This feature is supported in NetTools v1.30.9 beta and above
With the introduction of Windows 2008 R2, a new feature called Active Directory Recycle Bin was introduced. This feature allow you to restore objects that have been deleted by mistake or maliciously, without the need to do a restoration from backup and the AD authoritative restore. For new forest installs of Windows 2008R2 and above, this feature is enabled by default, for forests were the domain controller have been upgrade, the feature has to be manually enabled. To enable the Active Directory Recycle Bin see this page which has the details.
The only method that was originally provided to recovery delete object was through LDP, which requires multiple steps and configuration changes to be able to restore an object.
NetTools provides a simple method to restore single or multiple objects in a single operation. This feature is incorporated in the LDAP Browser option.
To be able to restore a delete object you must meet the following prerequisites:
- The recycle bin feature must be enabled
- The recycle bin feature must have been enabled before the objects were deleted
- Be a member of Domain Admins or equivalent
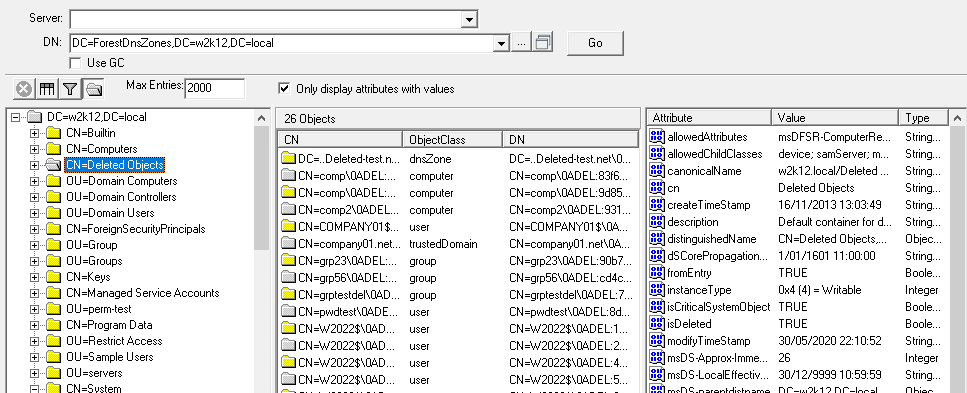
When an object is deleted it's moved to the Deleted Objects container, in the partition that the object existed. This also means that objects that have been deleted from the Configuration, DomainDNSZones, and ForestDNSZones can be restored using NetTools. When browsing the partitions with LDAP Browser the deleted object will be displayed in CN=Deleted Objects,<partiton dn>.
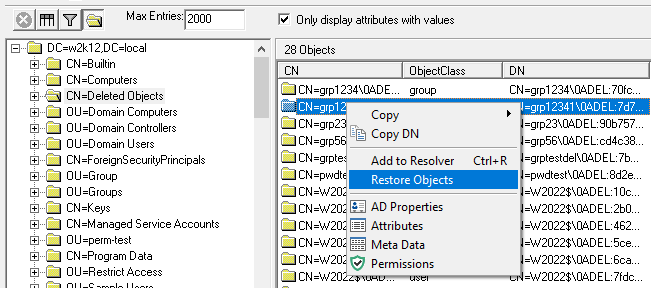
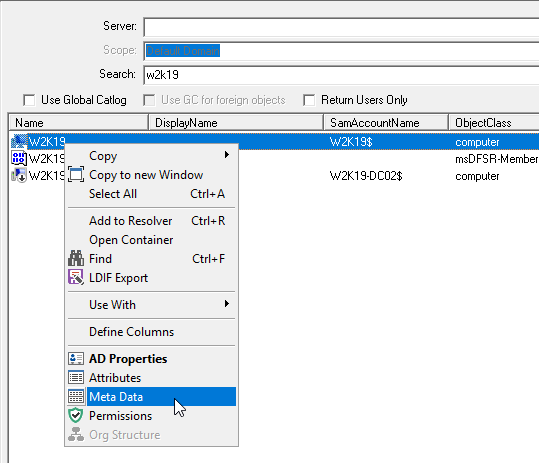
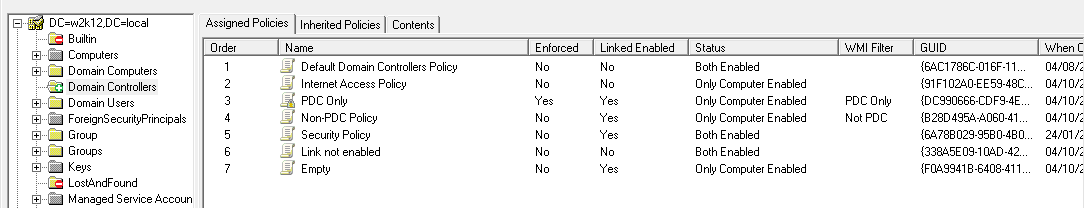
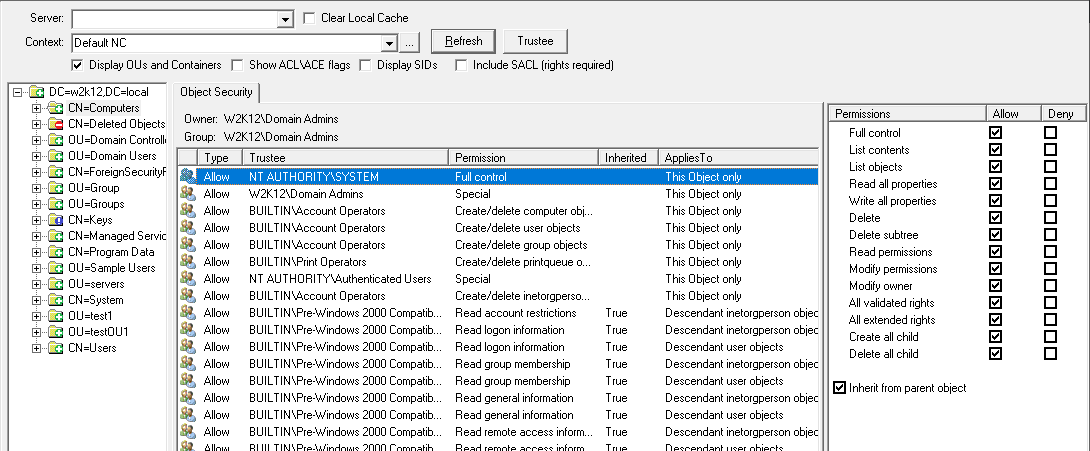
Objects that are listed in the Deleted Objects container can be restored by select the objects and right clicking and selecting Restore Objects from the context menu.
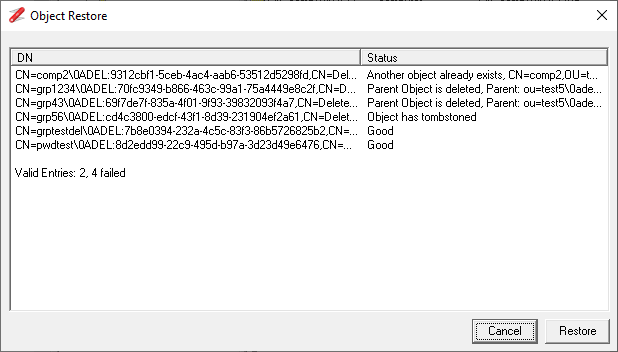
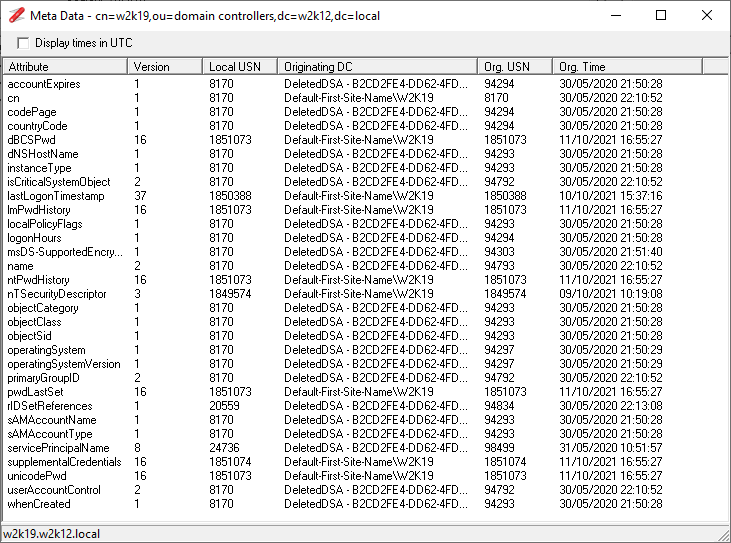
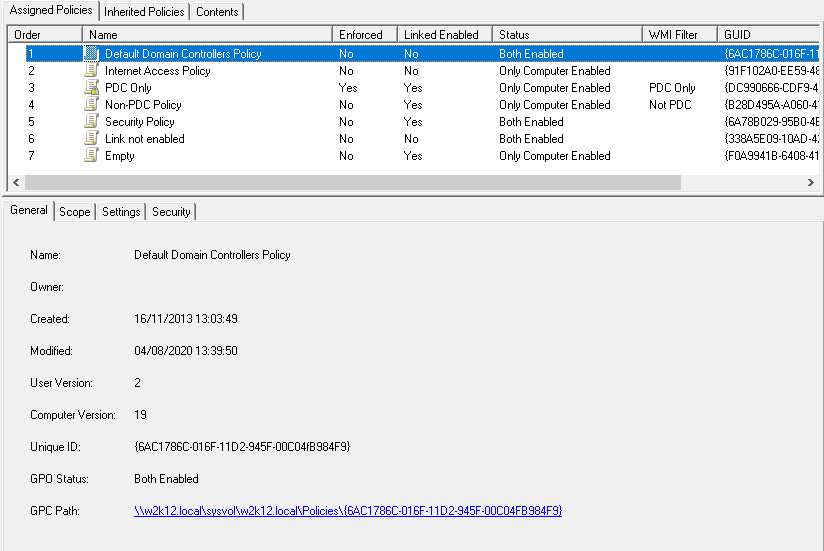
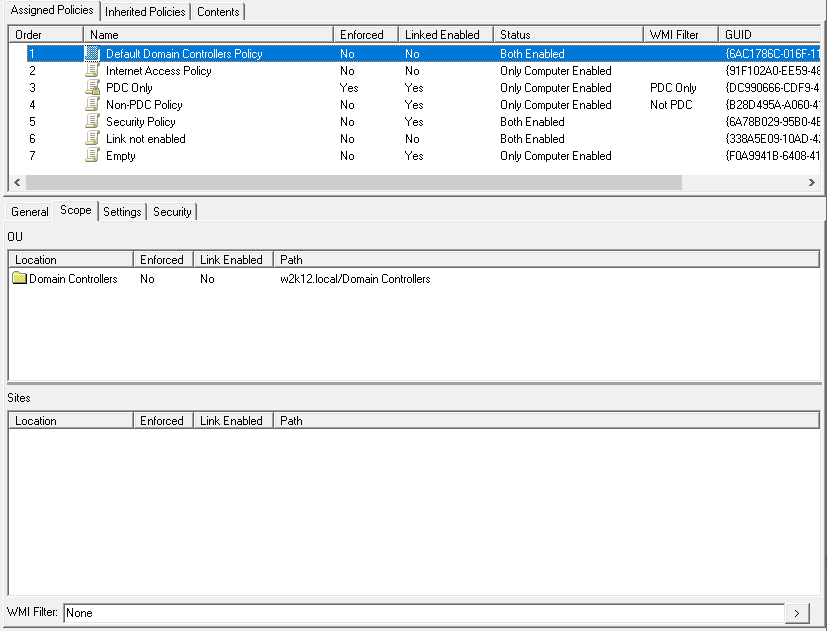
The context menu option will open the Object Restore dialog, shown below. When the dialog opens it will perform a number of validation checks of the selected objects, to ensure that the common issues are detected before the restore is attempted.
The Validation consists of the following checks:
- If the object has been tombstoned
- If the target parent container still exists
- if the target parent container is deleted
- If a new object with the same name has been created in the target parent
The objects that pass the validation will show a status of Good, for objects that fail these checks, the reason will be displayed in the status column and can't be restored. See Troubleshooting section for details on how to try and resolve these issues.
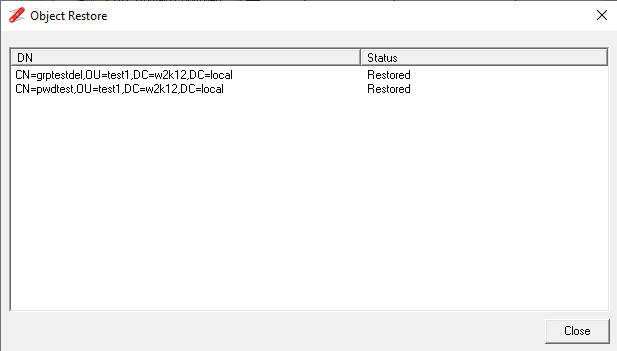
Once the validation is complete the results are shown at the bottom of the list of objects, and then the Restore button will be enabled. By clicking the restore button, only the objects that are valid will be restored.
The context menu provides the standard option to review the restored objects.
Restoring A Deleted OU
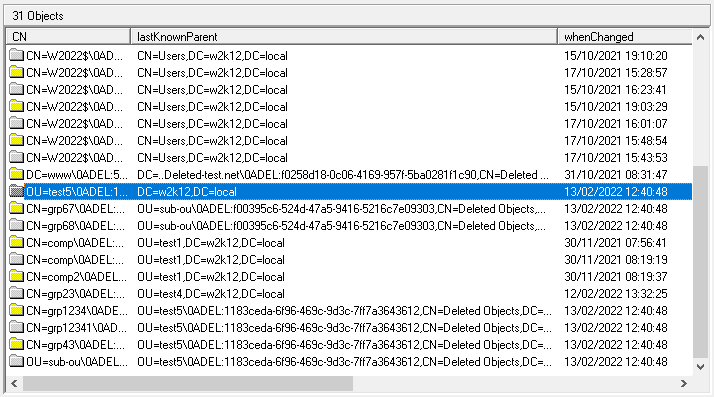
If an OU has been deleted which contains multiple objects and child OUs, these can also be restored, however, the OU structure must be restored first, then followed by the object in the OU. The simplest method to find objects that have been deleted from the same the OU, is to change the column displayed to include the LastKnownParent and WhenChanged
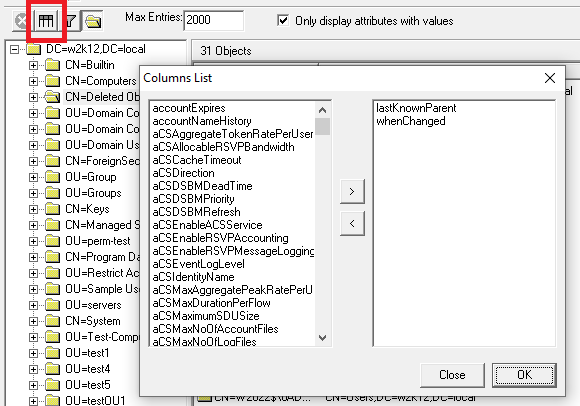
For this example, here are the details of the OU Structure that has been deleted. Sorry about the names, it was an OU that was already created!
These are the steps needed to restore the OU structure
- Restore the Parent OU
- Restore any sub level OUs
- Restore the child objects
Restore Parent OU
First you will need to restore the top level OU called Test5, sort the columns by the LastKnownParent column to make it easier to find the parent OU for Test5, in this case the root.
Restore the sub level OU
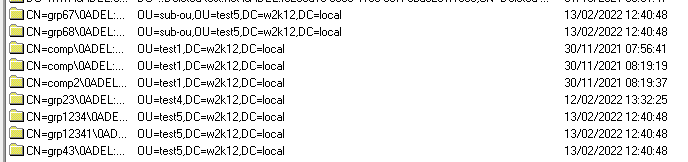
With the Parent OU restored it's now easier to find which objects were in the OU structure, as the LastKnownParent has now been updated, next restore any sub level OUs, in our example sub-OU has been restored.
Restore child Objects
Once the OU structure has been restored, we are ready to restore the objects from the OU structure, one things that we need to be conscious of, some objects may have been deleted previously and we don't want to restore these objects, using the WhenChanged column to help identify the objects we want to restore.
Troubleshooting
This section provide somes some extra details of the possible error messages that can happen during the validation.
Object has tombstoned
The object was been delete grater than msDS-deletedObjectLifetime period and now the object has been tombstoned. The object has the IsRecycled attribute set to true. Which means most of the attributes of the object have been removed and the object only exists to ensure replication is consistent between the domain controllers and the object can't be restored.
Parent Object is deleted
You are trying to restore an object to a parent object, but the parent object is currently deleted, restore the parent object first, then try restoring the child object.
Parent Object not found
Something has changed from selecting the object and running the validation, close the Object Restore dialog and try again.
Parent details not found
Failed to read the LastKnownParent attribute, confirm the attribute is set and try again.
Another object already exists
Since the object was deleted, another object with the same name has been created in the parent OU, either move or rename the new object so you can restore the deleted object.
Failed to get DN details
Failed to read the LastKnownParent or msDS-LastKnownRDN attributes, confirm these attributes are set and try again.