This software is Freeware. You use this software at your own risk. I do not warrant this software to be fit for any purpose, and I cannot be held accountable for any form of data loss that occurs as a result of using this program; you use it at your own risk.
Current Version: v1.9.4
Overview
ACLViewer provides a quick and straightforward way to browse the Windows file permissions assigned to a folder structure. It can also determine if a user can access a specified folder structure. ACLViewer uses the Windows User Rights\Privileges to enable the browsing and viewing of the permissions set on the file system. The folder structure can be browsed irrespective of the permissions that have been assigned on the file system, as long as the user is a member of the local administrators group with the Backup rights assigned.
Features
-
-
-
- It can be used to view local or remote folder structures
- Familiar Windows Explorer style interface
- Provides a graphical representation of the permissions inheritance in the file structure
- Provides a graphical representation of the folders that a selected trustee can access
- Perform recursive searches of a folder structure to identify any sub-folders that do not inherit permissions
- Two modes of use - Permissions Mode and Trustee Mode
- Display the trustees that have permissions assigned in a path
-
-
Interface
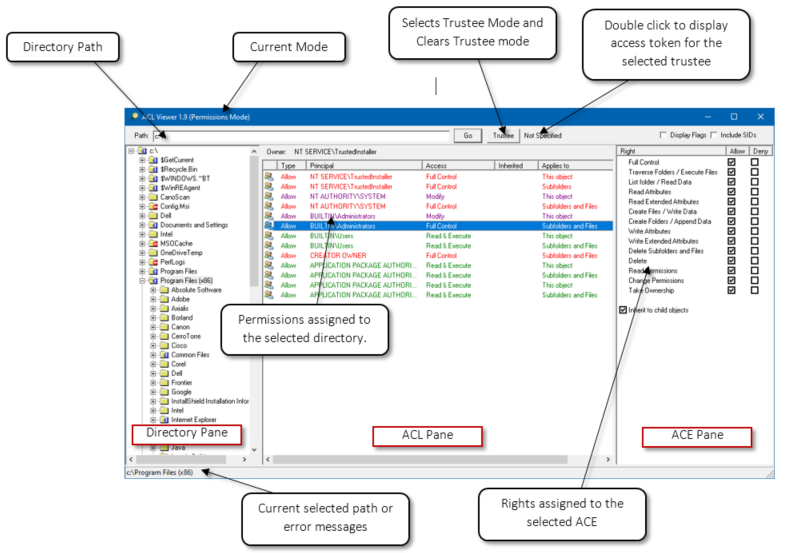
The picture below shows the elements of the user interface
If the program is run without administrator rights or the user context does not have the Backup user right, the following error message is displayed on the status bar at the bottom of the screen when the program starts.
Mode of Use
When using ACLViewer, the program must be run with Run As Administrator permissions, or some folders and ACLs may be inaccessible.
Enter the path in the Path field, this can be a local drive or a network share and click Go, and the directory structure will be displayed in the Directory pane. The permissions assigned to the folder are shown in the ACL pane by clicking on a folder. By clicking on one of the individual ACEs in the ACL pane, the rights assigned to that ACE are displayed in the ACE pane.
Context Menu
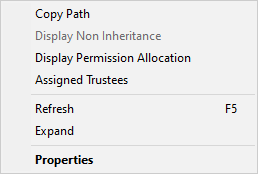
The directory pane has a context menu that provides several additional options.
Copy Path - copies the path of the currently selected folder to the clipboard
Display Blocked Inheritance - this option is only available in Permissions Mode. When selected, it will enumerate all subfolders of the selected folder and expand and display any folders that don't inherit permissions from the parent folder. This feature is useful when trying to find any subfolders that will not inherit changes made that are assigned to folders higher up the tree.
Display Permission Allocation - this option is only displayed in Trustee Mode (TM); it will expand the folder structure showing the folders that the trustee has permissions assigned.
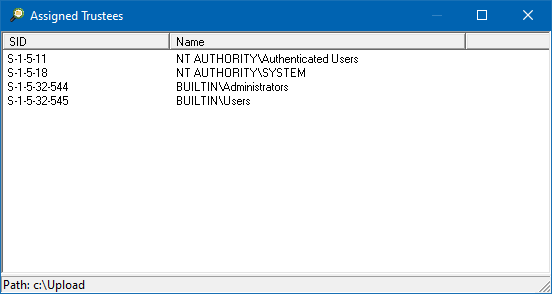
Assigned Trustees - will display all the trustees that have been assigned permissions in the selected path
Expand - will expand all the child folders under the currently selected folder
Properties - Display the Windows Explorer file properties dialog for the currently selected folder
The Assigned Trustees option will scan the select folder for all the trustees that have been assigned permissions in the path. This is useful when migrating servers to a different domain, and you want to know which groups are being used to access the folder structure, so they can be migrated as well. The option will display all the trustees that have been assigned permissions.
Permissions Mode (PM)
Permissions mode lets you view what permissions are assigned and inherited down the file structure. Permissions Mode is selected by default when the program is started. Enter the path and click Go; the directory pane will display the specified folder, and the user can browse the directory structure. If there is an issue accessing the specified path, the corresponding error will be displayed in the bottom status bar. The inheritance of permissions down the folder structure is represented by the icons used in the Directory pane; see the Icons section for the meanings.
While Permissions Mode is used to browse the folder structures, it can also be used to view the permissions on individual files. However, you cannot browse files; you have to specify the full path of the file in the Path field.
The permissions listed in the ACL pane are colour coding based on the permissions that have been assigned: Red = Full Control, Purple = change Permissions, and Green = Read permissions.
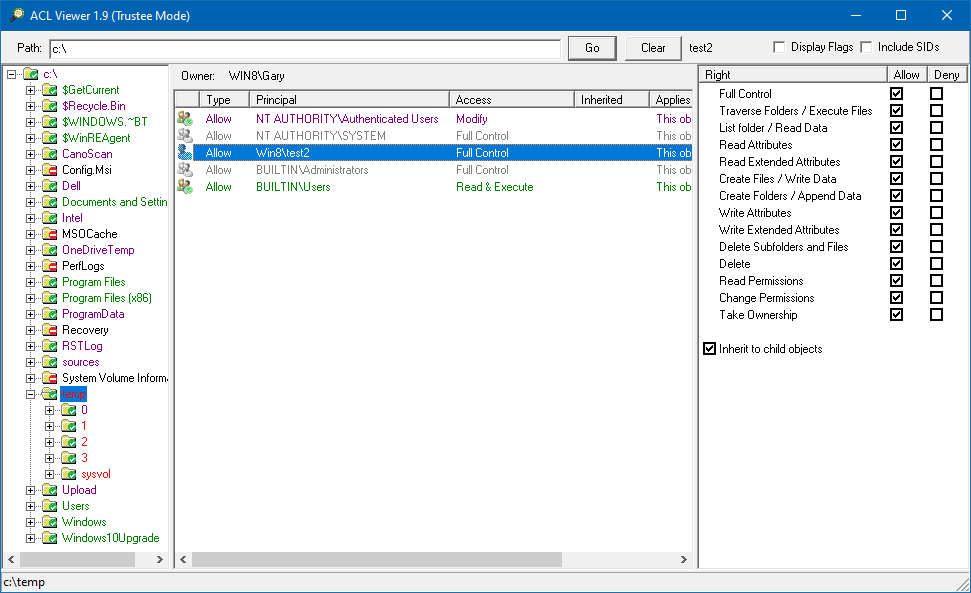
Trustee Mode (TM)
The Trustee mode allows you to select a trustee (user, group, or computer), and then the Directory pane will indicate if the chosen trustee has permissions assigned to the folder. Trustee Mode may not be 100% representative of the trustee’s access rights, as the trustee may receive more or different privileges based on how the trustee accesses the folder. Also, the permissions on a share may block the trustee’s access.
ACLViewer doesn't use the user's account to check if access is available. Instead, it builds an access token with the list of groups the trustee is a member of. Then ACLViewer uses this generated access token to check if corresponding ACEs are assigned to the folder relevant to the trustee. The list of groups in the generated access token is derived by querying the AD for the trustee's TokenGroups attribute, which contains all the trustee's AD group memberships. The well-known SID is also added to the generated access token based on the selected configuration options. It will then query the local groups of the selected computer to determine if the trustee has any local groups assigned, which will be added to the generated access token.
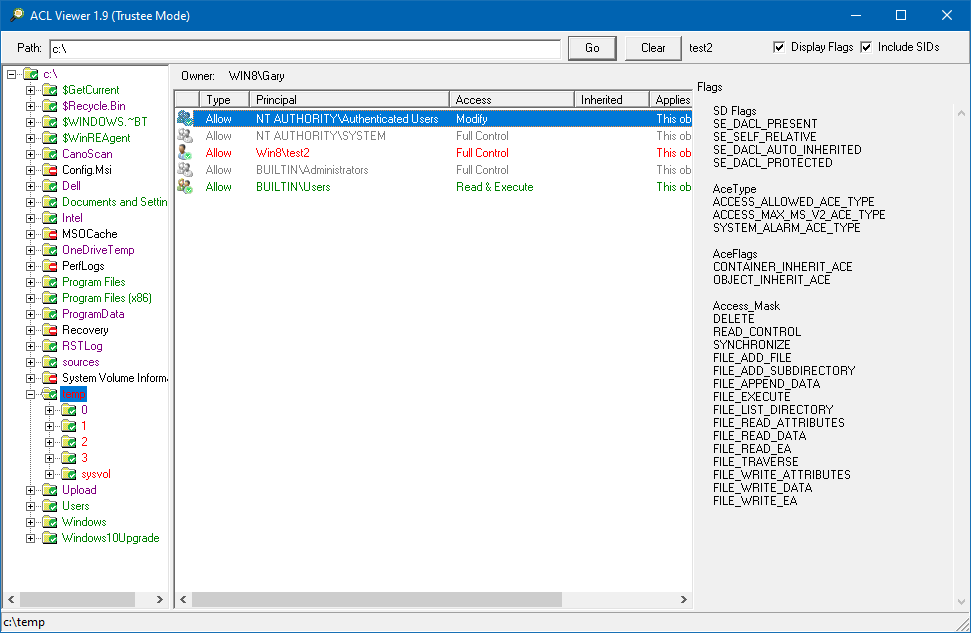
You can view the SIDs in the generated access token by double-clicking on the trustee name next to the Trustee button.
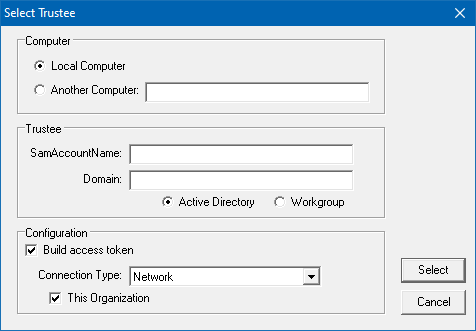
To select Trustee Mode, click on the Trustee button, and the following dialog will be displayed:
The Computer section provides the ability to select the local computer or a remote computer; if the remote computer option is selected, the local group on the selected computer will determine the trustee's group membership.
The Trustee section lets you select the user, group, or computer. You can choose if the trustee is searched for in the Active Directory or local workgroup. If the domain is not specified, the current domain of the machine running ACLViewer is used.
In the Configuration section, when the Build access token option is selected, it lets you choose the access method the user will use to access the specified path; this defines which additional Well-Known SID will be added to the trustee's generated access token. The Connection Type has the following options:
Network
Terminal Server (RDP)
Interactive
Batch
Service
Dialup
When the directory structure is browsed, the trustee's generated access token is used to check if one of the entries provides the trustee with access to the folder. The folder icon will signify if the ACL has an ACE associated with the trustee; see the Icon section for details on their meanings. The icon represents if the user has rights; it doesn't differentiate what access the user has, i.e. read, write or full control; you need to check the permissions assigned to the folder to determine the user's level of access.
In Trustee Mode the names of the folders are also colour coded to represent the permissions the trustee has on the folder: Red = Full Control, Purple = change permissions, and Green = Read permissions.
When the ACL is displayed, any ACEs that match an entry in the trustee list of groups the icon has a green tick. The ones that don't match are grayed out. You can then review what permissions the trustee will be granted or denied on the folder.
To return to Permissions Mode, click on the Clear button.
This is a screenshot of the Trustee Mode:
Icons
The table below shows the meaning of the icons that are used in ACLViewer, PM and TM signifies in which mode the icon is used.
This software is Freeware. You use this software at your own risk. I do not warrant this software to be fit for any purpose, and I cannot be held accountable for any form of data loss that occurs as a result of using this program, you use it at your own risk.