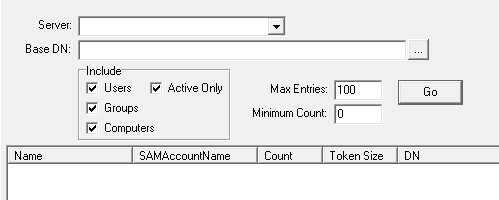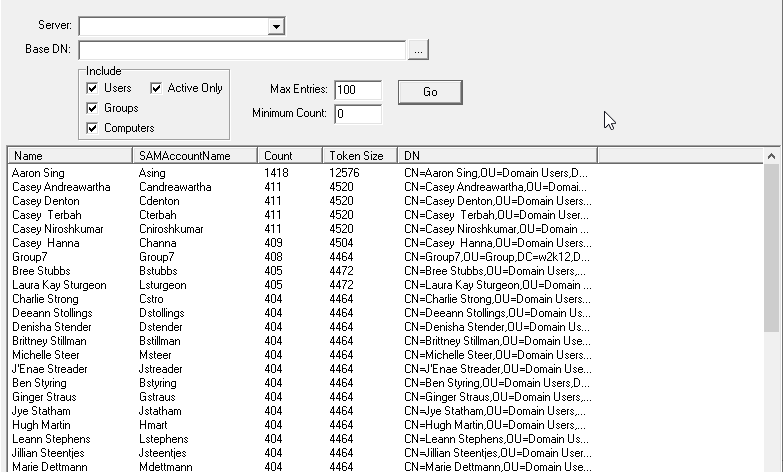
This option is used to report on the size of the access token of the selected security principals in the specified domain or OU. It shows an estimate of the number of SIDs that will be added to a user's or computer's access token when they authenticate against the domain, based on the TokenGroup attribute. The Base DN defines the starting point for the search, if it’s left blank, the entire directory is searched. There are also a number of options that can be used to limit the items that are returned, by default only the top 100 entries are displayed, however this can be increased or decreased.
Limiting the search to only Groups is a method to determine if there are any groups which have a high number of nested groups, which could impact the size of a user's access token if users are added to the group.
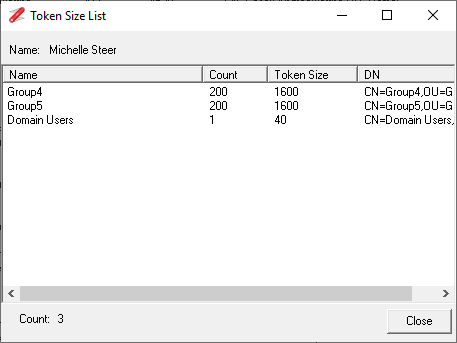
The Token Size column is for reference only, this is an estimate of the user's Access Token based on the details returned by the TokenGroups attribute for the corresponding object. The value in Token Size column is based on the Microsoft formula of 1200 + 40d + 8s.
The right click context menu provides a number of options to investigate the token size further, the Display SID Inheritance option allows you to drill down into the access token to see which items are potentially causing the token bloat. The Token Size displayed in the Inheritance dialog does include the 1200 byte overhead and is based on the formula 40d + 8s.
Background: Windows uses a static buffer to hold the user's access token, the size of this buffer varies in size depending on the versions of Windows, see: http://support.microsoft.com/kb/327825. While you can increase the size of the access token supported by the OS, there is no method to increase the maximum size supported by IIS prior to version 6. A user who is a member of 100+ groups they may experience intermittent access to resources hosted in IIS, over 300 they will have IIS\Sharepoint issues, over 1015 and the user will not be able to logon. The use of SID History for migration or consolidations only makes the access token size issue worse. This is quite a good white paper on the issue http://www.giac.org/paper/gsec/5111/kerberos-access-token-limitations/104962