Admin Network & Security Magazine published a review of NetTools. It's now available on their website here: https://www.admin-magazine.com/Archive/2022/72/Active-Directory-management-with-NetTools
Category Archives: Basics
NetTools v1.32.0
AD Permissions Editor ![]()
Updated AD Permissions dialog to provide the ability to edit the permissions of an object. The edit option can be used in conjunction with the Effective Rights tab to model permission changes. See Permissions Dialog or How to edit an AD object's permissions.
Reports ![]()
This option is used to display the direct and indirect reports under the nominated User. See Reports
General
Added UAC detection at startup and warn if a restricted token is detected when running on a DC, as sthe DC may not return some data due to the restricted token. Replaced all instances of strcpy with strncpy to help prevent memory overflows. Better support has been added for Unicode characters not included in the current code page. For DNs that contain a Unicode character, the DN will be encoded as # hexstring, i.e. CN=#04044761C48D,DC=w2k12,DC=local.
AD Effective Permissions
A new capability has been added to the AD Permissions Browser and the Permissions dialog to show the Effective Permissions. In AD Permissions Browser, the Effective Permissions are shown while browsing the AD. See AD Effective Permissions for more details.
AD Permissions Browser
The trustee option was updated to automatically add Pre-Windows 2000 Compatible Access group based on the group membership.
Added option to export permissions.
Permissions are now colour-coded to reflect the permissions that have been granted.
Updated the Trustee option to include a pre-Windows 2000-compatible access group to the access token.
Updated Trustee select to display the object search dialog if the User is not found.
Updated the ACE flags to provide more details of the ACE.
Fixed bug where list contents are not cleared when switching between permissions tabs.
Fixed intermittent error when switching between DACL and Default Security permissions for Schema objects.
Additional caching has been added to improve performance when switching between permission types on the same object.
AD Permissions Reporter
Added option to include Authentication group.
Fixed new rule defaulting the scope selection.
Permissions Dialog
Updated trustee selection to include the option to use the current User's access token.
Added the Effective Rights tab to display the Effective Permissions of the selected trustee. See Permissions dialog
Updated to include SACL permissions
AD Properties Dialog
Updated LAPS tab to support both LAPS v1 and v2.
Update the function of Absolute checkbox to refresh the TokenGroup list when changed.
The account option is updated to show the status of the User who cannot change their password based on the object permissions.
Added a Permissions button to the dialog.
Updated the TokenGroup tab so it doesn't refresh each time it's selected.
TokenGroups now uses the Profile cache to improve name resolution performance over slow links.
Updated to handle attributes that can't be resolved or displayed correctly, due to Unicode characters.
Updated to support Unicode DN in DN-DN attributes - member, memberof, manager, direct reports
Added extra field on Objects tab to display UTF-8 encoded DN, is displayed for DNs that contain Unicode characters
Connection Profiles
Added option to specify the LDAP Protocol Version to be used for the profile. The default is Version 3.
DC Resolution
Updated LDAP and DS binds to use the connection profiles.
DirSync
Updated the cookie functionality so show changes if the cookie is subsequentially used.
DsGetDcName
Added additional options for Windows 2022 and an Advanced View to show the associated API constants for the options. Also updated the output to display the details of the flags passed to the API.
Error Messages
Updated LDAP Error messages to also return the Windows equivalent error message.
Export Permissions
added the option to export the permissions of objects from AD Permissions Browser and Permissions dialog
GPO Explorer
Updated the context menu so the Edit GPO option is available in the tree view and GPO list views.
Updating testing to show the results of the data capture phase if a single server is selected.
Updated the GPO list view to include who has been assigned the Apply GPO right.
Additional tabs were added on the Group Policy Object view to display the Policies and Default GPO permissions.
GPO Test, Updated logic so if sysvol is inaccessible then all sysvol tests reflect the failure.
Fixed an intermittent exception error on the Domain based GPO tests.
Update the tests to include additional testing of the permissions on both AD and Sysvol, and checks that the sysvol permissions are the same across all DCs
Added additional Sysvol test on individual GPO details to test and report on file permissions.
Added option to open and view the settings in registry.pol files.
Group Compare
Added a new membership compare option of Member Recursive, which will compare the membership of a group and all nested groups.
LDAP Browser
Fixed bug where user-selected decode types are not honoured.
LDAP Search
Updated the Manage Control dialog to allow the selection of Sequence encapsulated of the value, to provide better support for other control types. See details here
Fixed bug that could cause an exception when multiple Date meta data decodes are used
Added metav attribute decode for value based replication details contained in the msds-msDS-ReplValueMetaData attribute.
Added decode for UTCTime and change dynamic decode to select UTCTime for OID 2.5.5.11 and OMSyntax = 23.
Meta Data Dialog
Updated to support F5 refresh option
Object Count
Updated to support GC connections so the count can be completed across the entire forest.
Object Replication
Added context menu option called Move to Top as the first DC in the list is used as the source DC to compare the other DC against.
Organization Dialog
updated to include Organisation Structure in the context menu
Ping
Updated context menus to disable change option when tests are running.
Schema Versions
Updated to support LAPS v2, Exchange 2019 CU13.
Search
The Use With context menu updated to include an option to select Effective Permissions
Time Converter
Updated to support hex-based 64 bit time entries, i.e 0x1d99bfe7fb26dbd
ACL Viewer v1.9.4
This is a new version of ACL Viewer available under the other Tools section. This includes a number of update to improve the functionality and usability.
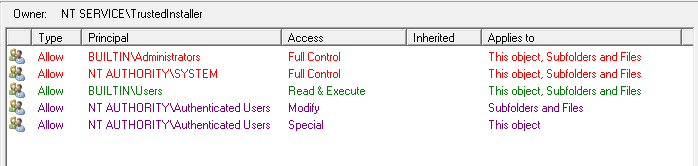
The Permissions pane now has colour coded permissions to help identify what permissions have been assigned. Red - for Full Control, Purple - for Change permissions, and Green for Read Permissions.
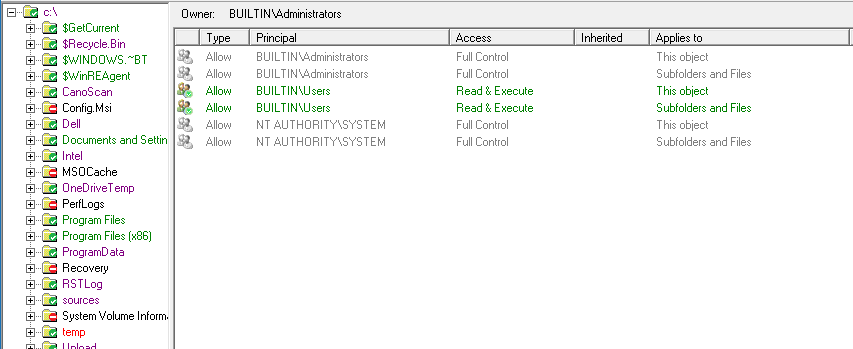
The Folders pane also gets a colour makeover, now when in Trustee Mode, the folders will also be colour-coded based on the permissions the selected trustee has on the folder. This makes it easy to see at a glance what permissions the trustee has.
Also while in Trustee Mode only the permissions that are for the selected trustee will have any colours, the permissions that are not assigned to the selected Trustee are shown as greyed out, as shown above.
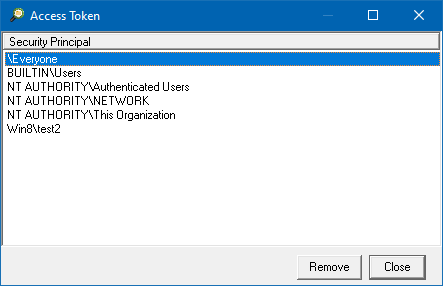
The Access Token dialog has also been updated to include an option to remove groups from the selected trustee access token. This will allow you to display specific permissions that have been assigned.
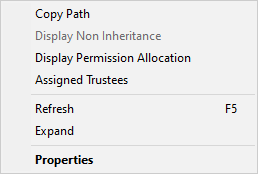
Another new feature is the Expand option on the folders context menu, this allows you to expand all the sub-folders under the selected folder.
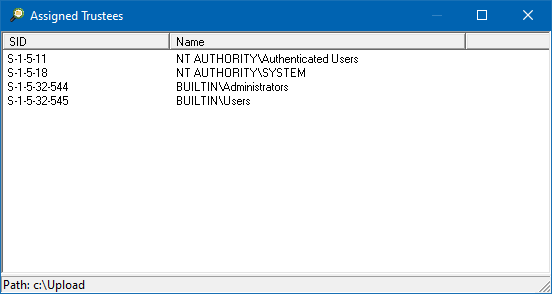
The final addition is the Assigned Trustees option on the folders context menu. This option will scan the select folder for all the trustees that have been assigned in the permissions in the path. This is useful when migrating servers to a different domain, and you want to know which groups are being used to access the folder structure, so they can be migrated as well. The option will display all the trustees that have been assigned permissions.
How to: Copy a user’s group membership
In this post, we will look at how to use NetTools to copy the group membership from one user to another.
To add or remove a user from a group, we need to make the changes on the group itself; the native AD tools hide this requirement to simplify AD management. NetTools is the same; it can make group changes on the user objects.
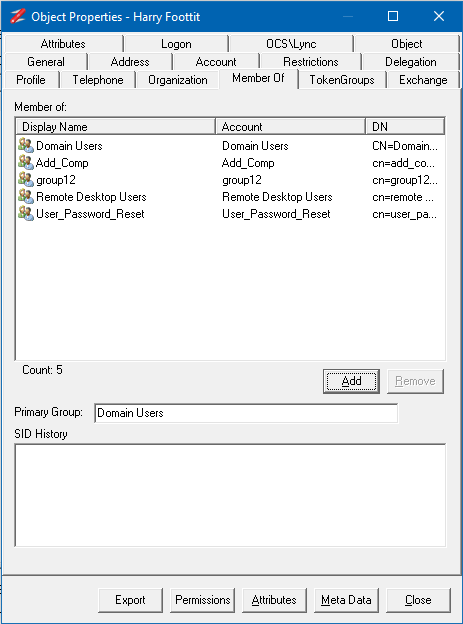
To copy the group membership we need to use the NetTools AD Properties dialog, to select the user's group membership you want to copy.
In NetTools, in the Quick Search, enter the user name you want to copy, and press enter.
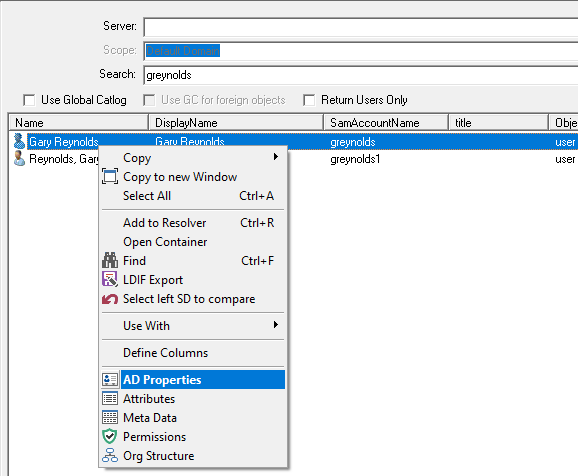
Right-click on the user you want to copy and select the AD Properties option from the context menu.
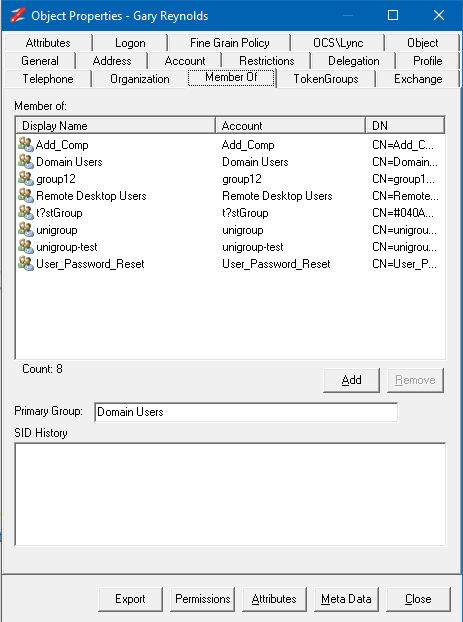
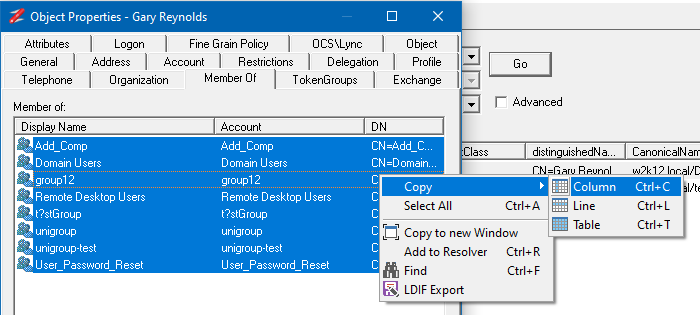
In the AD Properties dialog select the Member of tab, this shows the groups that the user is a member of.
Select all the groups, or the groups you want to copy and move the mouse over the DN column and right-click and select Copy->Column to copy the list of DNs for the selected groups.
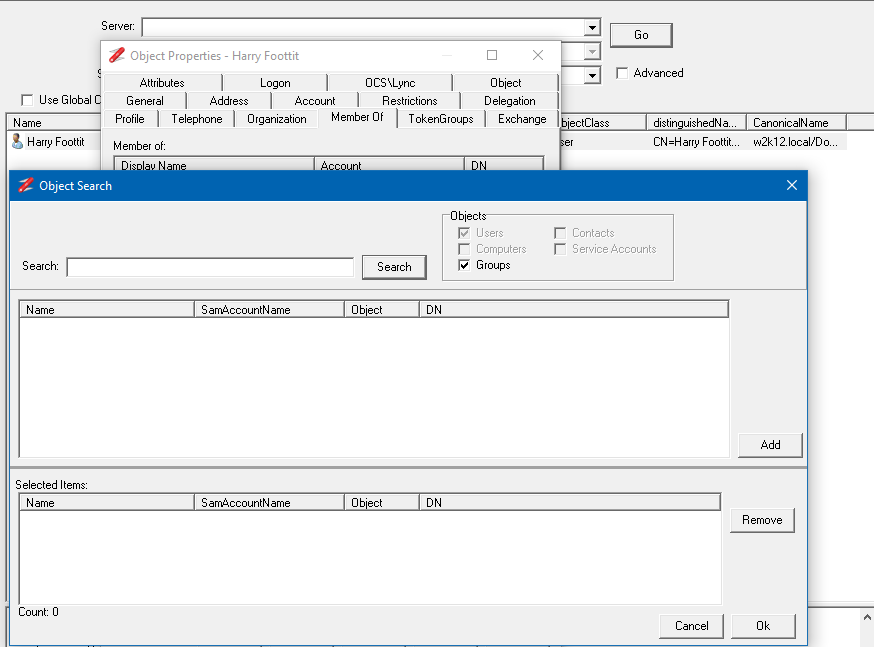
Using Quick Search, search for the user you want to add the selected groups too. Open the AD Properties for the user and select the Member Of tab.
Click on the Add button to display the Object Search dialog.
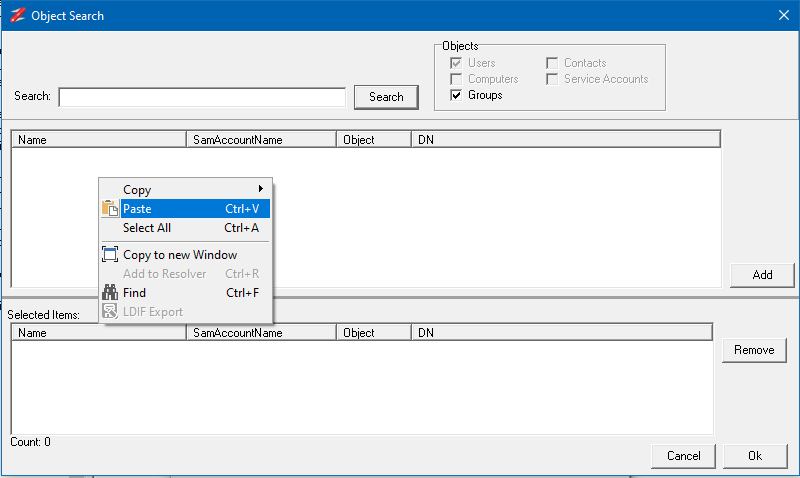
In the Object Search dialog, right-click in the top select and select Paste from the context menu.
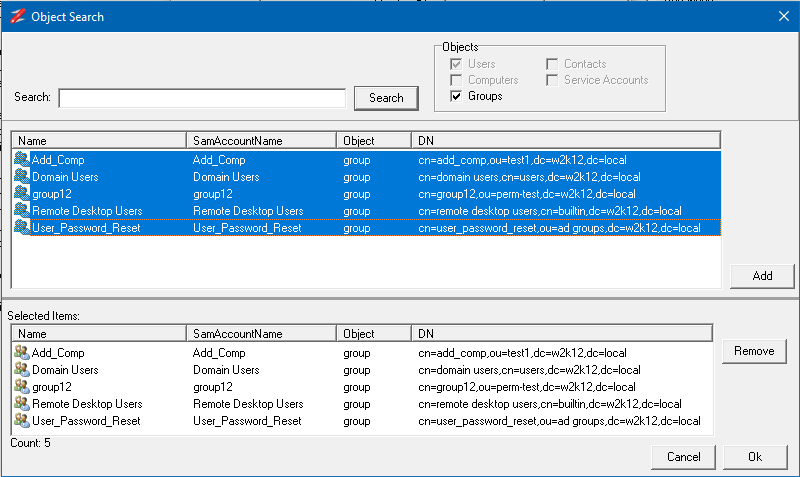
The selected groups will be displayed in the top sections. Now select all the groups and click on Add and then click OK.
The groups have been added to the user, and the membership is now updated.
GPO Explorer – GPO Test Details
Some of the Features and Tests listed here are only available in NetTools v1.31.4 and above.
The GPO Explorer Test feature provides similar functionality to the retired Microsoft GPOTool.exe utility. This post provides the details of the completed tests and how the results are compared to the other selected DCs.
The test feature appears in two locations in GPO Explorer, one as a tab on the individual policy details and the other at the domain level to test multiple GPOs simultaneously. While how the results are displayed is different between the two test types, the same testing is completed for both instances.
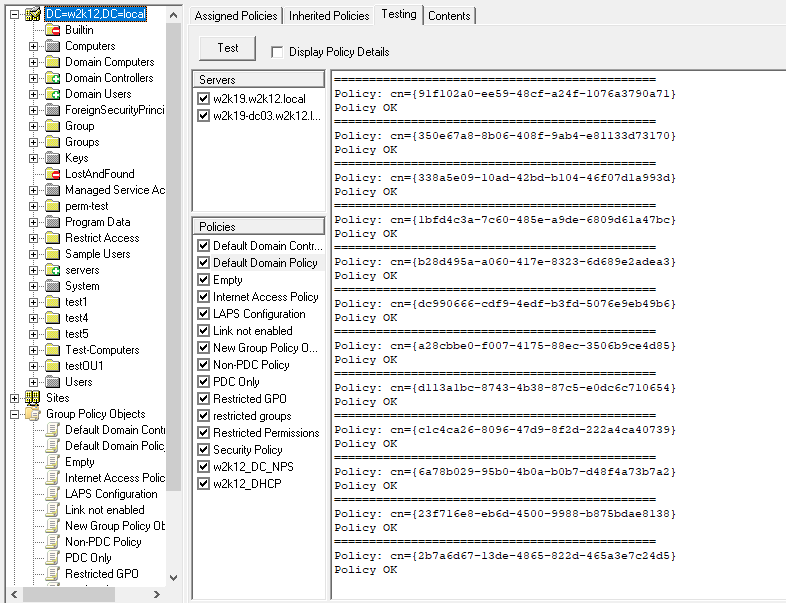
The Domain option looks like this and provides a very similar output to the retired GPOTool.exe.
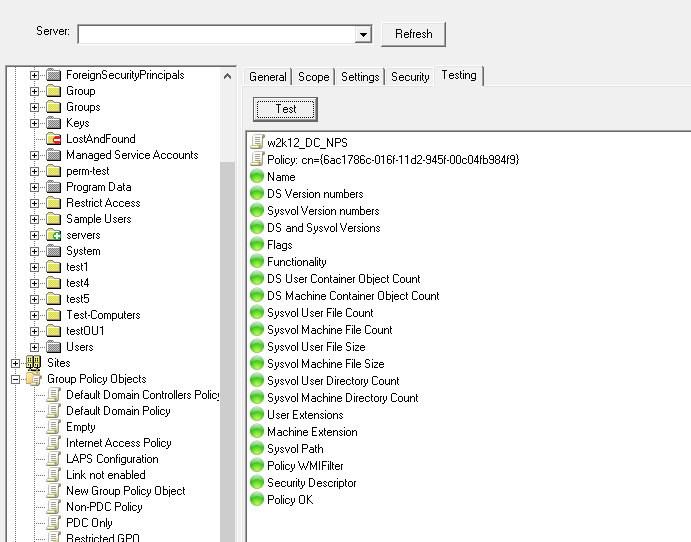
The individual test looks like this:
DC Selection
By default, the tests are performed against all the DCs in the domain. However, it's possible to define which DCs you want to include in the test. The Domain level test, as shown above, provides a list of DCs that have been discovered; you can limit which DCs will be included in the test by selecting as required DCs. This selection is then used for both the Domain and Individual tests.
Test Details
The testing is completed in two phases; first, the details are collected from each of the selected DCs, and then in phase two, the captured details are compared across all the selected DCs. The first selected DC in the server list is used as the source, and all the other DCs are compared against this DC; you can change this by using the context menu to move another DC to the top of the list, which will be used as the source DC.
During the Collection phase, the following details are captured and tests performed:
- Display Name of the Policy
- Sysvol Path
- Functionality Version
- GPO Flags
- GPO Version Number (User and Machine)
- WMI Filter assigned
- GPO Machine Extensions
- GPO User Extensions
- When Created
- When Last Changed
- AD Permissions
- Number of sub-AD objects under the GPO for both User and Machines settings
- Check the Sysvol path is accessible
- Capture the security permissions of the root of the policy folder
- Check that the trustees assigned Apply Group Policy right in the AD have access to the following location in the Sysvol path:
- The root of the policy folder
- GPT.ini
- User folder
- Machines folder
- Capture the GPO version details from the GPT.ini file (User and Machine)
- Capture the file count, total file size, and directory count for these sub-directories:
- Machine
- User
Once the details have been captured from all the selected DCs, phase two will compare each value to confirm the details are the same across all the DCs. If there are any differences, it will report an error, or the traffic lights indicators for the test will be Red. The Compare phase, in addition to comparing the details captured in phase one, will also complete the following tests:
- Compare the AD DACL ACE Count
- Compare the Sysvol DACL ACE Count
- Confirm the ACE in the Sysvol DACL are in the same order
- Compare the AD Security Descriptor
- Compare the Sysvol Security Descriptor
- Check for duplicate ACEs
- Check the order of the permissions
The Individual test option displays the results as pass\fail and doesn't provide much detail on the reason for the failure. However, the Domain level test provides details of the captured information and failure details when the Display Policy Details option is selected before running the test.
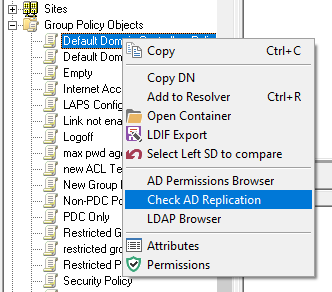
If any AD replication tests fail, you can select the individual GPO and use the Context Menu option to run a Check AD Replication test on the GPO AD object; this will automatically populate the Attribute Replication test for you.
Debug Option
The GPO test also provides additional debug information in the Domain level test, which is helpful if you are trying to diagnose ACL issues as reported by the GPMC Status report. This debug option is not enabled by default and can only be enabled by manually editing the NetTools.ini file.
- Open the NetTools.ini file
- Search for [SavedOptions]
- Add GPODebug=true after the heading
[SavedOptions] GPODebug=true
Mapping Get-ADTrust attributes to the TDO Object
This post provides the details of the mapping between the the attributes displayed by the Get-ADTrust powershell command and the attributes of the TDO object.
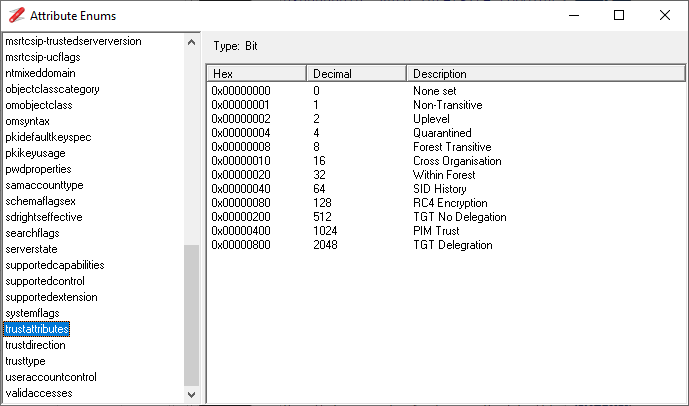
Most of the properties returned by the Get-ADTrust command map to the TrustAttribute attribute of the TDO object, so the table below shows which values of the TrustAttribute map to corresponding Get-ADTrust Property. The NetTools Mnemonic column has the name of the mnemonic that NetTools will display if this value is set.
| Get-ADTrust Parameter | TDO Attribute | NetTools Mnemonic |
|---|---|---|
| Direction | trustDirection | |
| DisallowTransivity | TrustAttribute | Non-Transitive |
| DistinguishedName | DistinguishedName | |
| ForestTransitive | TrustAttribute | Forest Transitive |
| IntraForest | ||
| IsTreeParent | ||
| IsTreeRoot | ||
| Name | Name | |
| ObjectClass | ObjectClass | |
| ObjectGUID | ObjectGUID | |
| SelectiveAuthentication | TrustAttribute | Cross Organisation |
| SIDFilteringForestAware | TrustAttribute | SSIDHistory |
| SIDFilteringQuarantined | TrustAttribute | Quarantined |
| Source | ||
| Target | trustPartner | |
| TGTDelegation | TrustAttribute | TGT Delegration |
| TrustAttributes | ||
| TrustType | trustType | |
| TrustedPolicy | ||
| TrustingPolicy | ||
| UsesAESKeys | msDS-SupportedEncryptionTypes | |
| UsesRC4Encryption | TrustAttribute | RC4 Encryption |
This table shows the NetDom command argument that is used to change the corresponding TDO attribute.
| Get-ADTrust Parameter | NetDom Parameter |
|---|---|
| Direction | twoway or oneside |
| ForestTransitive | Transitive |
| SelectiveAuthentication | SelectiveAuth |
| SIDFilteringForestAware | SIDHistory |
| SIDFilteringQuarantined | Quarantine |
| TGTDelegation | EnableTgtDelegation |
This page provides the details of the netdom command parameters, and this page provides the details of the TrustAttribute attribute. This page provides the details of the SID filtering functionality and which SID will be filtered.
The screenshot below shows the enumerate or mnemonics as defined on NetTools.
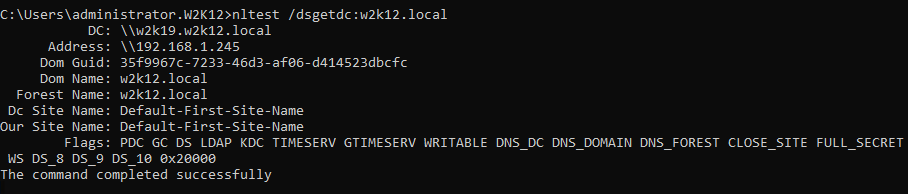
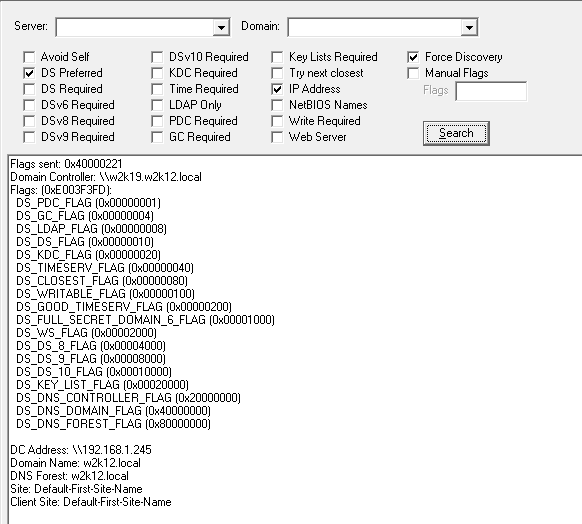
NLTEST Flags – what does 0x20000 mean?
When running NLTEST /DSGETDC command against a domain controller that is Windows 2012R2 or later, the command will display the normal flags plus an extra flag called '0x20000', but what does the 0x20000 flag mean. First of all it's not an error code, Microsoft have added an additional feature to Windows 2012R2 and later DCs, but NLTEST hasn't been updated to display this flag correctly, even the Windows 2019 version doesn't have this flag defined.
The results deplayed by NLTEST /DSGETDC is the information returned by the DsGetDcName API, this information if defined in the DOMAIN_CONTROLLER_INFO structure.
typedef struct DOMAIN_CONTROLLER_INFOA { LPSTR DomainControllerName; LPSTR DomainControllerAddress; ULONG DomainControllerAddressType; GUID DomainGuid; LPSTR DomainName; LPSTR DnsForestName; ULONG Flags; LPSTR DcSiteName; LPSTR ClientSiteName; } DOMAIN_CONTROLLER_INFOA, *PDOMAIN_CONTROLLER_INFOA;
The Flags member has the following definitions in the dsgetdc.h file
#define DS_PDC_FLAG 0x00000001 // DC is PDC of Domain #define DS_GC_FLAG 0x00000004 // DC is a GC of forest #define DS_LDAP_FLAG 0x00000008 // Server supports an LDAP server #define DS_DS_FLAG 0x00000010 // DC supports a DS and is a Domain Controller #define DS_KDC_FLAG 0x00000020 // DC is running KDC service #define DS_TIMESERV_FLAG 0x00000040 // DC is running time service #define DS_CLOSEST_FLAG 0x00000080 // DC is in closest site to client #define DS_WRITABLE_FLAG 0x00000100 // DC has a writable DS #define DS_GOOD_TIMESERV_FLAG 0x00000200 // DC is running time service (and has clock hardware) #define DS_NDNC_FLAG 0x00000400 // DomainName is non-domain NC serviced by the LDAP server #define DS_SELECT_SECRET_DOMAIN_6_FLAG 0x00000800 // DC has some secrets #define DS_FULL_SECRET_DOMAIN_6_FLAG 0x00001000 // DC has all secrets #define DS_WS_FLAG 0x00002000 // DC is running web service #define DS_DS_8_FLAG 0x00004000 // DC is running Win8 or later #define DS_DS_9_FLAG 0x00008000 // DC is running Win8.1 or later #define DS_DS_10_FLAG 0x00010000 // DC is running WinThreshold or later #define DS_KEY_LIST_FLAG 0X00020000 // DC supports key list requests #define DS_PING_FLAGS 0x000FFFFF // Flags returned on ping #define DS_DNS_CONTROLLER_FLAG 0x20000000 // DomainControllerName is a DNS name #define DS_DNS_DOMAIN_FLAG 0x40000000 // DomainName is a DNS name #define DS_DNS_FOREST_FLAG 0x80000000 // DnsForestName is a DNS name
As you can see 0x20000 is defined in the include file as support for Key List Requests, see the Kerberos Protocol Extension [MS-KILE] section 2.2.11 for more info. NetTools includes this decode and the result from the same server shows the option for Key List Request are supported.
Also See
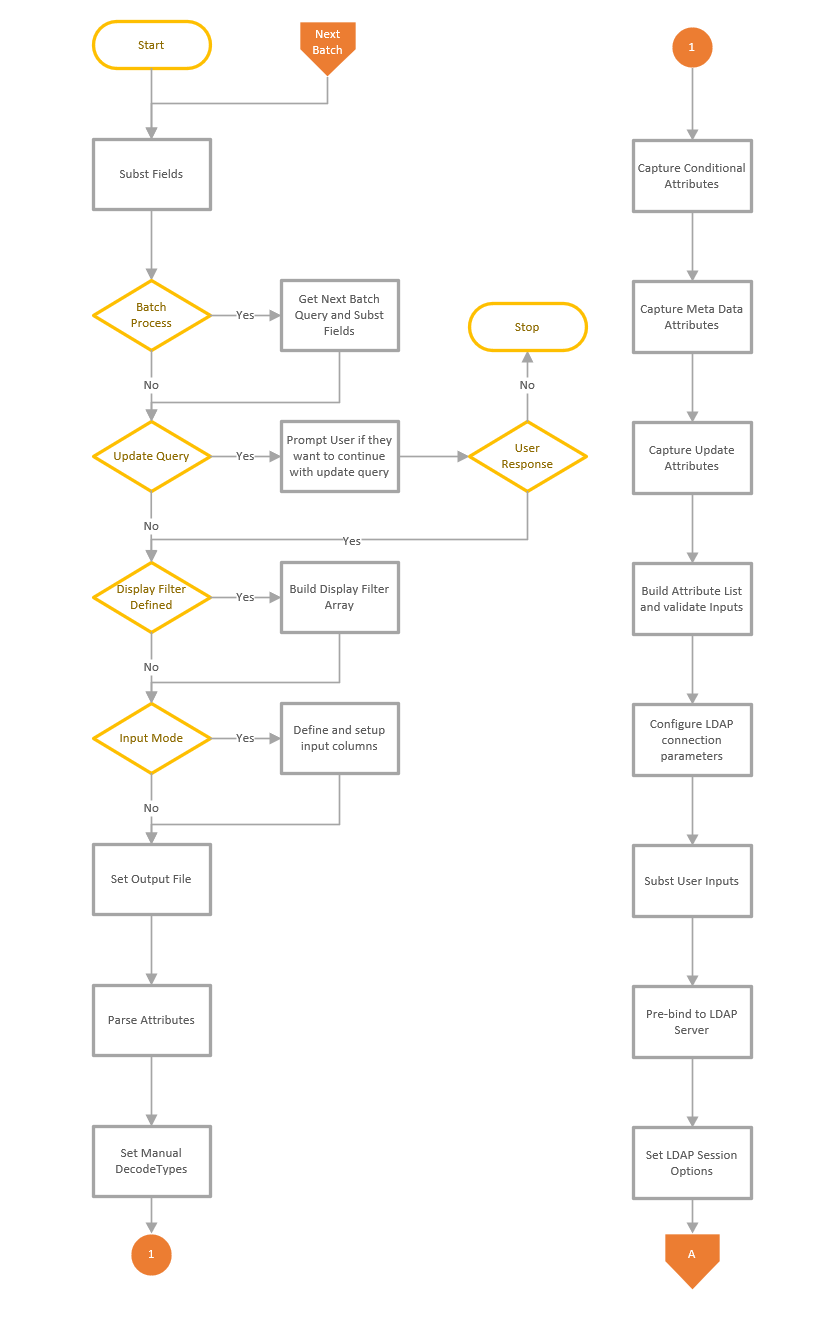
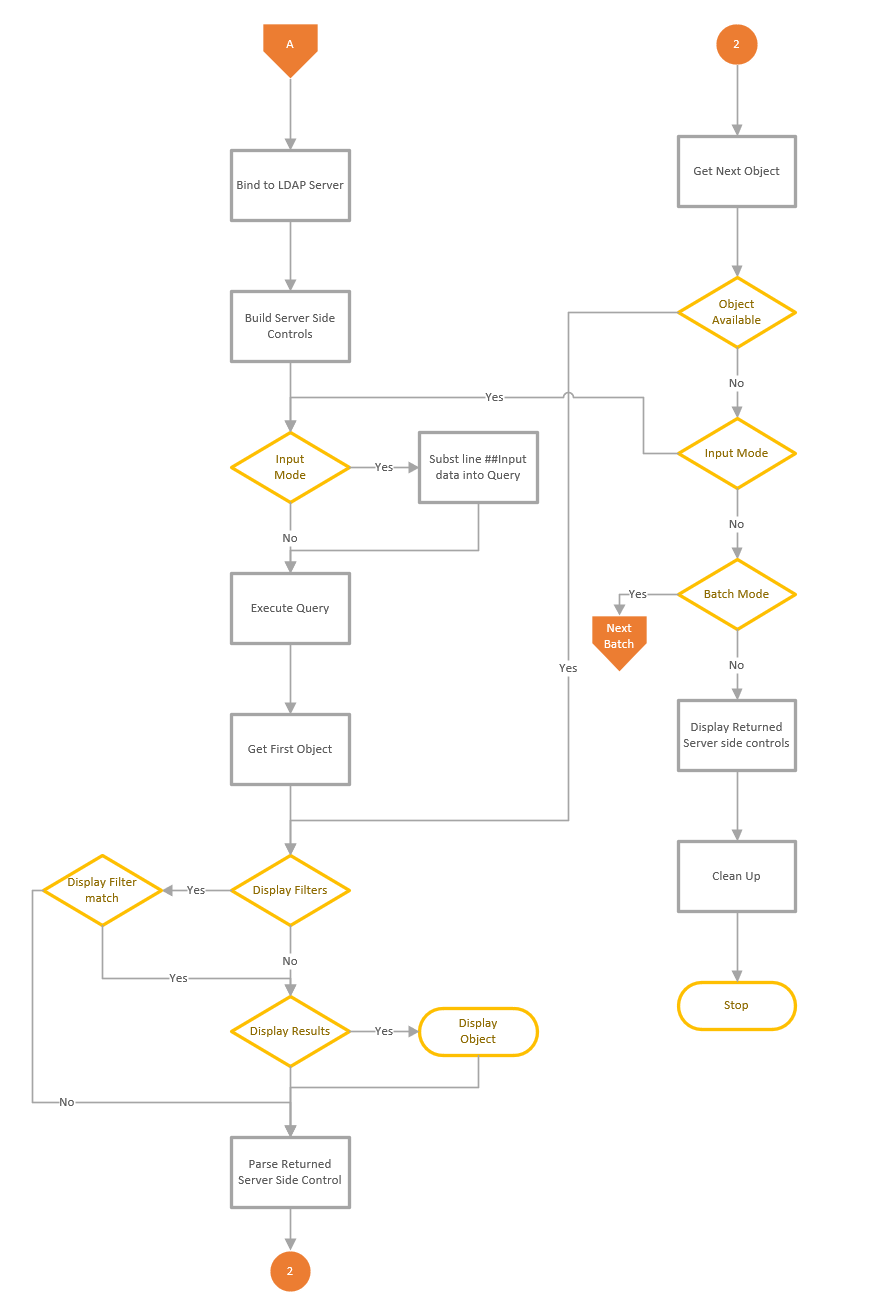
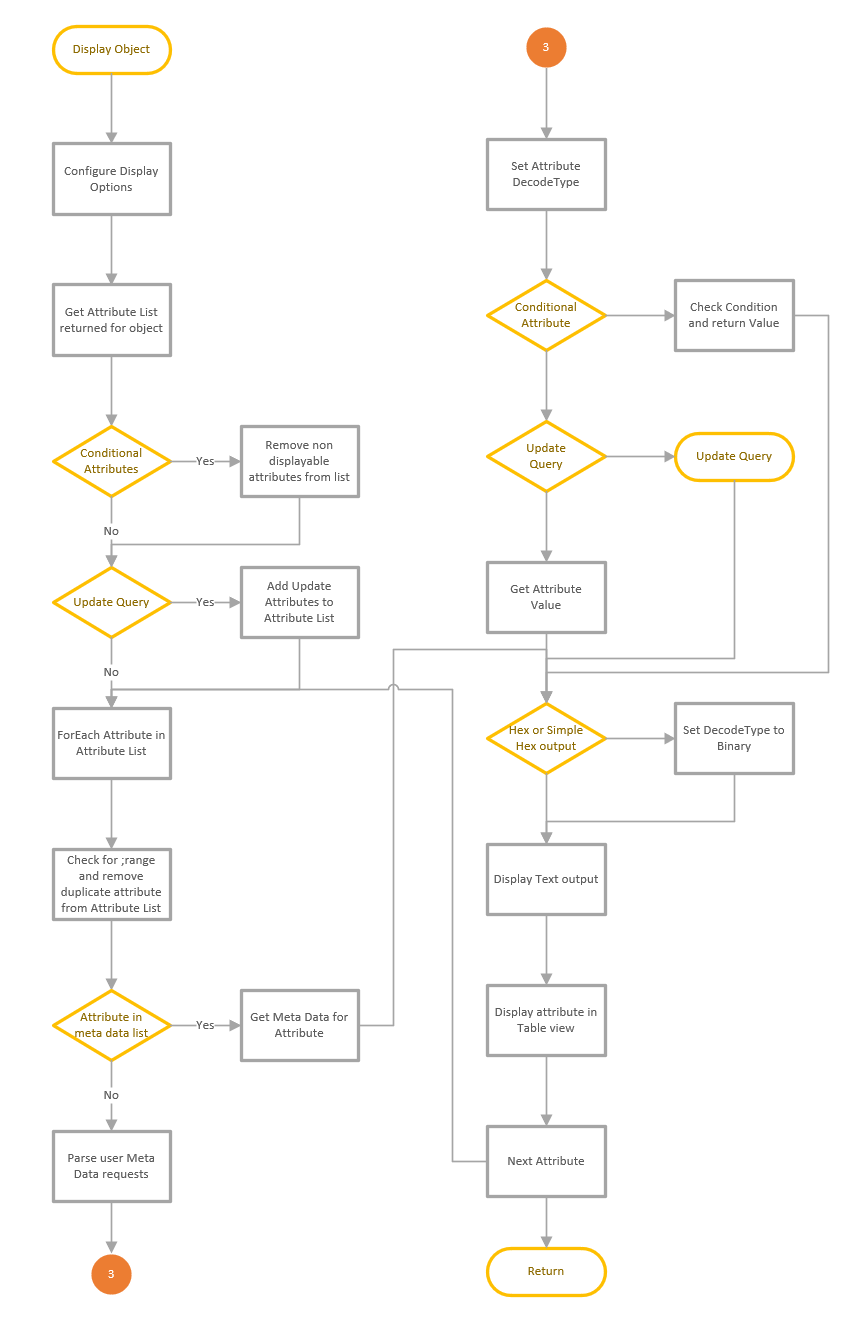
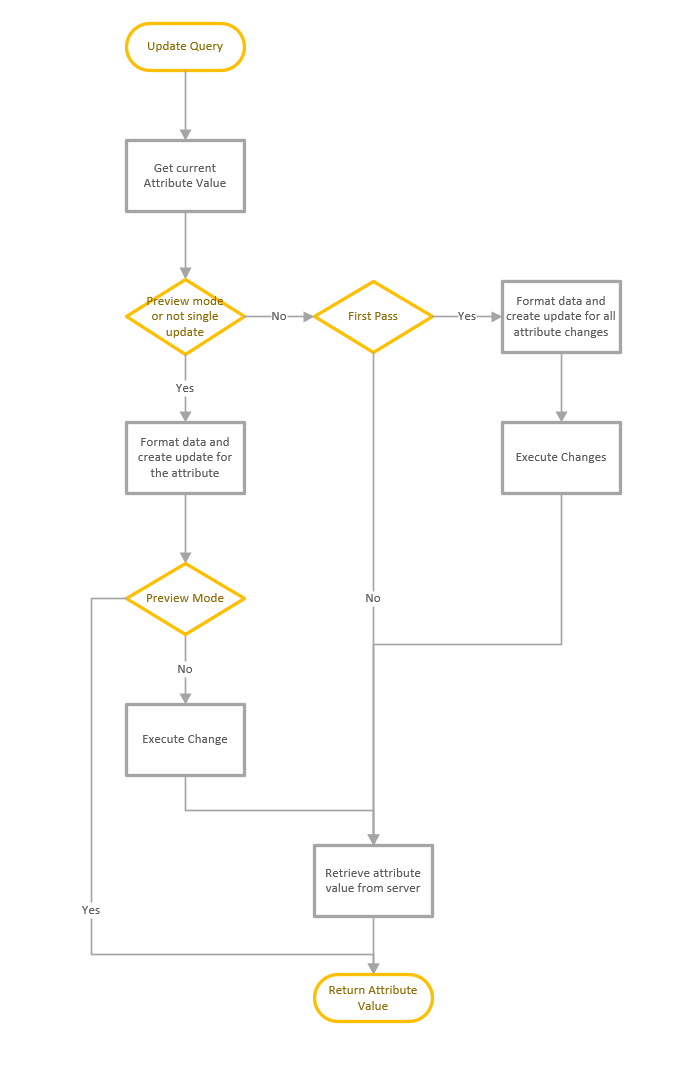
Process Flow for LDAP Search
This is a quick article that shows the process flow of the LDAP Search feature. The LDAP Search function consists of a number of functions that are used to execute the query and display the results. The main function is used to collect and validate the user inputs and connect to the server and execute the query, then a sub function is used to display the results and complete any attribute updates. The process shown below starts when the user presses the Go button to execute the query.
Invalid characters for Office365 Sync
Office365 specifies a number of characters that can't be includes in a number of key attributes. These invalid characters vary depending on the attribute, for a full list of invalid characters in each attribute see this Microsoft article.
NetTools includes a predefined query that will show which user objects contain these invalid characters. The query is called Users: Invalid characters for O365, which is available in the LDAP Search option. These are the attributes that are included in the search
-
-
-
- givenName
- sn
- mailNickname
- proxyAddresses
- UserPrincipalName
-
-
To run the query first select the LDAP Search Option in the left hand pane, then click on the Populate button, shown in the red square below, to connect to the AD and populate the Base DN field.
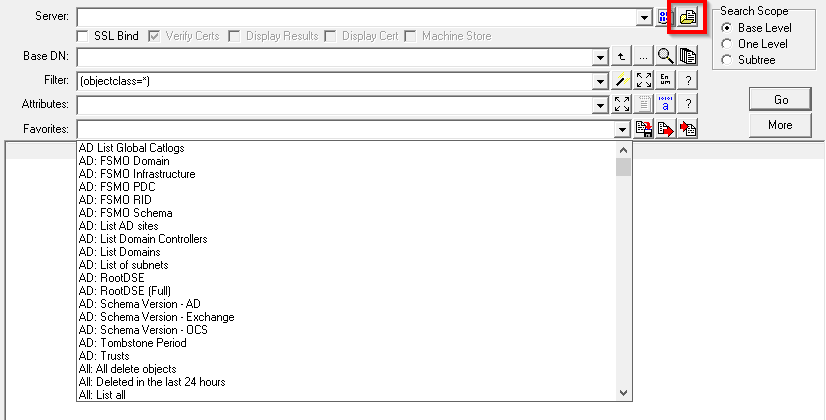
Once the Populate has finished, select the Users: Invalid characters for O365 query from the Favorites dropdown list. If required, change the BaseDN field to limit the scope of the search and then click Go. A list of all the user objects that contain invalid characters will be displayed.
The query uses the Regex Display filter option to only display the user objects that have invalid characters. Here are the the query properties:
[Users: Invalid characters for O365] Options=879892770722381 Server= BaseDN=##default Filter=(&(objectclass=user)(objectcategory=person)(!userAccountControl|=2)) Attributes=userPrincipalName, proxyAddresses;SMTP, givenName, sn,displayName,mailNickname, mail DisplayFilter=userPrincipalName regx [\"|,/:<>+=;?*'] || givenName regx [\"|,/:<>+=;?*'] || sn regx [\"|,/:<>+=;?*'] || mailNickname regx [\"|,/:<>+=;?*'] || mail regx [\"|,/:<>+=;?*'] || proxyaddresses regx [\"|,/:<>+=;?*'] Filename= Sort= Controls= Authentication=1158 Separator=,
For more information on the available queries see Redefined LDAP Queries
For details on the favorites option see Favorites
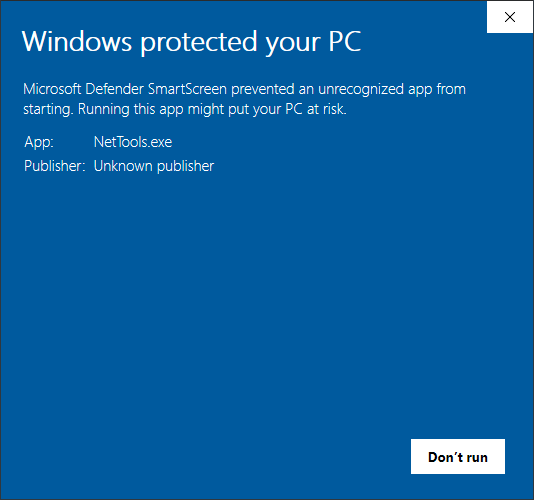
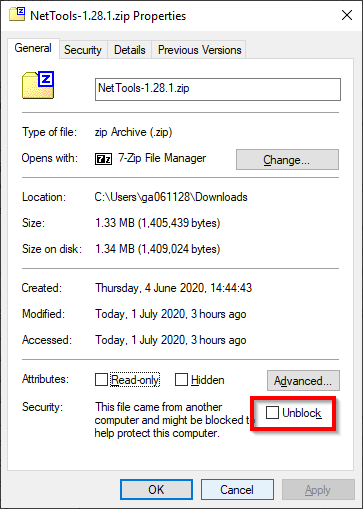
Workaround for SmartScreen
When running NetTools on a Windows 10 machine, it can sometimes trigger the Microsoft Defender SmartScreen and block the execution of NetTools. This is because NetTools is not signed and SmartScreen blocks apps that have been downloaded. This is an example of the SmartScreen dialog that is be displayed.
To prevent SmartScreen from blocking NetTools, open the properties of NetTools.exe and check the Unblock option and click OK.