In this post we will look at how to delegation the restoration of deleted objects using the AD Recycle Bin.
First we need to enable AD Recycle Bin, this is enabled by default on newly built forests with DC of Windows 2012 and above, for older forests all the domain controllers must be Windows 2008 R2 and above and you will need to run this command from a PowerShell command prompt to enable AD Recycle Bin:
Enable-ADOptionalFeature 'Recycle Bin Feature' -Scope ForestOrConfigurationSet -Target <your domain>
By default only domain administrators have the rights to restore object that have been deleted, the following steps will delegate the ability to restore deleted objects to the members of the "Restore_Objects" group.
1. Create an new AD group called 'Restore_Objects', the group can be a local, global or universal depending on your requirements
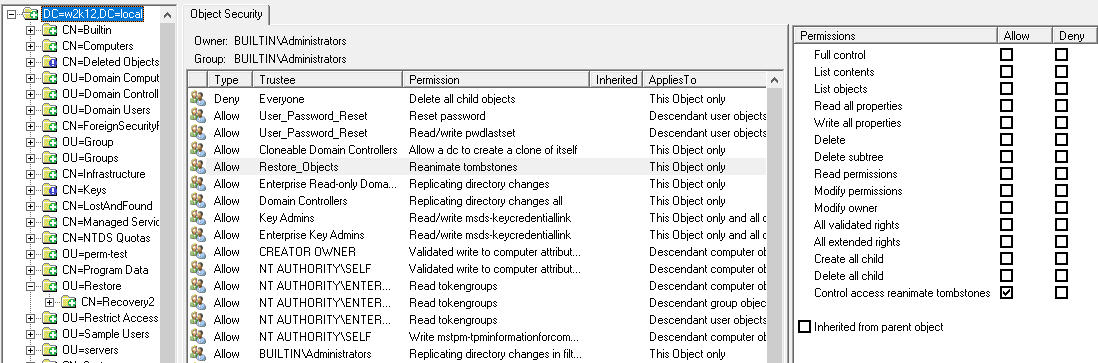
2. Next we need to set restoration rights on the root of the domain, open a command prompt with Run As Administrator rights and run the following command:
dsacls dc=<your domain>,dc=<com> /g "restore_objects:ca;Reanimate Tombstones"
3. To be able to change the security on the Deleted Object container, we first need to take ownership of the container, from the same command prompt run the following command:
dsacls "CN=Deleted Objects,dc=<your domain>,dc=<com>" /takeownership
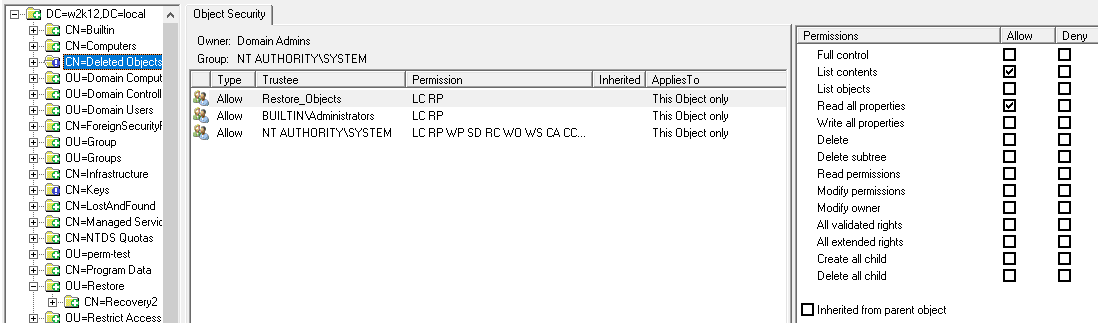
4. Now we are owners of the Deleted Objects container we can update the permissions, first we will assign the delegation group the rights to list the contents of the Deleted Objects container and read the properties of the objects using the following command:
dsacls "cn=deleted objects,dc=<your domain>,dc=<com>" /g "restore_objects:LCRP"
The permissions set so far provide the Restore_Objects group with the rights to restore objects and view the contents of the Deleted Objects container. However, they can't restore objects yet, they also need write permissions to the properties of the objects that have been deleted in order to be able to restore them.
Depending on your requirements, you can assign the properties permissions at the root of the domain so the Restore_Objects members can restore any deleted object in the domain or you can limit the delegation to a particular OU or object type.
This is the command to assign the required permissions
dsacls "ou=<your ou>,dc=<your domain>,dc=<com>" /I:T /g "restore_objects:WPCC"
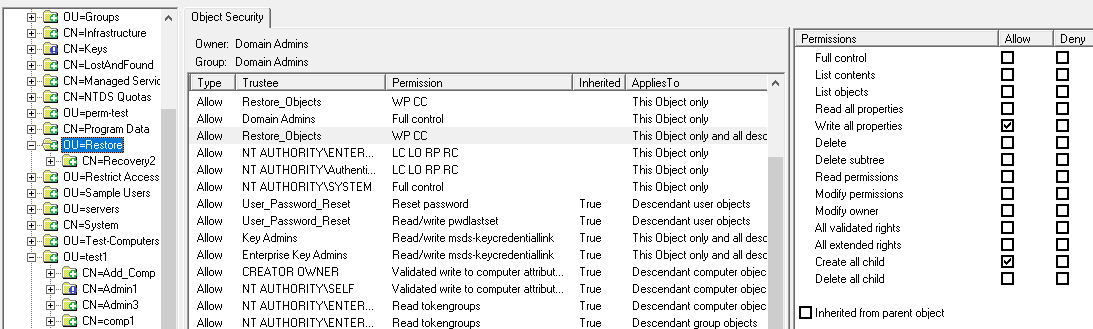
This shows the permissions assigned at the OU level:
In this case the members of the Restore_Object group, will be able to see all the of the Deleted Object but will only be able to restore the objects that were deleted from Restore OU, unless they have been assigned Write All Properties (WP) and Create Child (CC) rights through other permissions.
To restore objects you can use the Restore Objects option in LDAP Browser, see How To Restore AD Deleted Objects for more details.