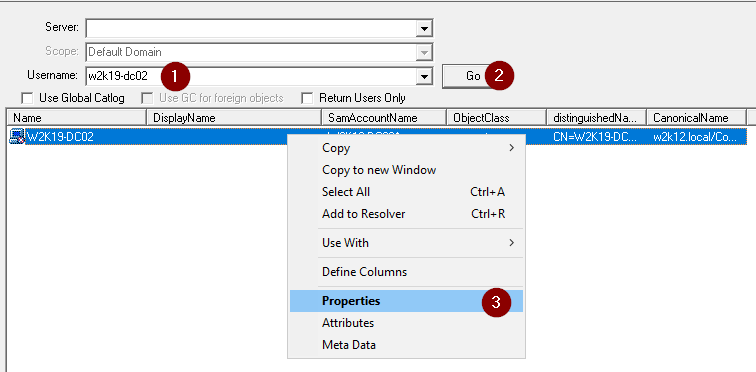
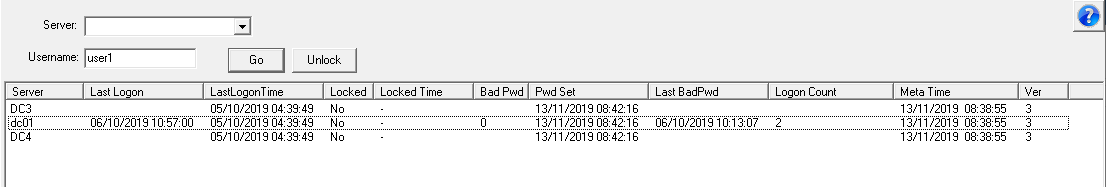
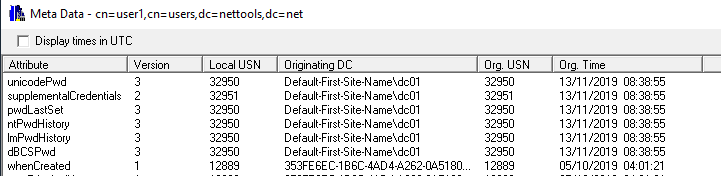
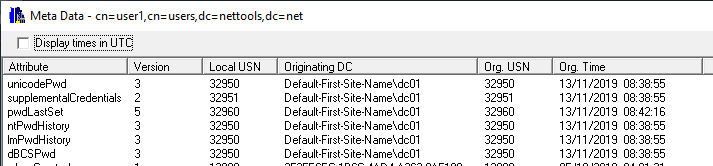
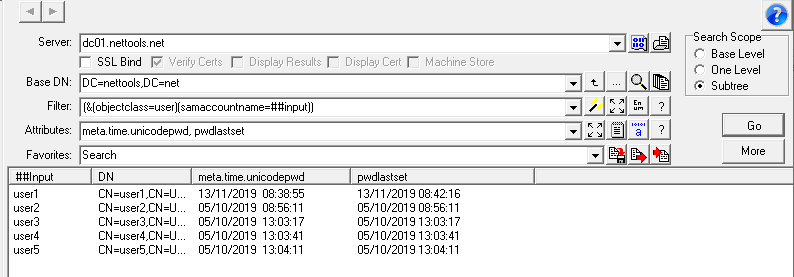
If you have configured BitLocker to store the recovery keys in AD, you can use NetTools to retrieve the BitLocker Recovery Key. With NetTools the process to retrieve the recovery key is really simple.
Select the User - Search option in the left hand pane and make sure that the Return Users Only is deselected, and then complete the following steps:
- Enter the name of the computer
- Click Go
- Open the AD Properties for the computer
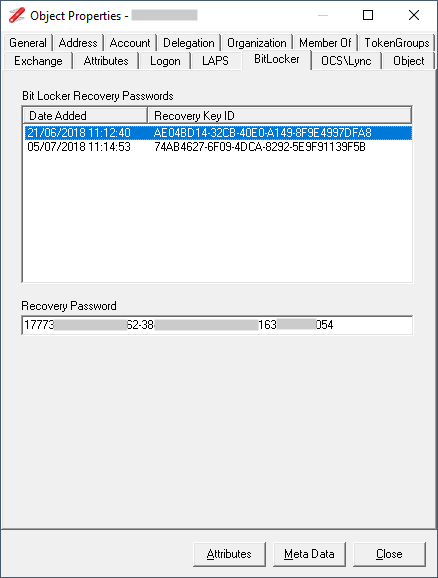
Select the BitLocker tab
Select the Recovery Key ID that is displayed on the BitLocker Recovery screen
Note: the BitLocker tab will only be displayed if msFVE-RecoveryInformation object exist on the computer object and you have the rights to read the object