There are a number of different ways to check if an AD domain join workstation is still being used or active in the environment. This article provides a couple of different approaches depending on the number of workstations or type of information required. All approaches are based on the standard assumption that an active workstation will update the pwdlastset, lastlogon, lastlogontimestamp attributes while connected to the domain\network.
Which attribute you use to validate if the workstation is still active will depend on the configuration of the AD:
PwdLastSet – this will change each time the workstation changes it’s password and this change is replicated to all domain controllers, so the time reported by one domain controller will be the same on all. The frequency at which the password is changed is controlled by the Domain Member: Maximum machine account password age and Domain Member: Disable machine account password changes, GPO settings. The default maximum password age is 30 days, however, if the password update is disabled, then the PwdLastSet attribute will not changed. Also in some scenarios if the workstation is used remotely, and not connected to the network for long periods of time, then the pwdlastset will not be updated.
LastLogon – this is the last time that the workstation logged on, however, this attribute is not replicated between domain controllers and you have to retrieve the attribute from all the domain controllers to get the last logon time. As with the PwdLastSet attribute, if the workstation is used remotely for long periods of time, this attribute may not be updated.
LastLogonTimeStamp - this attributes is also replicated between domain controllers, however, the replication of this attribute doesn’t happen every time the workstation logs on, by default it will be updated every 14 days, details here , so if 14 days is close enough then this is the best attribute to use.
Single Workstation:
The quickest method is search for the workstation using the Search option under Users to find the workstation’s object in AD, from there right click on the required workstation and from the context menu, select Use With -> Last Logon. All three attributes are displayed in the one view. The Last Logon column displays the lastlogon attribute from each of the domain controllers in the domain, sorting this column to display the last logon time, the lastlogontimestamp and pwdlastset will be the same across all servers.
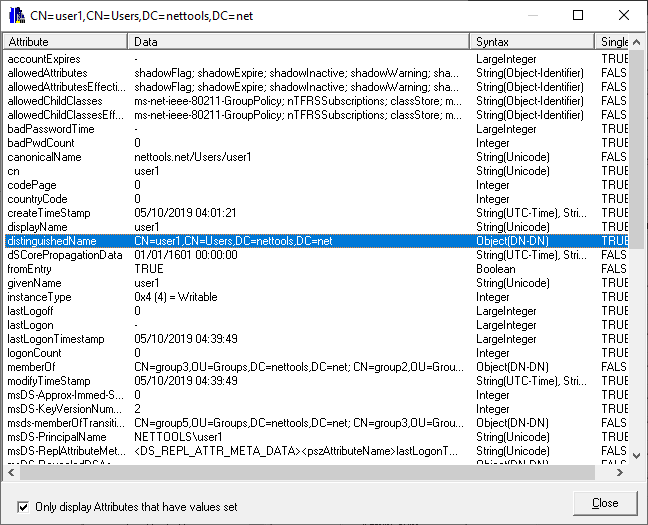
Another method to check for activity, but not specifically based on the lastlogon attribute, you can use the object Meta Data to get the list of attributes that have been changed, and then compare the time the changes were made to confirm if the workstation is still active. To display the Meta Data for an object, complete the search as describe above, from the context menu, select Meta Data, and then sort the form based on the time column. The attributes that are relevant are dBCsPwd, lmPwdHistory, ntPwdHistory, pwdLastSet, supplementalCredentials, unicodePwd which are updated when a password is updated.
Multiple Workstations:
If you want to check the details of a number of workstations, the Last Logon Time option is the easiest option to use. This option requires a list of samaccountnames of the workstation, with workstations the samaccountname must include the trailing $ character. Once the list is pasted into the right hand pane, and Go pressed, it will check each entry against all the domain controllers in the domain and it will display the latest time recorded against all the domain controllers.
If you require additional information about the workstations other than the lastlogon details, then the LDAP Search is the best option, the save query below uses Input Mode to return the details, you paste a list of workstations into the Input pane and return any information you require about the workstations, include Operating System, Version, etc.
[Active Workstations]
Options=879892770722397
Server=
BaseDN=##default
Filter=(&(objectclass=computer)(samaccountname=##input))
Attributes=lastLogon,lastLogonTimestamp,operatingSystem,operatingSystemVersion
DisplayFilter=
Filename=
Sort=
Authentication=1158
Separator=,
In this example it assumes that the workstation SamAccountNames will have the trailing $, however, changing the filter to the following and the trailing $ is not required:
Filter=(&(objectclass=computer)(samaccountname=##input$))
Related Items
Troubleshooting Account Lockouts
User Search
LDAP Search
Input Mode
Favorites