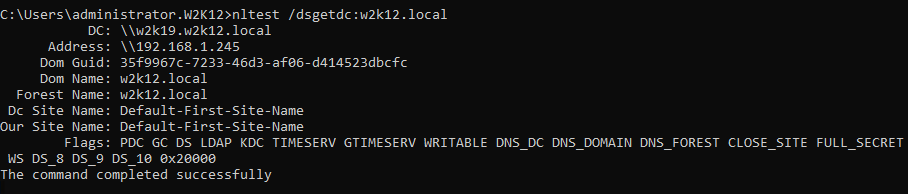
When running NLTEST /DSGETDC command against a domain controller that is Windows 2012R2 or later, the command will display the normal flags plus an extra flag called '0x20000', but what does the 0x20000 flag mean. First of all it's not an error code, Microsoft have added an additional feature to Windows 2012R2 and later DCs, but NLTEST hasn't been updated to display this flag correctly, even the Windows 2019 version doesn't have this flag defined.
The results deplayed by NLTEST /DSGETDC is the information returned by the DsGetDcName API, this information if defined in the DOMAIN_CONTROLLER_INFO structure.
typedef struct DOMAIN_CONTROLLER_INFOA { LPSTR DomainControllerName; LPSTR DomainControllerAddress; ULONG DomainControllerAddressType; GUID DomainGuid; LPSTR DomainName; LPSTR DnsForestName; ULONG Flags; LPSTR DcSiteName; LPSTR ClientSiteName; } DOMAIN_CONTROLLER_INFOA, *PDOMAIN_CONTROLLER_INFOA;
The Flags member has the following definitions in the dsgetdc.h file
#define DS_PDC_FLAG 0x00000001 // DC is PDC of Domain #define DS_GC_FLAG 0x00000004 // DC is a GC of forest #define DS_LDAP_FLAG 0x00000008 // Server supports an LDAP server #define DS_DS_FLAG 0x00000010 // DC supports a DS and is a Domain Controller #define DS_KDC_FLAG 0x00000020 // DC is running KDC service #define DS_TIMESERV_FLAG 0x00000040 // DC is running time service #define DS_CLOSEST_FLAG 0x00000080 // DC is in closest site to client #define DS_WRITABLE_FLAG 0x00000100 // DC has a writable DS #define DS_GOOD_TIMESERV_FLAG 0x00000200 // DC is running time service (and has clock hardware) #define DS_NDNC_FLAG 0x00000400 // DomainName is non-domain NC serviced by the LDAP server #define DS_SELECT_SECRET_DOMAIN_6_FLAG 0x00000800 // DC has some secrets #define DS_FULL_SECRET_DOMAIN_6_FLAG 0x00001000 // DC has all secrets #define DS_WS_FLAG 0x00002000 // DC is running web service #define DS_DS_8_FLAG 0x00004000 // DC is running Win8 or later #define DS_DS_9_FLAG 0x00008000 // DC is running Win8.1 or later #define DS_DS_10_FLAG 0x00010000 // DC is running WinThreshold or later #define DS_KEY_LIST_FLAG 0X00020000 // DC supports key list requests #define DS_PING_FLAGS 0x000FFFFF // Flags returned on ping #define DS_DNS_CONTROLLER_FLAG 0x20000000 // DomainControllerName is a DNS name #define DS_DNS_DOMAIN_FLAG 0x40000000 // DomainName is a DNS name #define DS_DNS_FOREST_FLAG 0x80000000 // DnsForestName is a DNS name
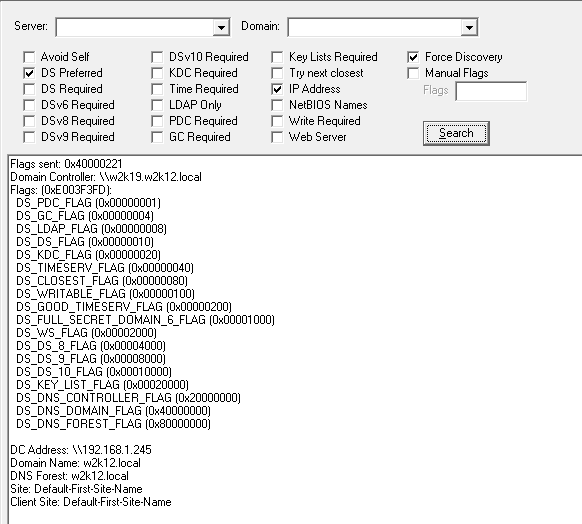
As you can see 0x20000 is defined in the include file as support for Key List Requests, see the Kerberos Protocol Extension [MS-KILE] section 2.2.11 for more info. NetTools includes this decode and the result from the same server shows the option for Key List Request are supported.
Also See