Features shown in this post are only available in NetTools v1.31.6 and above.
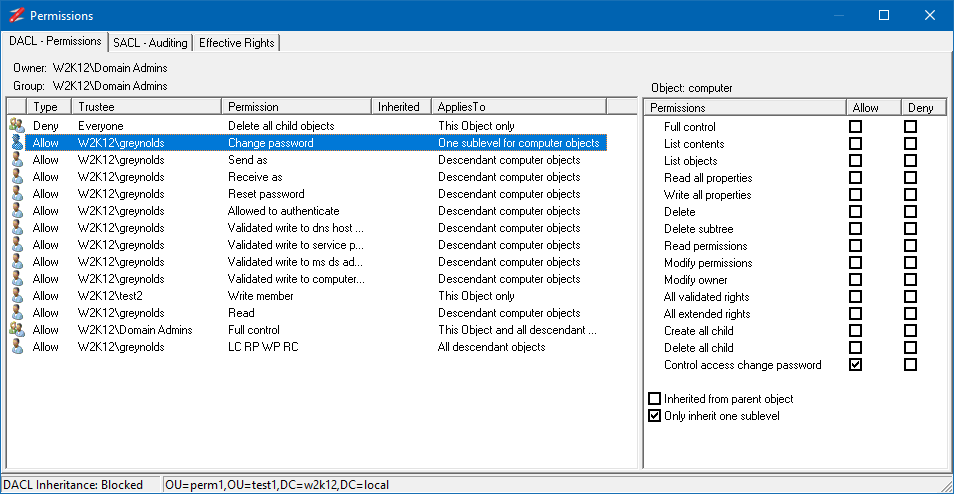
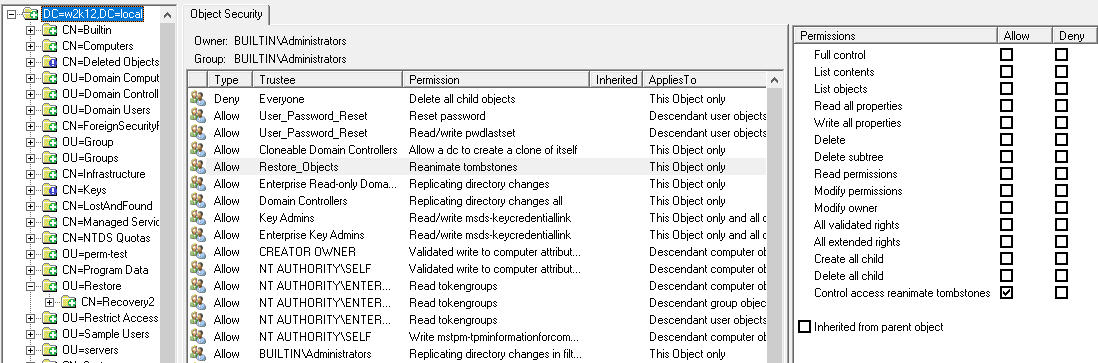
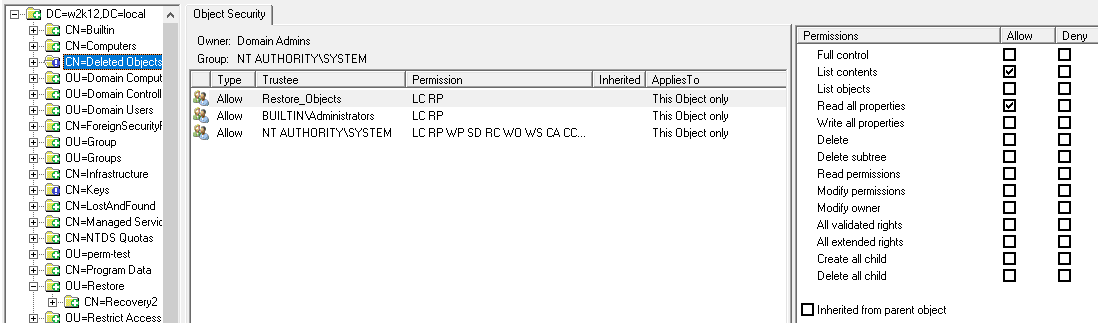
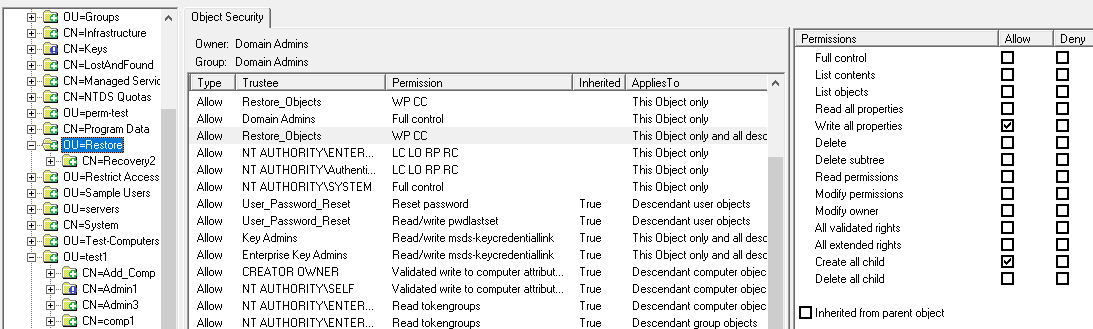
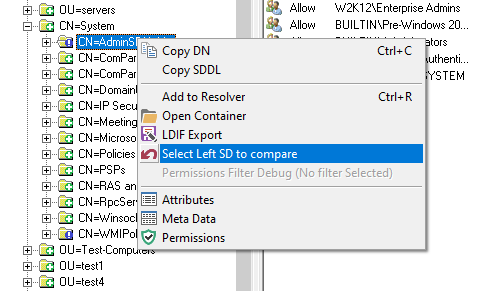
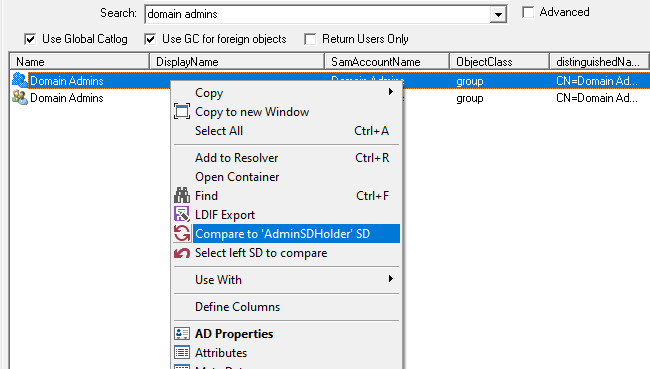
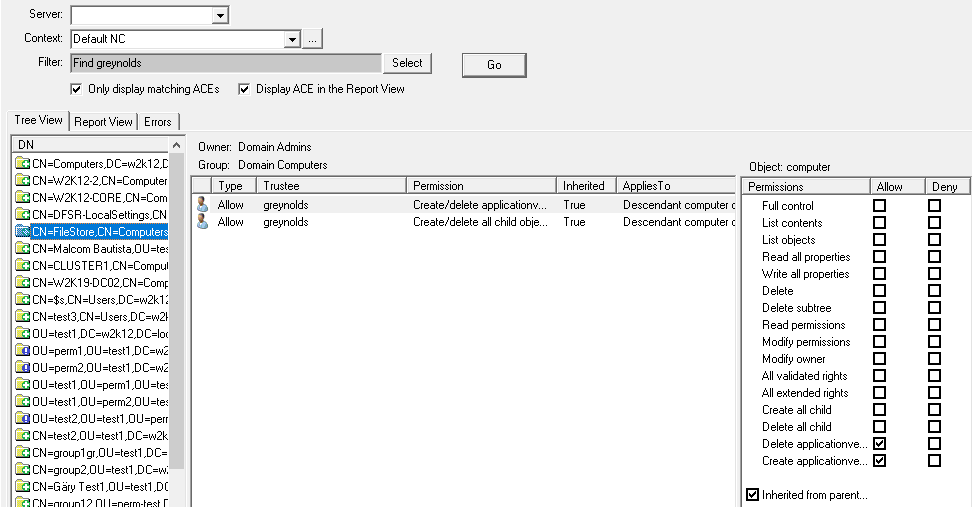
NetTools allows editing the permissions of the objects in Active Directory. An object's permissions can be edited from the Permissions dialog, which provides similar functionality to the ADUC permissions dialog, but provides more control over the permission configuration than the native tools. The Permissions dialog is accessed via the Permissions options on the context menu, which is available throughout NetTools.
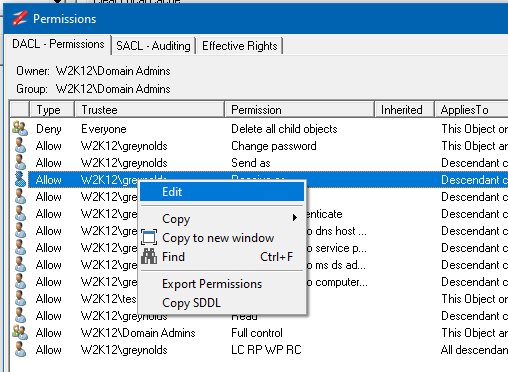
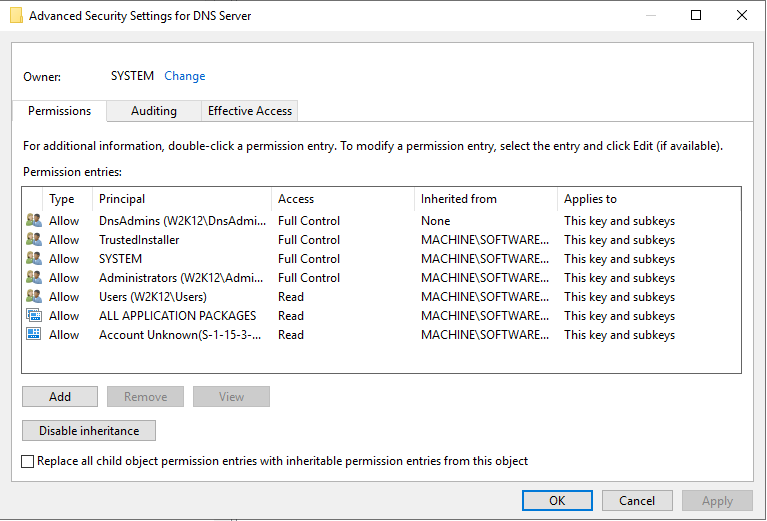
By default, the Permissions dialog opens in read-only mode. To enable editing of the permissions, right-click on the list of permissions and select Edit from the context menu. Once selected, the edit control bar is displayed at the bottom of the permissions list.
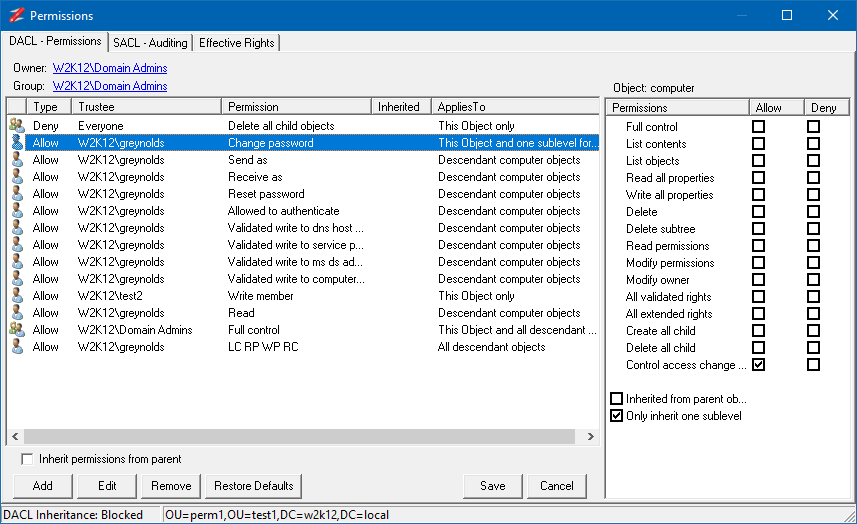
The buttons on the edit control bar allow you to add, edit, and remove permissions. The Restore Defaults button, will restore the default permissions for the object, as defined in the schema for the object. The Inherit permissions from parent option allow block inheritance from the parent object, when unselected, you are presented with the option to copy the existing inherited permissions.
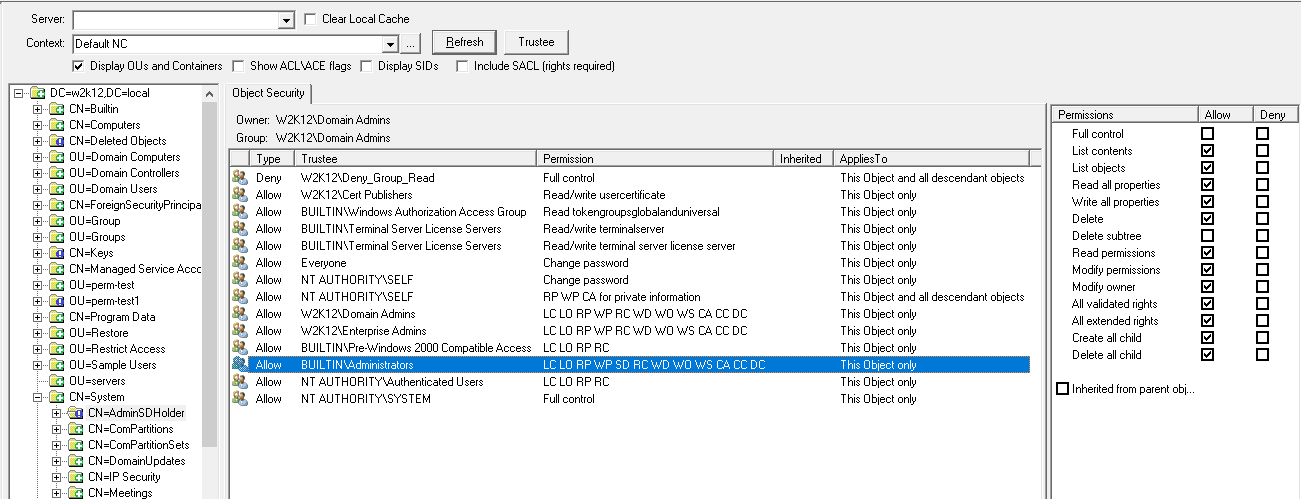
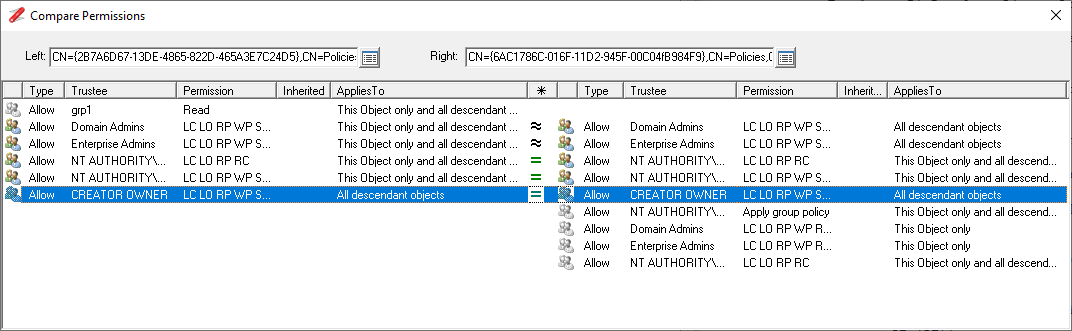
It is possible to update both the DACL or SACL permissions of an object, but you can only edit one at a time, you must save or cancel any edits before editing the other permissions on the other tab.
If the Permissions dialog is opened not based on an AD object and the status bar doesn't display the DN of the object, then the Save and Restore Defaults buttons are not displayed, this allows you to modal the permissions but not save them.
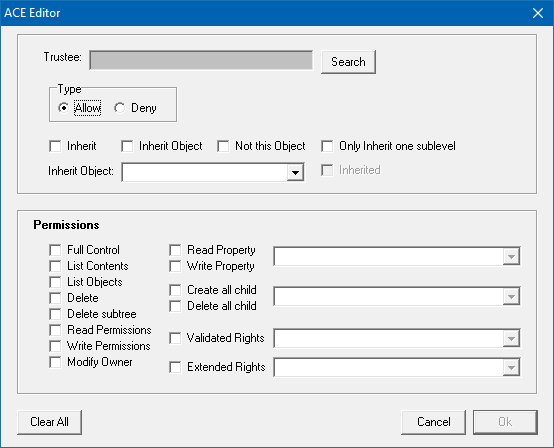
The following dialog is shown when adding new permission or editing existing permission:
The top part of the dialog is used to select the trustee, the access type, and how the permissions are inherited, and the lower section specifies the permissions that will be set.
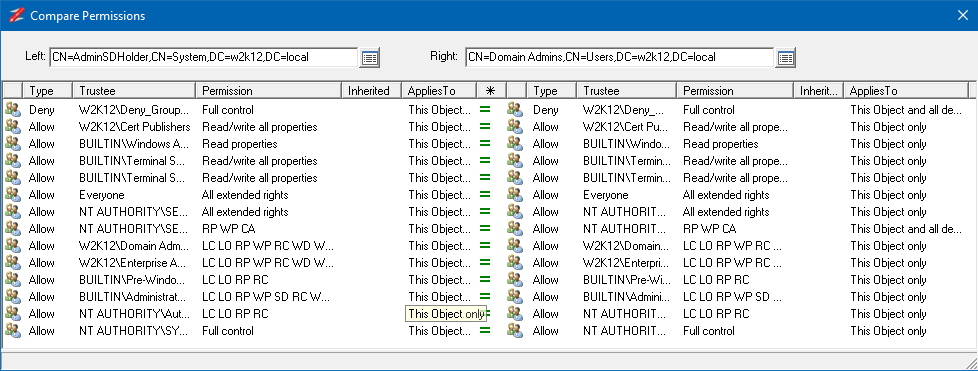
The edit permissions can be used in conjunction with the Effective Rights tab to model the permissions.