If you manage an AD environment, understanding who can reset the password of an account that is a member of domain admins is critical to the security of your environment. A Domain Admins accounts hold the keys to your AD, if one of these accounts gets compromised and used by a bad actor, it's going to be a bad day at the office.
In this post we will look at how we can use NetTools to report on who can reset the password of your Domain Admin accounts. This information can be used to identify potential security issues that might need to be addressed to increase the security posture of your environment.
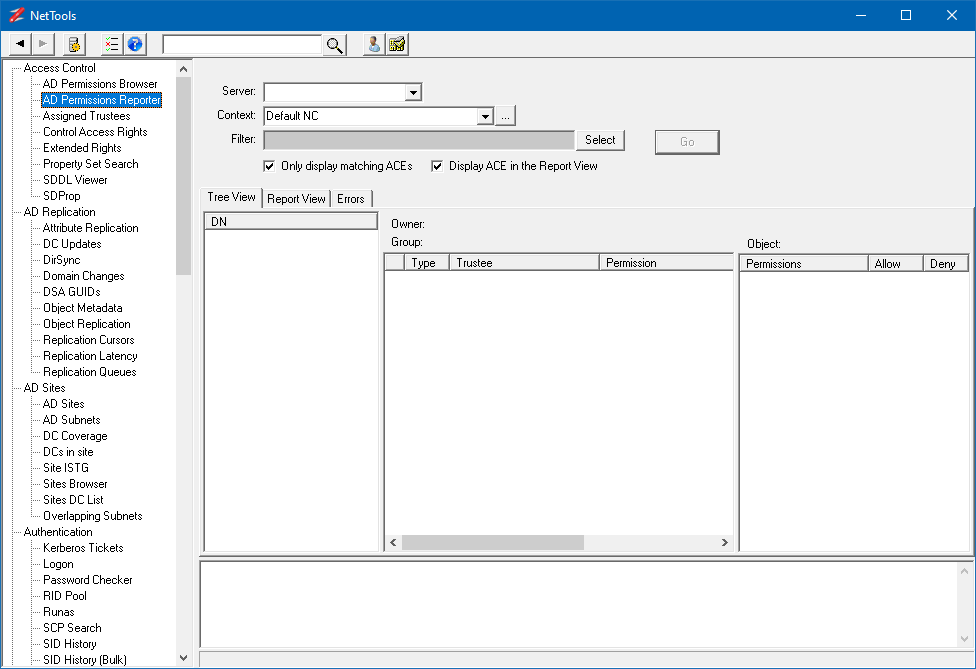
The AD Permissions Reporter can be used to report on what permissions are assigned to specific objects and understand who has the rights to make changes. The AD Permissions Reporter is located under the Access Control in the Options selection pane on the left side. By selecting the AD Permissions Reporter the default screen is displayed as shown below.
We will build a new Advanced Filter to report on permissions providing these rights, if you want to skip the building of the Filter, you can skip to the bottom of the post where you can find the Filters that you can simply import.
Who can reset the Domain Admins Passwords
To be able to reset the password on an account, you need the Reset Password right, this can be assigned as specific right or when all rights are assigned, this means we will need to build an Advanced Filter which has multiple rules.
The Domain Admins group and any members, including nested members, are protected from the SDProp process and this process will assign permissions to these users and groups based on the permissions assigned to the AdminSDHolder container. We will use this behavior to help simplify the report that we need to do, as we don't need to query the individual users, as they will have the same permissions irrespective of their location in the AD.
For more information on the SDProp process see SDProp.
At the option screen click on the Select button to open the Select Filter dialog, as we are going to create a new filter click on the Add button. This will display the new Permissions Filter dialog.
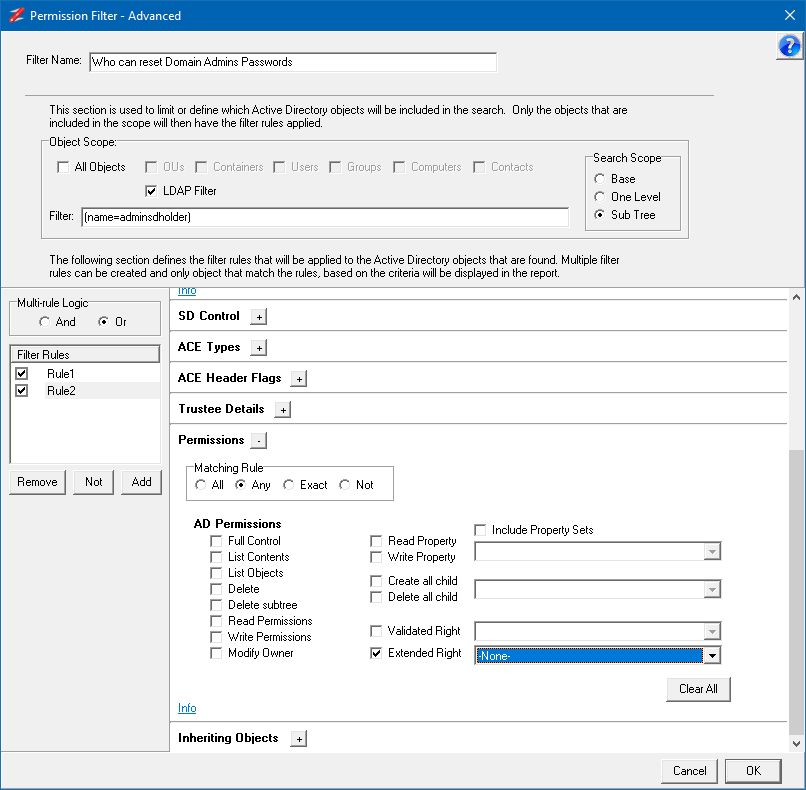
In the Filter Name field enter 'Who can reset Domain Admins Passwords' and then click on Advanced Filter button which will open the Advanced Filter .
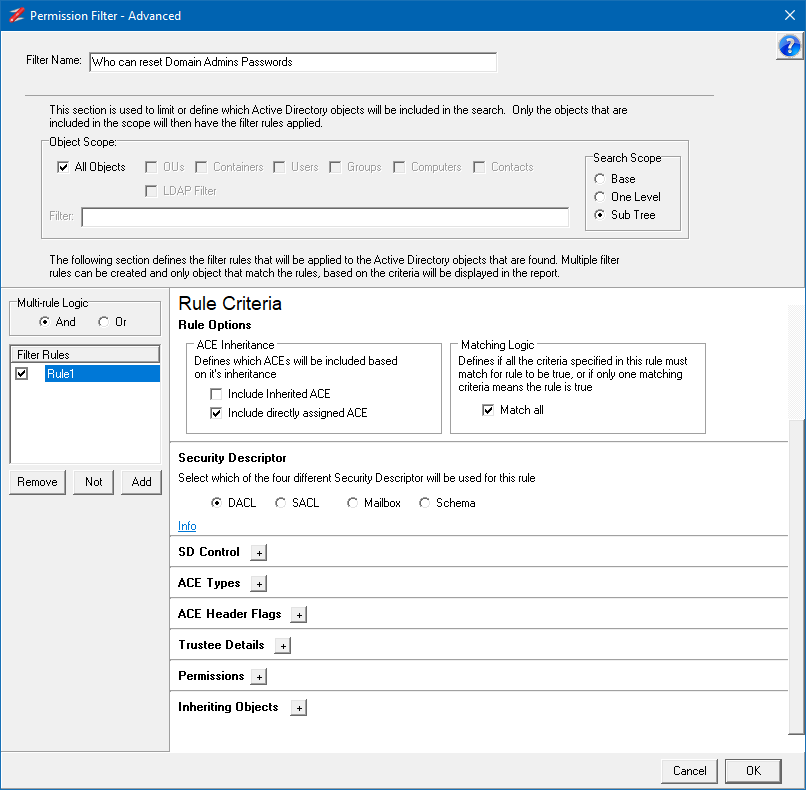
First we need to define the scope of the Filter, and as we are going to use the AdminSDHolder for this filter, we will set an LDAP Filter to select it. Untick All Objects in the Object Scope section and select LDAP Filter. Make sure the Search Scope is set Sub Tree. In the Filter field enter the following Filter:
(name=adminsdholder)
Make sure that the Match all option in the Matching Logic is set.
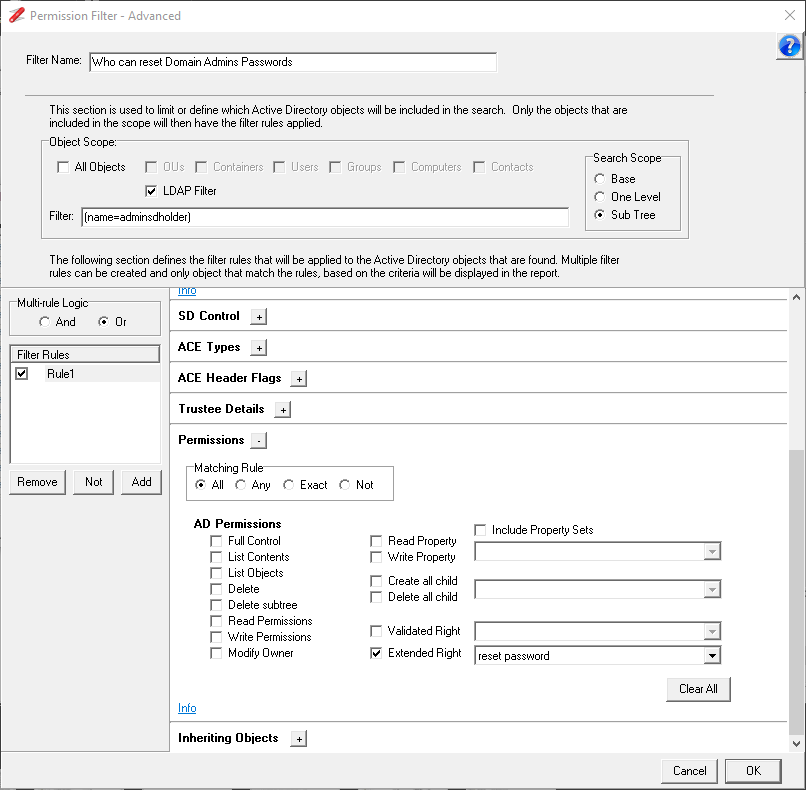
Next we need to set the Permission we want to search for, Expand the Permissions section. Set the Matching Rule to All and check the Extended Right option and from the dropdown list select "reset password" option. Your Filter should look like this:
This rule covers the specific granting of the reset password right, however users that have been assigned the All Validate Rights can also reset the password, so we need to add another rule to search for this permission as well.
On the left side click on the Add button under the Filter Rules, this will add a new Rule2 entry. With version V1.31.3 and below there is a bug which resets the Object Scope when a new Rule is created, you just need reselect the LDAP Filter option.
As we want to return permissions if either of these Rules are matched, select the Or option in the Multi-rule Logic
Select the Match all option in the Matching Logic Section
Expand the Permissions section, select the Extended Rights option. As we want to return the All Extended Rights, we need to select -None- from the dropdown list.
Click on the OK to save the Filter. In the Select Filter window click on Select.
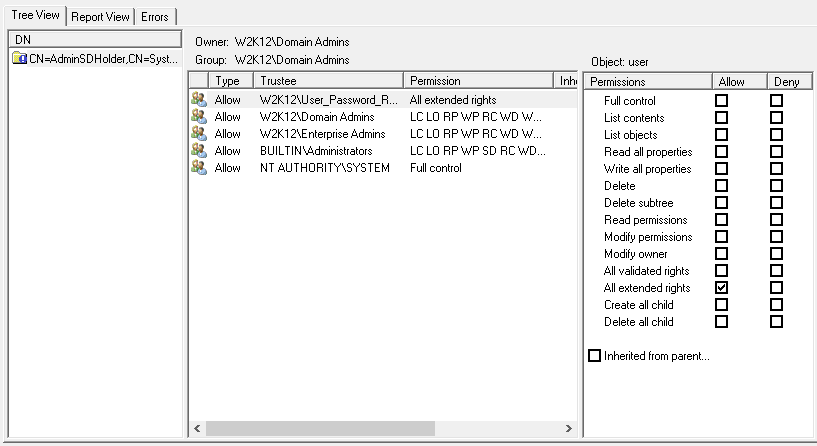
With the Filter selected click on Go. Once the scan has completed you should get something like this:
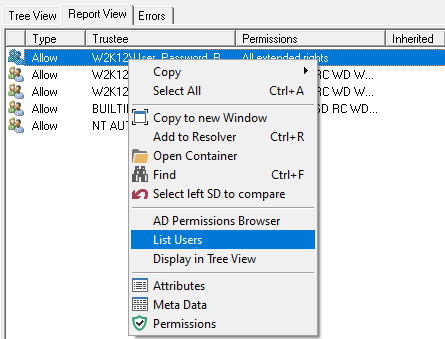
The results show you which permissions provide the rights to reset the password. Now to find out which users have these permissions, we need to select the Report View tab, which displays all the permissions in a list view, now by right clicking on one of the permissions and selecting List Users from the context menu, you will get the complete list of users that have these rights in your environment.
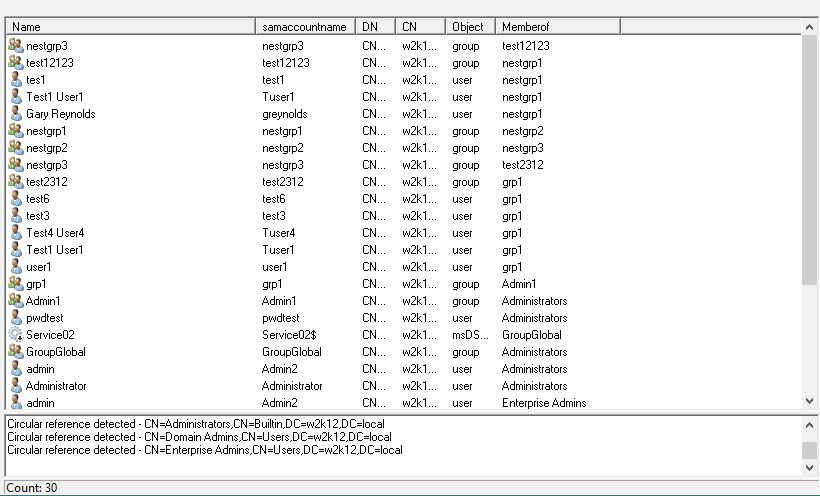
This will switch to the Group Members option and will display all the users and members of the groups. This is the list of users that have the rights to reset the password on the Domain Admin accounts.
Filters
If you you don't want to build the filter yourself, here is the save filter, you just need to copy the text below and import as a filter, see How to Import Filter
Who can reset Domain Admins Passwords
[Who can reset Domain Admins Passwords] LDAPFilter=(name=adminsdholder) Count=2 Options=18944 Rule1_Enabled=1 Rule1_Options=1281 Rule1_SDControl=0 Rule1_SDNotControl=0 Rule1_SDNullAcl=0 Rule1_Prompt=0 Rule1_Token=0 Rule1_AuthGroups=0 Rule1_Scope=8 Rule1_NotScope=0 Rule1_ACEType=0 Rule1_ACEFlags=0 Rule1_ACENotFlags=0 Rule1_Perms=256 Rule1_NotPerms=0 Rule1_Property=00299570-246D-11D0-A768-00AA006E0529 Rule1_NoProperty=0 Rule1_PropType=4 Rule1_MatchRules=546 Rule2_Enabled=1 Rule2_Options=1281 Rule2_SDControl=0 Rule2_SDNotControl=0 Rule2_SDNullAcl=0 Rule2_Prompt=0 Rule2_Token=0 Rule2_AuthGroups=0 Rule2_Scope=8 Rule2_NotScope=0 Rule2_ACEType=0 Rule2_ACEFlags=0 Rule2_ACENotFlags=0 Rule2_Perms=256 Rule2_NotPerms=0 Rule2_Property=00299570-246D-11D0-A768-00AA006E0529 Rule2_NoProperty=1 Rule2_PropType=4 Rule2_MatchRules=530