Sometimes when troubleshooting complex issues it can be useful to dump the contents of the AD database, this can then be used to confirm an object exists, or to retrieve the DNT of an object, which will enable other troubleshooting activities, or just being a bit geeky and wanting to look under the hood.
In this post we will be looking at the RootDSE Modify Operations. There are a number of RootDSE Modify Operations that are available which provide advanced operations on the domain controllers. The full list of available modifiers is available here.
We will be looking at the DumpDatabase operator which allows us to dump the contents of the AD to a single text file. The dump file will be written to the NTDS folder on the domain controller. By default this is %systemroot%\NTDS with the file name of NTDS.dmp.
Note: as this is going to dump every object in the AD database, make sure you have sufficient space available on the volume hosting the NTDS directory on the selected domain controller before running this query.
By default the dump file contains the following fields:
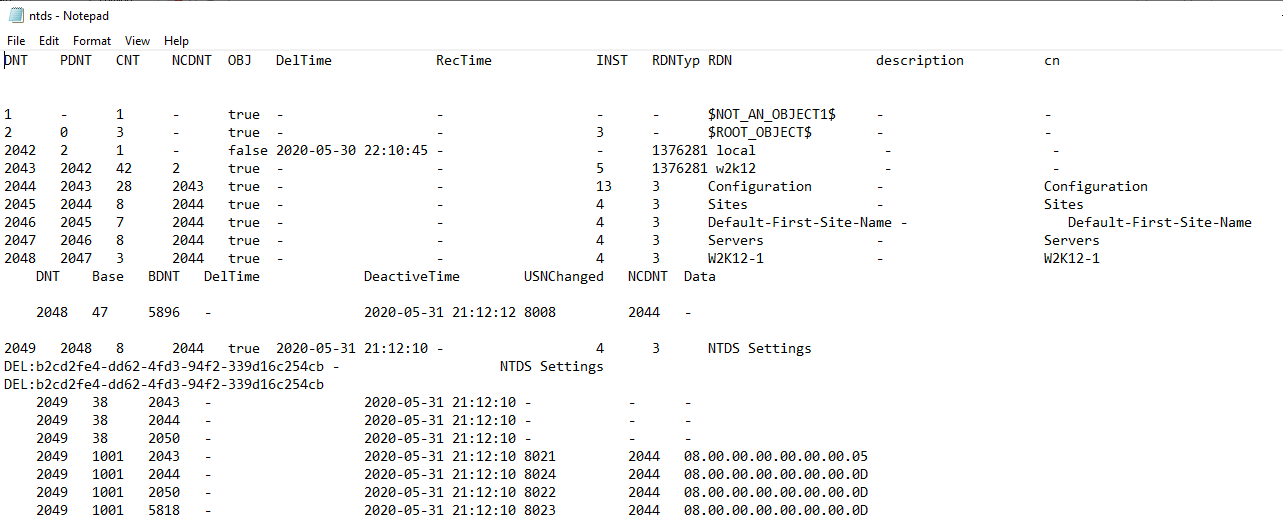
DNT PDNT CNT NCDNT OBJ DelTime RecTime INST RDNTyp RDN
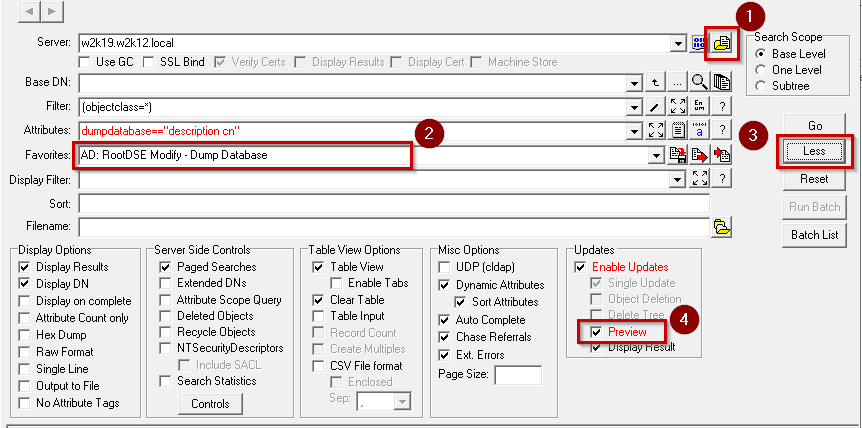
We can also specify additional attributes to be included in the dump file, however some security sensitive fields can't be included i.e. passwords. We are going to use one of the NetTools predefined queries to complete this task. This task can be completed on the domain controller itself or executed remotely, you just need domain admin rights on the domain controller to run the query.
In NetTools select the LDAP Search option in the left hand pane under the LDAP section
As the AD database dump query is an update query we need to complete a few extra steps to run the query:
-
-
- Click on the Populate button
- Select the AD: RootDSE Modify - Dump Database from the list of Favorites
- Make sure that the BaseDN field is blank, to write to the RootDSE
- Click on the More button to display the more options
- Uncheck the Preview option
- Click Go
- Confirm that you want to run the query
-
Once the query is complete the ntds.dmp will be created in the NTDS directory on the domain controller specified in the Server field. The query is configured to include the description and cn attributes in the dump file, you can specify additional attributes if required, the entry in the speech marks on the Attributes field needs to be updated with a space-separated list of attributes. If a security sensitive attribute is specified the dump file will contain an error message that the attribute was not found.
One of the limitations of the database dump, is that it will limit the number of characters that are returned per field, so if you are trying to dump the contents of a long binary field i.e. NTSecurityDescriptor the field will be truncated.
Here is a sample of the database dump: