This post provides a number of LDAP Search Favorites for common operations, copy the text of the query and import into the favorites, the samples will be saved in the favorites list as the name in square brackets, see Favorites for more information.
Inactive Users
Return a list of users that have not logged on in the last 60 days and excluded any accounts created in the last 60 days
[Users - Inactive Accounts]
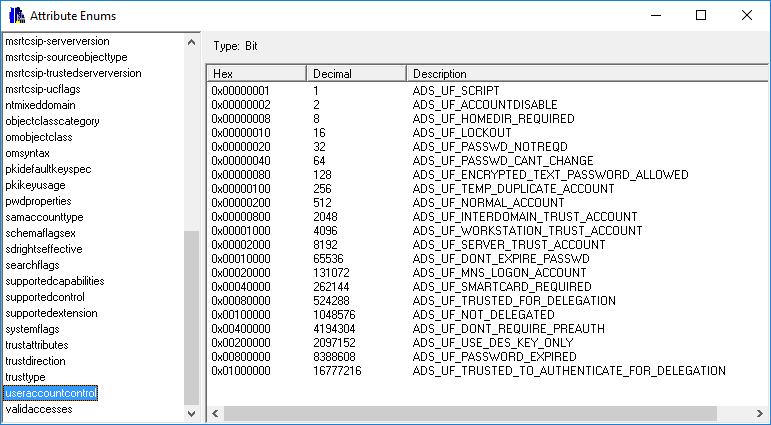
Options=660045
Server=
BaseDN=##default
Filter=(&(objectclass=user)(objectcategory=user)(!useraccountcontrol|=2)(|(lastlogontimestamp<={idate:now-60})(&(whencreated<={zdate:now-60})(pwdlastset=0))))
Attributes=canonicalname, samaccountname, displayname, description, pwdlastset, accountexpires, lastlogontimestamp, msExchShadowDepartment, msExchWhenMailboxCreated, msExchRecipientDisplayType, msExchRecipientTypeDetails, homeMDB
DisplayFilter=
Filename=
Sort=
Authentication=1158
Separator=,
Active Accounts
A simple active users query to display a list of users where the user has logged on or changed their password in the last 60 days, and any account that have been created in the last 60 days but the user has not set their password yet.
[Users - Active Accounts]
Options=660036
Server=
BaseDN=##default
Filter=(&(objectclass=user)(objectcategory=user)(!useraccountcontrol|=2)(|(lastlogontimestamp>={idate:now-60})(pwdlastset>={idate:now-60})(&(whencreated>={zdate:now-60})(pwdlastset=0))))
Attributes=canonicalname, samaccountname, displayname, description, pwdlastset, accountexpires, lastlogontimestamp, msExchShadowDepartment, msExchWhenMailboxCreated, msExchRecipientDisplayType, msExchRecipientTypeDetails, homeMDB
DisplayFilter=
Filename=
Sort=
Authentication=1158
Separator=,
Active User with user input
This query is the same as the one above however the static 60 days used above is replaced with a prompt. At execution time a dialog will be displayed to enter the Activity Period. In the query the static 60 has been replaced with {userinput:Activity Period (Days)} to prompt for the value. This Subst is used a number of times in the query but only prompted for once, as the first response is cached and used for subsequent entries with the same label. See Substitutions
[Users - Active Accounts Input]
Options=8590594637
Server=
BaseDN=##default
Filter=(&(objectclass=user)(objectcategory=user)(!useraccountcontrol|=2)(|(lastlogontimestamp>={idate:now-{userinput:Activity Period (Days)})(pwdlastset>={idate:now-{userinput:Activity Period (Days)}})(&(whencreated>={zdate:now-{userinput:Activity Period (Days)}})(pwdlastset=0)))(|(accountExpires=0)(accountExpires=9223372036854775807)(accountExpires<={idate:now})))
Attributes=canonicalname, samaccountname, displayname, description, pwdlastset, accountexpires, lastlogontimestamp, msExchShadowDepartment, msExchWhenMailboxCreated, msExchRecipientDisplayType, msExchRecipientTypeDetails,accountExpires
DisplayFilter=
Filename=
Sort=
Authentication=1158
Separator=,
Active Accounts Count
This is the same as the first active accounts queries, but this doesn't display any details of the users, just the count.
[Users - Active Accounts Count]
Options=8590594628
Server=
BaseDN=##default
Filter=(&(objectclass=user)(objectcategory=user)(!useraccountcontrol|=2)(|(lastlogontimestamp>={idate:now-60})(pwdlastset>={idate:now-60})(&(whencreated>={zdate:now-60})(pwdlastset=0))))
Attributes=1.1
DisplayFilter=
Filename=
Sort=
Authentication=1158
Separator=,
Active Accounts (More Complex)
This query builds on the queries above and include the account expires attributes in the checking.
[Users - Active Accounts AE]
Options=8590594637
Server=
BaseDN=##default
Filter=(&(objectclass=user)(objectcategory=user)(!useraccountcontrol|=2)(|(lastlogontimestamp>={idate:now-60})(pwdlastset>={idate:now-60})(&(whencreated>={zdate:now-60})(pwdlastset=0)))(|(accountExpires=0)(accountExpires=9223372036854775807)(accountExpires<={idate:now})))
Attributes=canonicalname, samaccountname, displayname, description, pwdlastset, accountexpires, lastlogontimestamp, msExchShadowDepartment, msExchWhenMailboxCreated, msExchRecipientDisplayType, msExchRecipientTypeDetails, homeMDB
DisplayFilter=
Filename=
Sort=
Authentication=1158
Separator=,
Disable users
This favorite is a input mode Update query which will disable the provided list of SamAccountNames, it will prompt for a change number which will be added to the Info field of each user. See Update Queries for more information about update queries.
Warning: This is a Update Query which will make changes to your AD once the update feature is enabled
[Users - Disable Users]
Options=489626931805
Server=
BaseDN=##default
Filter=(samaccountname=##input)
Attributes=useraccountcontrol=|2:2, info==Account disabled as part of change {userinput:Enter Change Number}\n{attrib:info}
DisplayFilter=
Filename=
Sort=
Authentication=1158
Separator=,
AD Tombstone Period
This query will display the current AD tombstone period for deleted\recycled objects.
[AD Tombstone Period]
Options=132677
Server=
BaseDN=CN=Directory Service,CN=Windows NT,CN=Services,##config
Filter=(objectclass=*)
Attributes=tombstonelifetime
DisplayFilter=
Filename=
Sort=
Authentication=1158
Separator=,
AD Schema Version
This query will display the current AD schema version
[Schema Version - AD]
Options=132673
Server=
BaseDN=##schema
Filter=(objectclass=*)
Attributes=objectversion
DisplayFilter=
Filename=
Sort=
Authentication=1158
Separator=,
Exchange Schema Version
This query will display the current exchange schema version.
[Schema Version - Exchange]
Options=132673
Server=
BaseDN=CN=ms-Exch-Schema-Version-Pt,##schema
Filter=(objectclass=*)
Attributes=rangeupper
Filename=
Authentication=1158
User=
Domain=
OCS Schema Version
This query will display the current OCS\Link\SfB schema version.
[Schema Version - OCS]
Options=132673
Server=
BaseDN=CN=ms-RTC-SIP-SchemaVersion,##schema
Filter=(objectclass=*)
Attributes=rangeupper,rangelower
Filename=
Authentication=1158
User=
Domain=
Root DSE
This query will return the default values for the RootDSE
[RootDSE]
Options=656901
Server=
BaseDN=NULL
Filter=(objectclass=*)
Attributes=
DisplayFilter=
Filename=
Sort=
Authentication=0
Separator=,
RootDSE (Full)
This query will display both the default and optional values of the RootDSE, the values returned are based on the current DC OS and DFF level.
[RootDSE (Full)]
Options=132613
Server=
BaseDN=NULL
Filter=(objectclass=*)
Attributes=*,domainControllerFunctionality,domainFunctionality,forestFunctionality,msDS-ReplAllInboundNeighbors,msDS-ReplAllOutboundNeighbors,msDS-ReplConnectionFailures,msDS-ReplLinkFailures,msDS-ReplPendingOps,msDS-ReplQueueStatistics,msDS-TopQuotaUsage,supportedConfigurableSettings,supportedExtension,dsaVersionString,msDS-PortLDAP,msDS-PortSSL,msDS-PrincipalName,serviceAccountInfo,spnRegistrationResult,validfsmos,tokenGroups,usnAtRifm
Filename=
Authentication=1158
Separator=,