 encoded DN, is displayed for DNs that contain Unicode characters
Connection Profiles
Added option to specify the LDAP Protocol Version to be used for the profile. The default is Version 3.
DC Resolution
Updated LDAP and DS binds to use the connection profiles.
DirSync
Updated the cookie functionality so show changes if the cookie is subsequentially used.
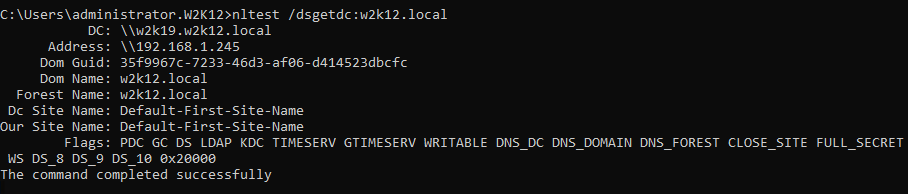
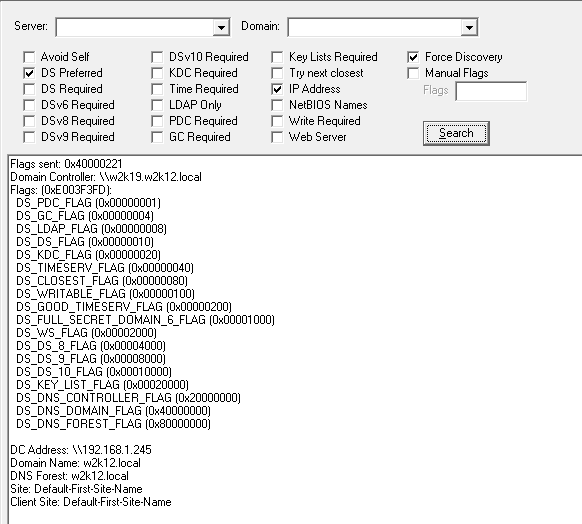
DsGetDcName
Added additional options for Windows 2022 and an Advanced View to show the associated API constants for the options. Also updated the output to display the details of the flags passed to the API.
Error Messages
Updated LDAP Error messages to also return the Windows equivalent error message.
Export Permissions
added the option to export the permissions of objects from AD Permissions Browser and Permissions dialog
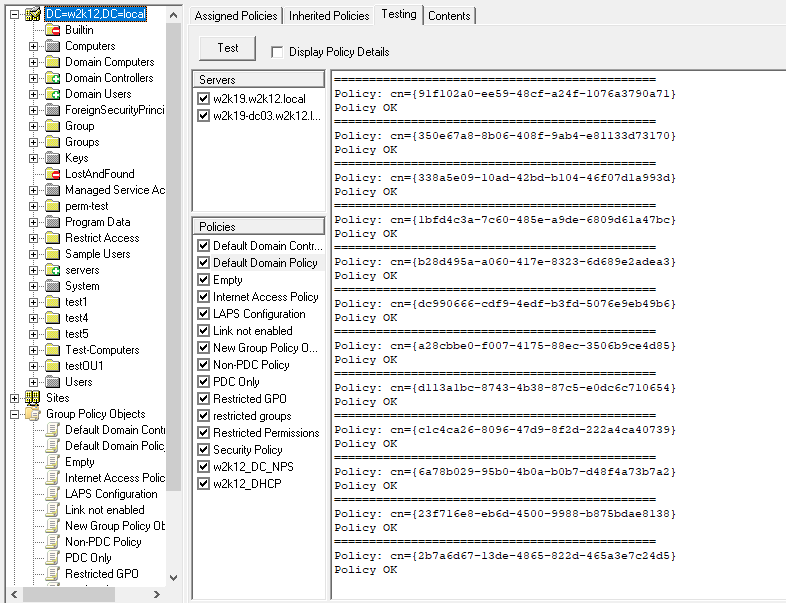
GPO Explorer
Updated the context menu so the Edit GPO option is available in the tree view and GPO list views.
Updating testing to show the results of the data capture phase if a single server is selected.
Updated the GPO list view to include who has been assigned the Apply GPO right.
Additional tabs were added on the Group Policy Object view to display the Policies and Default GPO permissions.
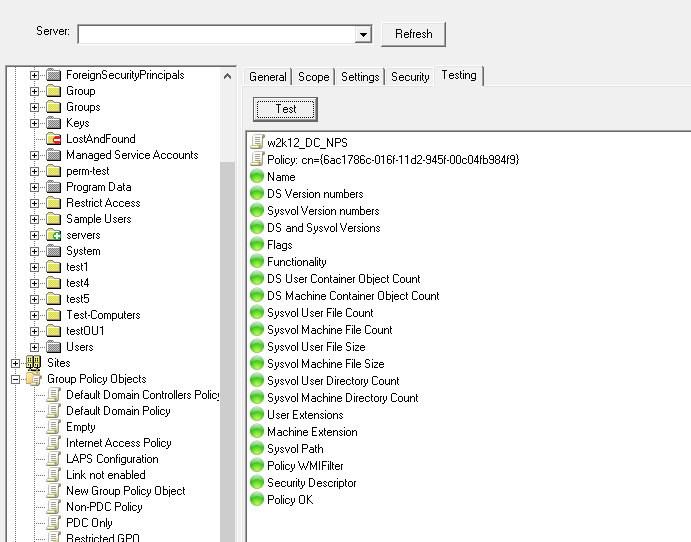
GPO Test, Updated logic so if sysvol is inaccessible then all sysvol tests reflect the failure.
Fixed an intermittent exception error on the Domain based GPO tests.
Update the tests to include additional testing of the permissions on both AD and Sysvol, and checks that the sysvol permissions are the same across all DCs
Added additional Sysvol test on individual GPO details to test and report on file permissions.
Added option to open and view the settings in registry.pol files.
Group Compare
Added a new membership compare option of Member Recursive, which will compare the membership of a group and all nested groups.
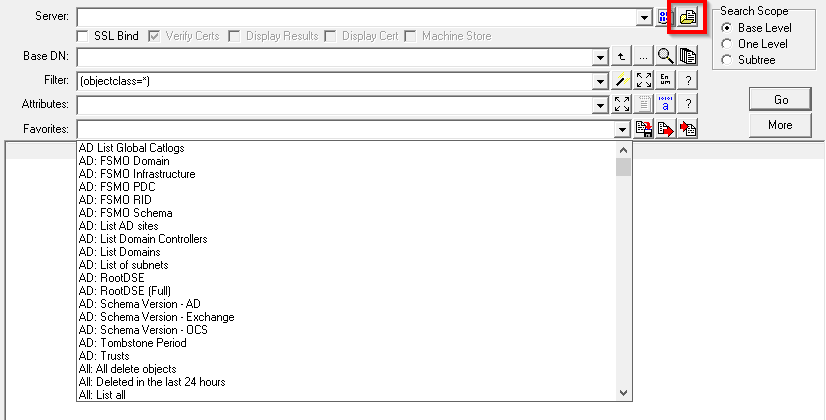
LDAP Browser
Fixed bug where user-selected decode types are not honoured.
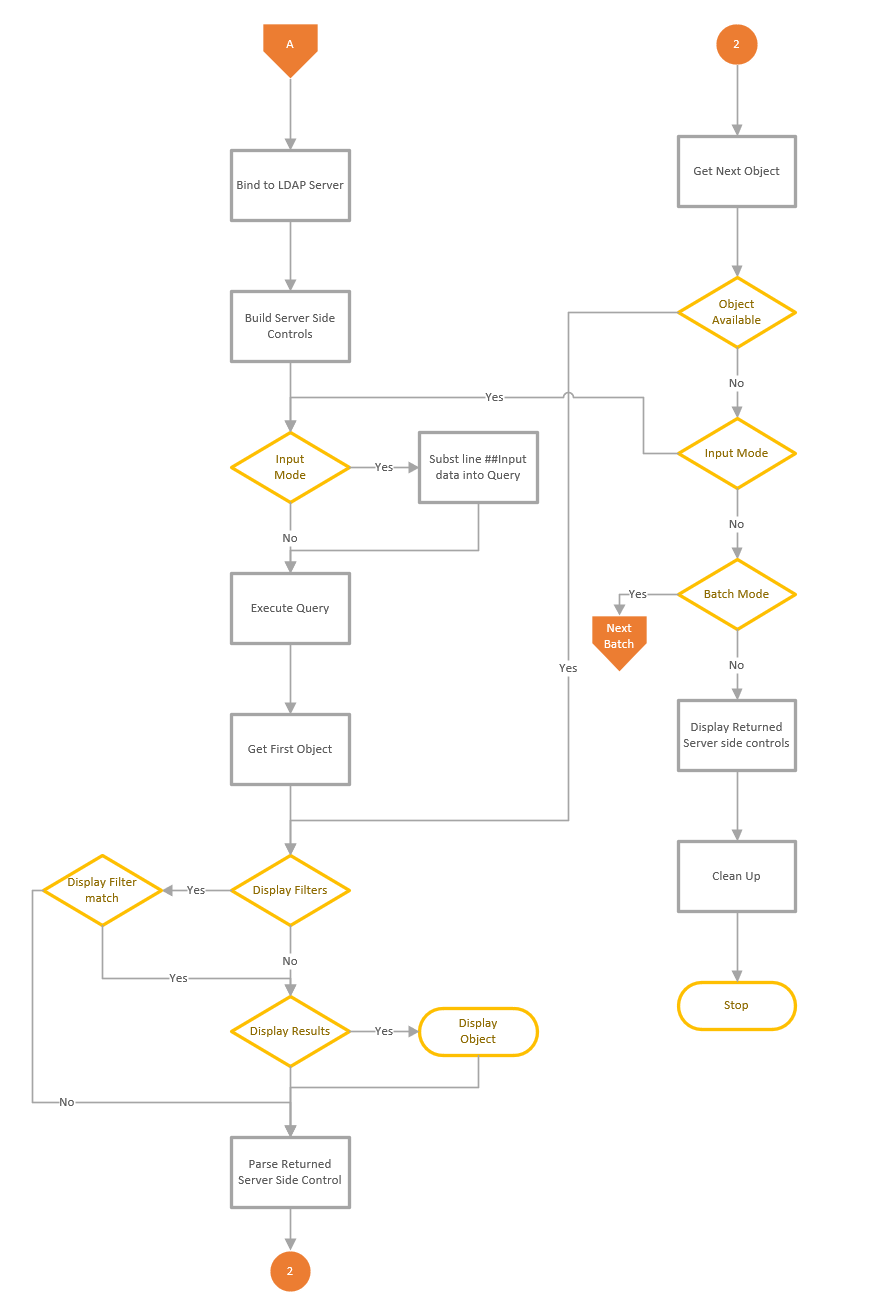
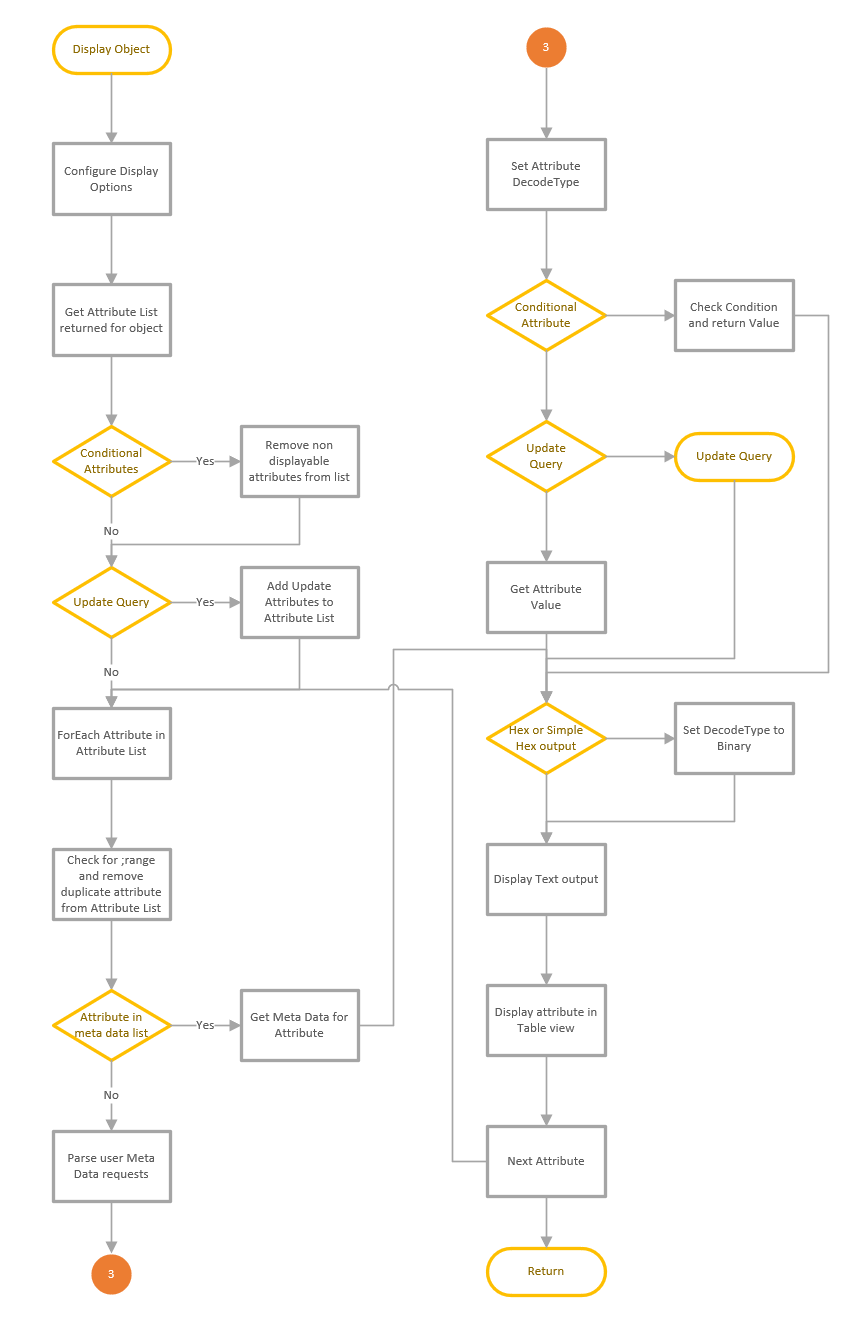
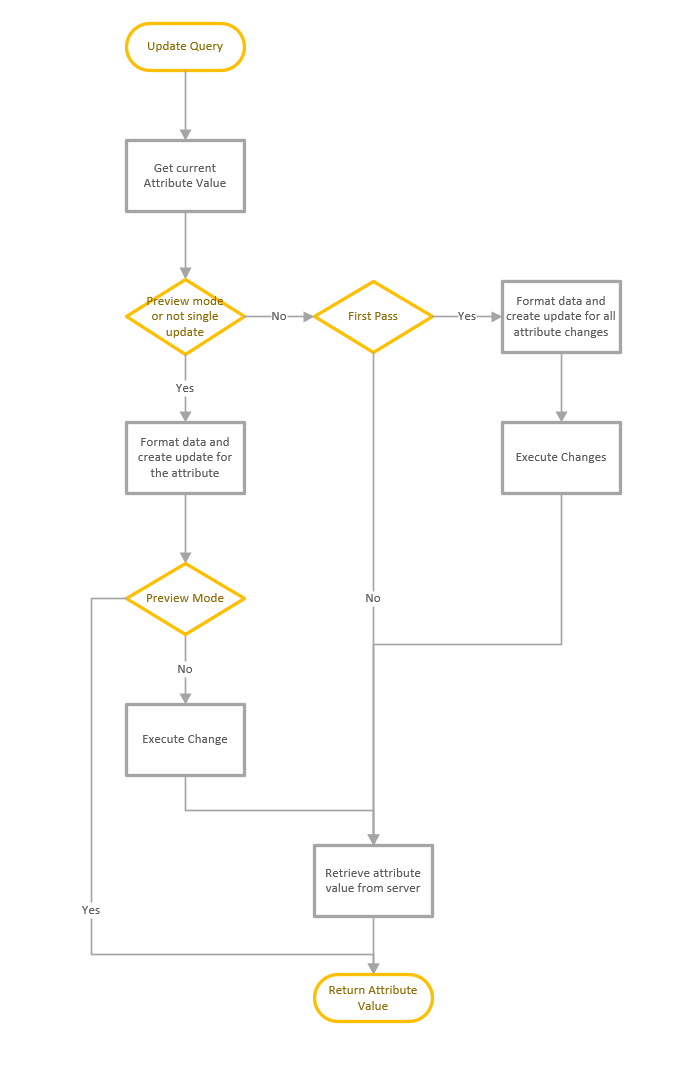
LDAP Search
Updated the Manage Control dialog to allow the selection of Sequence encapsulated of the value, to provide better support for other control types. See details here
Fixed bug that could cause an exception when multiple Date meta data decodes are used
Added metav attribute decode for value based replication details contained in the msds-msDS-ReplValueMetaData attribute.
Added decode for UTCTime and change dynamic decode to select UTCTime for OID 2.5.5.11 and OMSyntax = 23.
Meta Data Dialog
Updated to support F5 refresh option
Object Count
Updated to support GC connections so the count can be completed across the entire forest.
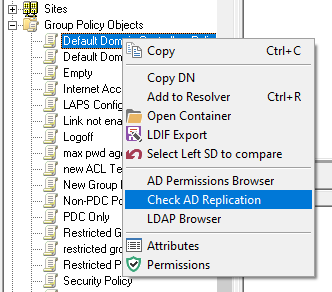
Object Replication
Added context menu option called Move to Top as the first DC in the list is used as the source DC to compare the other DC against.
Organization Dialog
updated to include Organisation Structure in the context menu
Ping
Updated context menus to disable change option when tests are running.
Schema Versions
Updated to support LAPS v2, Exchange 2019 CU13.
Search
The Use With context menu updated to include an option to select Effective Permissions
Time Converter
Updated to support hex-based 64 bit time entries, i.e 0x1d99bfe7fb26dbd